I went to Helsinki a couple of years ago. I was there running a security workshop for a local company and whilst in town, I caught up with Mikko Hypponen:
Troy Hunt (@troyhunt) in Helsinki today. Troy's http://t.co/zOiZnkMpNo service is highly recommended! Use it. pic.twitter.com/lf59Hz7zvI
— Mikko Hypponen (@mikko) May 28, 2015
Now Mikko is a very interesting bloke having been around in the security industry since just about forever so he's seen a few things. There's a great TED talk where he talks about the first PC virus and actually travels to Pakistan to track down the guys who wrote it. He's also the Chief Research Officer at F-Secure who make the Freedome VPN, a tool I've used for some years now and it brings me to the point of this post.
I'm having a chat to Mikko and he's talking about Freedome and the importance of trust when he comes out with a really interesting comment:
You know what's great about Finland? We're the least corrupt country in the world!
So I looked it up and he's right! Either Finland or Denmark depending on whose stats you read but there it is, right up the pointy end of the list. And this is actually really, really important when it comes to a VPN because not only do you need to trust the company running the service, you need to trust the jurisdiction they're running in too because to some extent, you're beholden to their local laws.
VPN providers control your traffic. They can inspect it, modify it, log it and have a very good idea of what it is you're up to. And just before you say "ah, but much of my traffic is now HTTPS", as I wrote earlier this week, the negotiation phase of the connection is still observable so the VPN provider knows the site you're connecting to. Even upstream of that, DNS queries can be watched so per that article, there's a hell of a lot anyone inspecting your traffic can glean even on encrypted connections. Whoever can see your traffic - be that your local ISP or the VPN provider you decide to use - has an enormous responsibility and you're placing a huge amount of trust in them.
Which brings me to MySafeVPN. I first heard of these guys when they sent me spam a few days ago:
I woke up to an email allegedly from @plex that seemed very out of character. Looks like it's spam (or worse): https://t.co/FXWcZ1SEnM pic.twitter.com/4ZN5t84QFO
— Troy Hunt (@troyhunt) April 3, 2017
Which lead through to the MySafeVPN.com website:
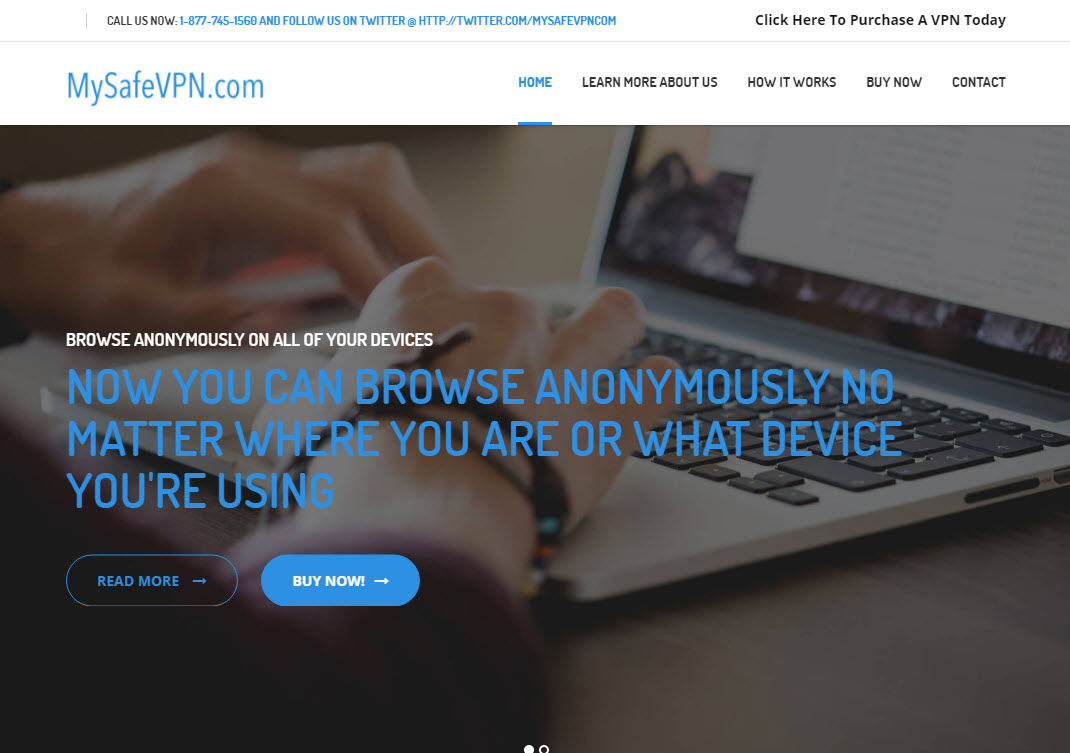
Now any reasonable person would read that email and conclude that it's intended to represent an offering from Plex because, well, it literally says "Plex reveals...". And thus begins an absolute train wreck of communications as they attempt to explain themselves:
@danielvena @plex Daniel, part of plex's development team is working at MySafeVPN hence they sent the email. The corp Plex is unhappy because they don't earn.
— MySafeVPN (@MySafeVPNcom) April 4, 2017
The basic premise (as it's repeated over and over again), is that there are Plex developers working for MySafeVPN and therefore this is not spam and putting Plex's name on it is cool. Of course, neither of these things are correct and Plex themselves are clearly unhappy about the whole thing:
@MySafeVPNcom @danielvena Sorry, but this is just a flat our lie. Neither our company or any of our employees are affiliated with you.
— Plex (@plex) April 4, 2017
So how do you explain the emails? Well Plex had a data breach back in 2015 and a few hundred thousand email addresses (including mine) were released out into the wild. It's not just them, Boxee lost data in 2014 and they too have been misrepresented by MySafeVPN:
@troyhunt I wasn't going to name them, but they spammed all the old Boxee mailing lists as well https://t.co/OEuzRElHHE pic.twitter.com/buDapVMTf7
— Legost’d’ve (@scott_thewspot) April 5, 2017
In the Plex case, their data breach was as a result of a vulnerability in the IP.Board forum software they were running, a threat which miraculously, MySafeVPN believes their product can protect users from:
@plex @tony_sutton @Scott_Helme @troyhunt @plex You should be happy that we're securing your system. Judging by 2015 you guys do not do a good job with security.
— MySafeVPN (@MySafeVPNcom) April 5, 2017
But let's move past the Plex connection for a moment and look at how the service is presented, keeping in mind of course the importance of integrity and trustworthiness in a service such as this. We'll start with attempting to order the product from the website at mysafevpn.com:
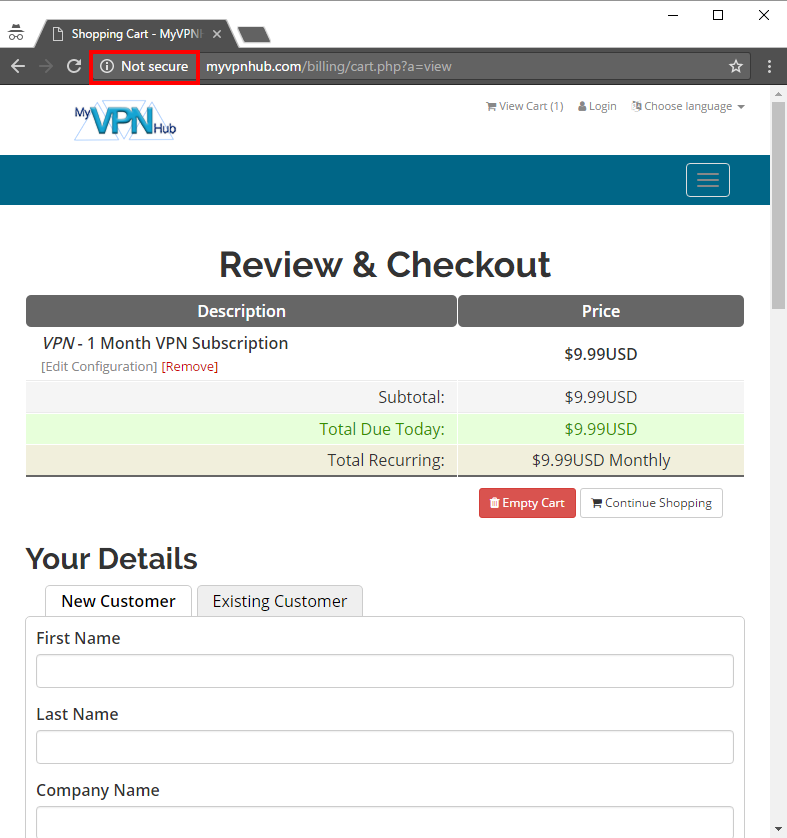
Not a good first impression for a company providing a cryptographic service! You'll also notice we're now off on myvpnhub.com for reasons which aren't exactly clear. We could attempt to force a secure connection, but that just returns a certificate for flfixed.com (which is an empty site with a landing page):
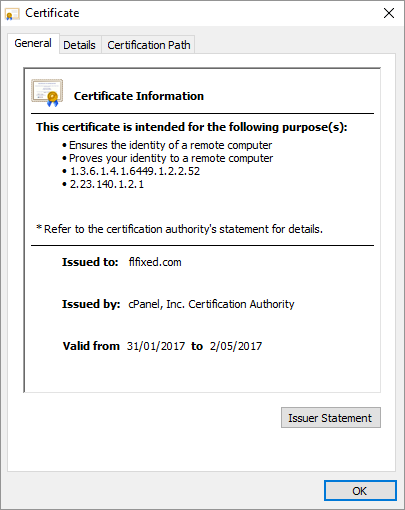
The lack of cryptographic protection didn't go unnoticed by the increasingly large array of people chiming in on the discussion:
@MySafeVPNcom @Scott_Helme @plex @troyhunt Your sign up page have no SSL, which means you're leaving personal data. Everything looks dodgy.
— Tony Sutton (@tony_sutton) April 5, 2017
But as things unfolded, the responses from MySafeVPN became more and more nonsensical, at least for an organisation (or possibly even just one individual), that should understand some of the basic mechanics of how modern day SSL or TLS work:
@tony_sutton @Scott_Helme @plex @troyhunt Our corporate SSL is going to be installed shortly, however the SSL's that actually protect you are very expensive and have a long process.
— MySafeVPN (@MySafeVPNcom) April 5, 2017
Just recently I wrote about what a fantastic time it is for HTTPS and how the free availability of transport layer security from the likes of Let's Encrypt and Cloudflare are transforming adoption rates. And then Scott Helme got involved and helped clarify:
@AdamR0berts @MySafeVPNcom @tony_sutton @plex @troyhunt It's not cheap, it's free. It doesn't take a day, it takes minutes. They should know this. They're just incompetent.
— Scott Helme (@Scott_Helme) April 5, 2017
Now Scott is the last bloke you want to argue the merits of certificates with, he literally runs a training program called The Best TLS Training in the World. Yet this didn't stop them attempting to educate him:
@Scott_Helme @AdamR0berts @tony_sutton @plex @troyhunt Not sure what kind of self signed horrible SSL you're talking about. You should head over to Namecheap and check out the real SSL Certs.
— MySafeVPN (@MySafeVPNcom) April 5, 2017
And it all goes downhill from there in ways I don't particularly want to document blow-by-blow here, but you can always read through their timeline with replies if you're the type of person who likes watching a train wreck in slow motion.
The website itself is full of misleading at best or even outright false statements. For example, their certifications:

Which they explain away as follows:
@tony_sutton @Scott_Helme @plex @troyhunt Tony, our employees are all trained with various certifications from VMWARE Management certs, SYMANTEC VAULT certs, etc.
— MySafeVPN (@MySafeVPNcom) April 5, 2017
Whilst neither VMware or Symantec are mentioned in the list on the site, having a product like a VPN certified is a very different story to having people working for you that have achieved certifications.
Then there's the support number:
I actually tried this yesterday and it went straight to a voicemail service which didn't surprise me in the least. I tried it again earlier today and it was the same story - straight to voicemail. I thought I'd give it one more shot and record it to make a point about it being an unmanned phone, but then, well just listen:
Well that was weird, not exactly what you'd expect from a trustworthy VPN service!
Speaking of getting in touch, they're apparently headquartered in Ontario:

Which you can find on Google Maps and check out using Street View, it's the one with the red seats out front:
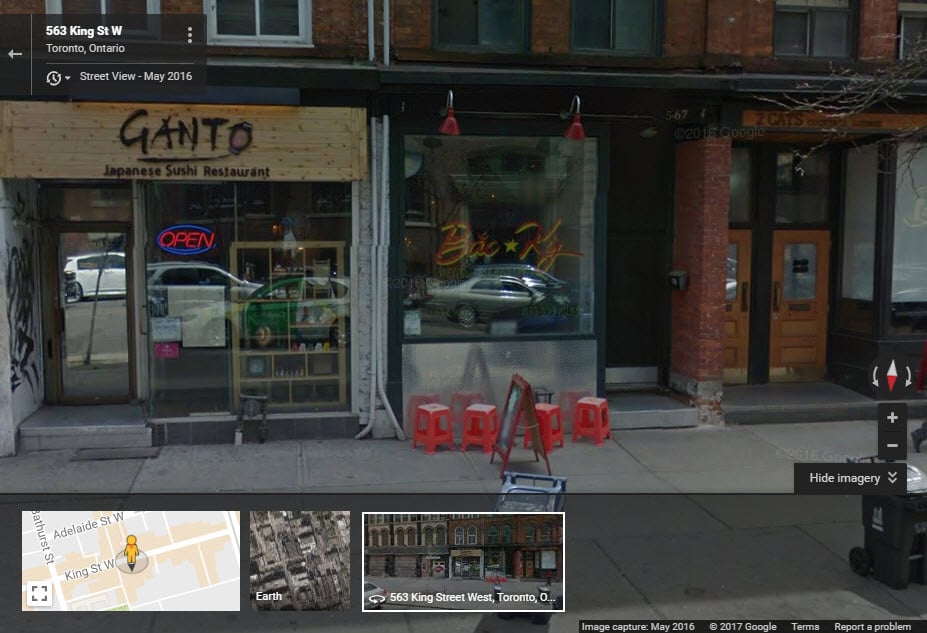
And in case that looks like an odd place for a VPN provider to be HQ'd, that's because it's a Vietnamese restaurant:
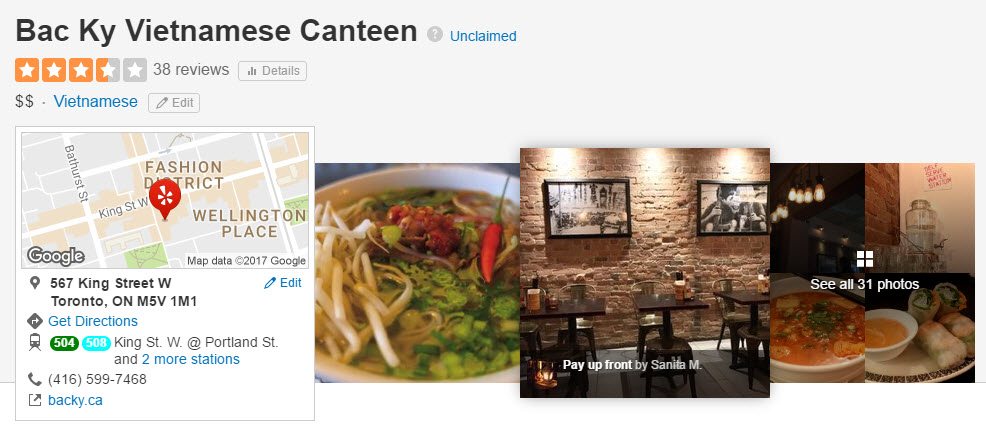
Apparently the Pho Ga is good but what that has to do with a VPN service is beyond me. Look, maybe it's a guy running it out of his bedroom above the restaurant, I don't know, but the point is that combined with the weird greeting on the support number and other oddities observed earlier, clearly the whole thing is very fishy.
Others have also classified the service as untrustworthy:
@J0k3r_2016 @MySafeVPNcom @troyhunt And... pic.twitter.com/nfgHzwJuac
— Paul Wilson (@pwgolfer) April 5, 2017
And even as I attempted to take screen caps of the site, it was going in and out of suspended mode:
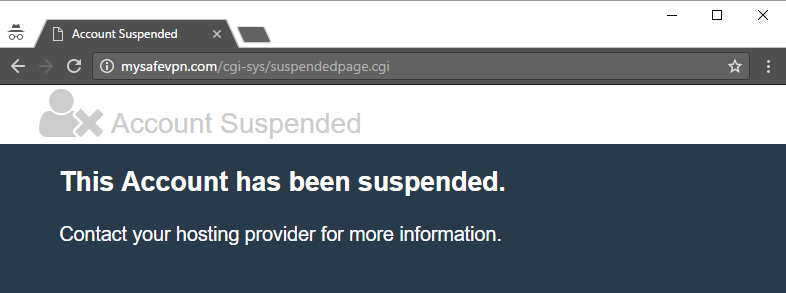
At first, I thought this was the inevitable conclusion of the thing - the hosting provider had pulled the pin - but it did indeed come back to life and remains up at the time of writing.
Whilst looking into MySafeVPN, I was contacted over DM by the account. I won't relay what they said because that was a discussion between the two of us, but I did strongly suggest they stop tweeting, get their shop in order, then come back and explain themselves properly once they've done that. That was after a bit of dialogue back and forth of fairly predictable nature and I didn't hear back from them after that. Clearly the advice wasn't heeded and the engagement via Twitter continued, culminating in racial abuse of a young guy in London who'd joined the discussion:
@Aan_ath @Scott_Helme @MySafeVPNcom @tony_sutton @plex @troyhunt This, my friends, is how @MySafeVPNcom handles their opposition on Twitter. Great way to show maturity of handling a security company. pic.twitter.com/zpJVvzJD4p
— Kelvin Zhang (@KelvZhan) April 5, 2017
Obviously this is all the personification of dodginess. There's been a lot of people chiming in on the topic both via Twitter and over on Reddit where MySafeVPN's behaviour was very eloquently described:
Many people were speculating that this was merely a scam and indeed Motherboard wrote a piece this week about it being a phony service. In that article, they did actually manage to talk to someone on the number I tried and subsequently had a call that culminated in name-calling of the reporter:
This scammer actually called @nicholasadeleon on the phone and called him a nerd
— Motherboard (@motherboard) April 4, 2017
Yet just as I was wrapping up this post, I noticed that they had indeed managed to get a valid certificate on the host name doing the payment processing:
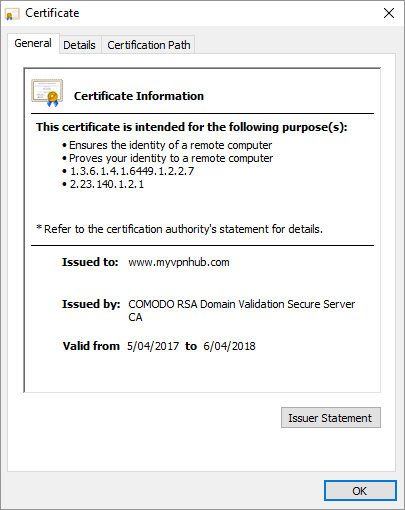
It's newly registered and per the earlier thread where they demonstrated a complete misunderstanding of the value of certs, it was indeed issued by Comodo. They've paid money for this and that shows a commitment to the service. Of course nobody in their right mind should actually pay them anything, but if it's just a scam then it's one they're actually investing in. But then - just to erode any good will that actually securing the billing system may have created, they come out with this:
@aw_nz @Eposig @malwrandpickles @tony_sutton @Scott_Helme @plex @troyhunt The billing area always had ssl.
— MySafeVPN (@MySafeVPNcom) April 6, 2017
We all remember the billing page from the earlier screen grab, right?
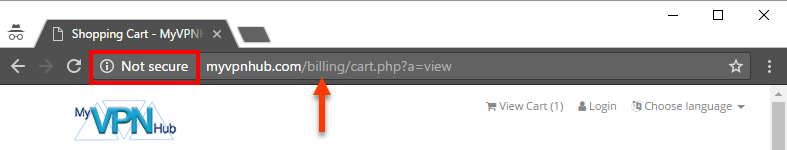
Countering the thinking of "maybe - just maybe - it's not a scam and they're just incompetent instead", I get this just before posting the story:
@troyhunt another one in the same vein as MySafeVPN... pic.twitter.com/IbipMvzDGY
— Matt Coutts (@northirid) April 6, 2017
Now you can try going to myvpnhouse.com but you'll then find yourself at... mysafevpn.com! The spam seems to be directing people to multiple different host names and again, when we come back to trust and integrity, this looks anything but legit. And it goes on. And on.
To wrap up, let's move past these guys and back to the original premise on the trustworthiness of VPNs. You need to know who you're trusting your data with. You need to have confidence that they'll handle it responsibly. You want a proven track record and identifiable individuals who'll back the service. Increasingly, you also want them running in a jurisdiction that values privacy and that means the UK with their Snoopers' Charter is out, the US with ISPs now able to sell your browsing habits is also out and even Australia that's mandated the collection of browsing meta data is out. Canada (where MySafeVPN is allegedly based) forms another leg of the Five Eyes intelligence alliance and frankly, that quintet doesn't have a real good track record when it comes to respecting privacy. People often ask me what I think of [insert other VPN service here] and there's a simple answer - I have no idea. I made my decision based on trust more than anything else and I simply don't have it to that same level with any other provider.
You can get into Freedome for €4.16/m (less than half the price of MySafeVPN) and in case you're wondering, no, I'm not in any way incentivised to recommend their service and have bought my own licenses at full retail price for years.
Edit: About 12 hours after posting, it looks like they've now been taken offline:
And that's (probably) the end of @MySafeVPNcom https://t.co/1axlSzFH6W https://t.co/O7hJAquleG pic.twitter.com/nbtT4SJWuz
— Troy Hunt (@troyhunt) April 6, 2017