As many readers and followers will know, I’ve had a bit of fun with scammers in the past. Remember those guys who call you up while you’re sitting down for dinner and tell you your computer has all sorts of nasties in it? Yeah, those guys.
The blog posts I’ve made have been part of the story and inevitably the one most people are familiar with, but there are a few other things happening which I think some of you would be interested in, particularly as it helps understand the bigger picture.
The catalyst for this post came after getting some good airtime last week. One thing that can be easily done and has a very significant impact is to raise peoples’ awareness (stick around – I’m going to ask for some help with this). Last week I was interviewed by Today Tonight (a national Aussie current affairs show) which aired at 6:30pm on Friday. I don’t know exact viewer numbers, but I assume its seven figures. Here’s the video (click through to their website):
As a result of that show, numerous people realised they’d been had and promptly cancelled payments. I’ll come back to some examples of this shortly, but first, let me try and shed some light on the tactics these guys are using as its a little cleverer than what many people are giving them credit for.
Understanding social engineering
One of the things I often hear is “Wow, you’d have to be stupid to fall for that”. By the same token, people who do fall for it often talk about how foolish they feel. The latter may be true, the former is not and that’s because this is a case of very clever social engineering. Let me explain:
When we talk about security in the digital age, we (myself included) usually talk about system security. Cryptography, SQL injection and cross site scripting are all essential concepts to understand when building secure systems but they’re all easily trumped by social circumvention:
Why are social engineering attacks so successful? It isn’t because people are stupid or lack common sense. But we, as human beings, are all vulnerable to being deceived because people can misplace their trust if manipulated in certain ways.
The social engineer anticipates suspicion and resistance, and he’s always prepared to turn distrust into trust. A good social engineer plans his attack like a chess game, anticipating the questions his target might ask so he can be ready with the proper answers.
One of his common techniques involves building a sense of trust on the part of his victim. How does a con man make you trust him? Trust me, he can.
Let me try and illustrate how this scam gains trust then uses it to exploit the victim. It breaks down into six phases and you’ll see the same six phases in every one of these virus scams:
- Establish credibility: The scam always begins by the caller claiming to represent Microsoft. They’re the “Windows Support Department” or the “Official Partner” or sometimes just Microsoft themselves. The scammer also claims that you have a Windows computer and more often than not, this will be correct. They’re also calling the victim on their home number at an hour where they’re usually relaxing – they’re in their comfortable zone and not as alert or as suspicious as they’d normally be.
- Create a sense of urgency: The scammer then moves on to making sure the victim sits up and pays attention by creating a sense of urgency. Usually this is along the lines of “We’ve just been notified that your PC has a virus” or “We’ve received an alert of malicious activity”. This obviously needs immediate attention and given the scammer has already established credibility, there’s no reason not to believe them.
- Instil fear: This phase is needed as the fear is what the scammer will later capitalise on. They’ll talk about all the nasty things the virus or malicious files will do to your computer and your personal data. It’s this fear that will cause the victim to begin throwing caution to the wind.
- Give the victim back some control: Urgency and fear themselves are not sufficient though, to really drive the point home the scammer helps the victim see the “viruses” for themselves. This is where the scammer directs the victim to the event viewer where perfectly innocuous warnings and errors are explained as being malicious activity.
- Create relief and gratitude: This phase involves two discrete tasks: Firstly, the scammer takes control of the PC. Strictly speaking, the victim hands over control using LogMeIn but of course by now they have been well and truly conditioned and have no reason not to let the guy who is going to save them in. Next the scammer “fixes” the problems which can mean anything from running free software such as Advanced System Care from IObit or even just deleting system files which they claim to be viruses.
- Commercialise the scam: By now the victim has been convinced they’ve been “saved” and are happy to pay the scammer for services rendered. The fee will differ, but usually it ranges from $150 to several hundred dollars which includes “ongoing support”.
When you look at the scam in this light – as a carefully crafted social engineering exercise – that position of “how stupid do you need to be to fall for this” quickly changes. What might also help you understand more about this scam is hearing from the people who’ve been stung by it so let me share a couple of stories.
Nigel in the UK
Although I have permission to reproduce these messages, I’m going to change the names of the individuals. Other than that these are entirely original, legitimate real world accounts from victims of the scam.
In the first case, because he’s in the UK, that means he’s Nigel (he’d be Bruce if he was an Aussie!). Nigel wrote to me last week after getting a bit suspicious and finding my blog:
FYI, I'm not, (or at least I didn't think before today), the kind of person who would fall for this kind of scam. However, as I said in my post, they only got to me because I had just reported a broadband fault and I was awaiting a reply from my ISP, (British Telecom).
The phone rang some fifteen minutes after putting down the phone from the BT call centre, (in India). A man said he was ringing about my “computer problem”, which I mistook for the call-back from BT.
Why did I let him gain remote access? Well the clever part of this scam is that they point you to Windows logs which have alarming looking symbols alongside the log entry, which are all reasonably benign. They then hype-up this “threat” using some pretty impressive sounding, (for us non-professional PC users), threats and then they are in.
Once in, they must deposit some bogus files on your machine, as the files/logs they showed me, are nowhere to be found now.
The thing that makes me even more mad, (at myself), is that I was constantly rebutting their bulls**t. For example, I asked why all the entries in the log they were showing me, (to prove I was being hacked…and I suppose I was), had the same date and time stamp. He just said “Oh that’s because you hadn’t downloaded the error log until today and that’s why”. I failed to ask him the $64K dollar question however, "Who told you to call me"?
I also asked, “Why am I paying you to eradicate these files? I can just shut down my machine and run my virus protection software and malware detector”. He then, (again), gave some pretty impressive sounding, (to me at least), reasons why this would not work.
He wanted me to pay via Western Union but I said I wasn’t happy with this and wanted to use Paypal, which I did. I have contacted Paypal but they just threw up the security “gates” on my account but promised to do nothing about the scammers as I had allowed them to gain access to my machine, of my own free will. Which is fair enough I suppose.
I did watch what he was doing on my PC remotely and nothing seemed particularly malicious, although I am now in a state of panic in that he got enough info from my machine to instigate some form of identity fraud.
The ”end” came when I saw him uninstall AVG, (which I have re-installed BTW), and install the free copy of Malwarebytes. This was something I could do, (obviously), so I asked him why this standard piece of software was being used, for this irremovable “clean-up”? He gave some reason, made his excuses and said he would be going and that I should just leave Malwarebytes running until finished. He then disappeared.
I have now changed all the passwords on all my online accounts, from message boards to my bank. I am still debating whether or not to contact my credit card company. Although all those passwords have been changed, I am fearful that they could have somehow got hold of my credit card number, end date and security digits from my machine. I have also contacted British Telecom to tell them what happened. I am highly suspicious that minutes after I hang up from an Indian call centre, I get an unsolicited call…from another Indian call centre. At least BT will be made aware but naturally, this will all be speculative and un-provable.
Finally, your blog has supplied me with a few answers and a great deal of cold comfort, so thanks for that. I now intend to warn as many people as I possibly can, as my technical penance for being so stupid as to fall for a scam like this.
The thing I really want people to take away from this is that Nigel is clearly articulate and would, under any other circumstances, normally exercise more caution. Note also how the scammer is persistent in the face of a challenge, always ready with an answer to the typical concerns a victim would raise.
Of course the other concerning behaviour is the removal of legitimate security software such as AVG. Once the scammer follows up by installing the free version of Malwarebytes (also legitimate but equally, probably unnecessary), they have “saved” the victim and have now performed a service they can capitalise on.
But there’s a silver lining to this one and it illustrates how valuable the awareness campaign is:
Some good news. Paypal came through and stopped the payment to the scammers!
I know this for sure, as I got a call a few minutes ago, (0915 UK), from the scammers complaining that the payment had been stopped.
This gave me an opportunity to vent my spleen. I have to say they were still very persuasive, "I'm going to lose my job" and "You're the cheat, not paying for services rendered", etc. However, once bitten twice shy and this time, not only did I ask some pertinent questions of my own but it also gave me the opportunity to inform them that I had changed all my passwords, bank details, etc. I have also registered with Experian (a credit check company) who have an identity theft watchdog and insurance scheme. It's £7 a month but what price peace of mind?
Once again, I have to thank you and your blog. The video of your interaction with the scammers took my breath away; such was the identical "modus operandi" with my case. It was your blog that galvanised me into action, to contact Paypal. I was, (up to that point), still dithering as to whether these people were legitimate or not.
Great news for Nigel, but it also shows the gall of the scammer; even after they’ve been caught out, they have the hide to call him back to try and retrieve “their” money. Amazing!
Now as it turns out, Nigel has since had his credit card used for a fraudulent Skype purchase, right after the scam was pulled off. This wasn’t Nigel’s Skype account and his bank actually raised this with him as part of their fraud detection process. Unfortunately Nigel had stored his credit card details – along with a number of passwords – in an unencrypted file on his desktop. Of course the bigger concern this raises is that not only are the scammers stealing cash for “services rendered”, they’re also stealing personal files. The damage that could be done with the sort of information that most of us have in digital format somewhere or other is limited only by the imagination.
This is really important and goes well beyond the (comparatively) minor inconvenience of just losing a few hundred bucks; scammers are using the access they gain to steal personal information from their victims.
Nancy the pensioner
This case is probably more the demographic you might picture as normally succumbing to computer fraud, but Nancy is not your average elderly computer user. Read on:
My name is Nancy, I am 71 years old and a self taught computer user. I sent you a message on facebook and suddenly this email came up on my screen, so here I am again.
After watching the program and seeing you at your computer I realized that this mob and scammed me a few days ago. They were really good convincing me that I had a problem and that they could fix it. All the information they gave me sounded very legitimate so dumb me went for it. Even took up their offer of a lifetime service of windows with a pensioner discount. Cost $230. They gave me an Adelaide number –
08 72001191 to ring if I had any problems.
Since seeing you on TV I have cancelled my credit card telling the bank of the scam. Not sure whether in time to stop the payment.
After hearing you I am very scared and am not sure what to do next. Do I go to the police? Consumer affairs? Find a computer technician? Can anything be done to stop future access?
Can you please give me any advice? Quite happy to pay you a fee if you can help. I am situated in a suburb of Newcastle. My phone number is [redacted]. Or reply by email.
Anything you can do to help me would be truly appreciated.
I gave Nancy a call yesterday and we spoke for about 40 minutes. She had actually just submitted an error report to Microsoft (you know the ones – an app crashes then asks you if you want to send anonymised data to MS), so she naturally drew the conclusion that the two events were linked.
During the scam the attacker went to great lengths to cleanse the PC of viruses – they even ran “defragler”, as she referred to it. Then, after she paid for the service and saved the credit card receipts locally, they deleted them. They then instructed her to leave her PC whilst they continued “fixing” it and not to worry, they’d shut it down when they were finished. They never did shut it down so Nancy called the number she sent me and left them a voice mail. This is how they responded:
with due respect ,we apologize to you for the inconvinience from us.Actually your laptop was not shut down because,our engineers were still working on it.But no worries sir,,your service has been completed.
And regarding those payment receipts,your receipts got removed automatically while the junk files were removing,,but don't worry,
we will soon sen you the receipt copies.
Bastards. This was sent from customercare.sol1@gmail.com. Google indexing, do your thing! The thing is that Nancy is quite adept at using the PC and in our discussion frequently demonstrated a good awareness of many concepts that would be foreign to most audiences half her age. Nancy simply succumbed to a clever social engineering scam and is now in the process of attempting to recover money and secure her PC.
The best defence is awareness
This is actually a bit disheartening, but to date, nobody has actually been able to do anything concrete to stop the bastards running these scams. And I do mean bastards plural as well; this is not just one organisation.
I’ve tried contacting the payment gateways I’ve seen used – no response. I’ve had a number of discussions with LogMeIn via both email and phone (their software is the one I’ve always seen used to remotely control the PC), but clearly they are too concerned about the impact on legitimate customers to place a warning on their site. I’ve had discussions with AusCERT and (indirectly) with the Australian Federal Police but because the scams originate overseas, it’s outside their jurisdiction (hopefully the last one I recorded will be an actionable exception).
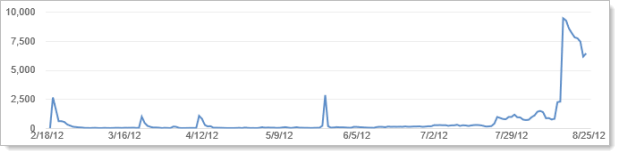
But one thing that has actually worked really, really well lately is YouTube. I now have four videos up there and the longest one – Scamming the scammers – catching the virus call centre scammers red-handed – now has 130,000 views (this is a 1hr 22min video for crying out loud!). They’ve also remarkably increased in recent weeks (this is views per day):
The comments from these videos are telling and tend to break down into three different categories:
- Racial abuse: Yes, the callers are usually Indian and unfortunately many YouTubers take that as a reason to go to town on the culture as a whole (note to self – don’t look to YouTube comments for maturity and insight!)
- Amusement at scammer misfortune: I get this one – seeing someone sticking it up a scammer then watching them try to worm their way out of it is entertaining(clearly I think so!)
- Reports of being scammed: A lot of people find my videos and blogs after having been scammed themselves. Often it’s only after seeing this material that they fully realise they’ve been had.
All told, those four scammer videos on YouTube have about 170,000 views plus the blog posts are running at about 70,000 views so the issue is getting plenty of eyeballs on it. The great thing about this is that it’s nothing more than digital word of mouth and probably a bit of the viral nature of YouTube.
Plus of course there’s the Today Tonight episode I mentioned so all told I’d like to think that we’re somewhere into the millions of people that have been exposed to this scam. But clearly that’s not enough as this rort continues and the people behind it keep snaring new victims. More awareness is needed…
Please share generously
Share this post. Share previous posts. Share the videos. It doesn’t matter whether it’s my content or someone else’s; just get the word out there. Hopefully the earlier info on social engineering and victims’ stories helped demonstrate that you don’t need to be stupid to fall for this scam nor do you need to have no idea about PCs, you just need to be vulnerable to clever social engineering – and that’s all of us.
Many of you reading this will already be aware of the scam or will be more technically inclined and less likely to fall for it; but you know people who are more likely to be victims. Less computer savvy people or simply people who are more likely to take a position of trust in their fellow man. These are the people you need to help educate primarily for their own sake but secondarily, if you are a technical person, you know who they’re going to turn to if they do get scammed!