This is a blog post about disclosure, specifically the difficulty with doing it in a responsible fashion as the reporter whilst also ensuring the impacted organisation behaves responsibly themselves. It's not a discussion we should be having in 2020, a time of unprecedented regulatory provisions designed to prevent precisely the sort of behaviour I'm going to describe in this post. Here you're going to see - blow by blow - just how hard it is for those of us with the best of intentions to deal with organisations who have a very different set of priorities. This is a post about how hard disclosure remains and how Surebet247's behaviour now has them experiencing the full blown Streisand effect.
It began with this email:

I get these every single day. Seriously, the flood of data that reaches my inbox is hard to describe it's that incessant. It's not always legit, mind you, and I invest a great deal of effort in establishing the authenticity of an alleged breach before loading it into Have I Been Pwned (HIBP). I've written before about how I verify breaches and it didn't take long to be pretty confident that per the subject line of the email above, Surebet247 (a Nigerian gambling website) had suffered a data breach. I'm going to save how I established that for a little later as it'll form part of the subsequent messages I sent them, the main thing for now is that as soon as I was sufficiently confident of the data's authenticity I fired off an email to their published support address:
The message was received. It must have been because the following response immediately came back:
I don't know how much of Office 365 sending the email directly to junk can be attributed to its automated nature, how much is related to its country of origin and how much is due to a missing DMARC record. But that's not the point - the email was received and then... crickets. A couple of days later and without response, I sought the support of Tefo Mohapi, a journalist in South Africa I worked with on the massive Master Deeds breach in 2017. I often use journalists I trust like Tefo to get in touch with unresponsive companies as they're very good at making them sit up and pay attention. And that's where things started to get weird.
With his permission, I'm sharing some of the communication Tefo subsequently had with the company because it's an important part of the narrative as it relates to disclosure. He managed to get a response via Twitter DM pretty promptly, albeit one that didn't really inspire much confidence they were taking this seriously:
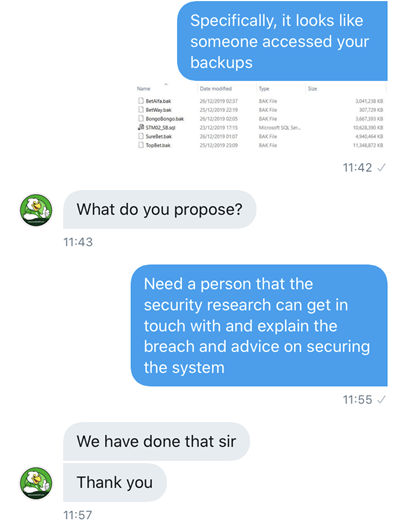
One thing you'll notice in Tefo's first message is the screen grab showing multiple difference database backups (and a single .sql file) indicating they came from different services (my original disclosure email also mentions this). You see, whilst the message that came to me only indicated Surebet247, the ZIP file I was sent included a total of 6 different databases from different services. You'll see those referenced again a little later on but the main thing for now is that regardless of the origin of the breach(es) or whose actual system suffered it, there was very likely data involved that customers had provided directly to Surebet247. They are the organisation people entrusted with their personal information and they are accountable for what happens to it after that.
Also experiencing nothing but crickets, a couple of days later Tefo follows up with Surebet247 to ask them how they're progressing:
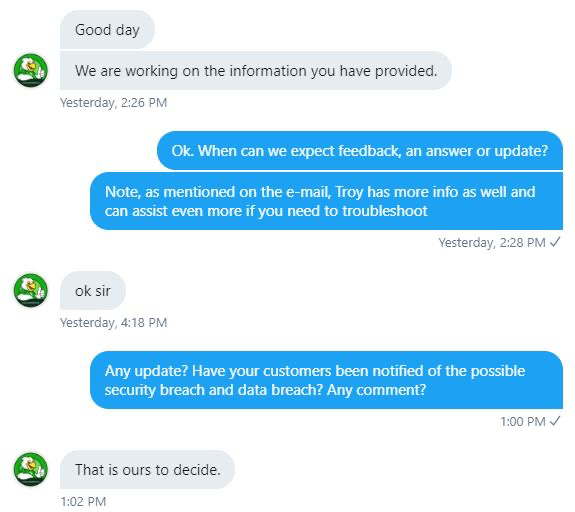
"That is ours to decide." Seriously? That's how you're going to handle this breach? It was becoming apparent that Surebet247 was not intending to set an exemplary example of breach response. Now many days in and having exhausted all reasonable avenues to drive Surebet247 towards appropriate handling of the incident, Tefo wrote about how Nigeria's SureBet247 has suffered a potential security breach. He wrote about our attempts alert them to the incident, the contents of the breach and about their "nonchalant attitude". He also wrote about the other betting operators implicated in the database backups and how there appeared to be a common thread across them. Suddenly, he had their attention. And they weren't happy.
I'll refrain from posting the entire messages he received as they were a bit, well, "legal", but they came from a combination of Surebet247's founder, Sheriff Olaniyan, and a south African attorney they'd retained. The former stated that they "seriously frown at this malicious news been [sic] promoted by your organization" and that they "will not hesitate to take legal action if you don't stop and bring this down". It continued with "No customer data of ours was hacked or exposed" and that Tefo's story amounted to "fake news" (yes, seriously, they went Trump on him). Now, keep in mind that at this stage nobody from Surebet247 had replied to me and subsequently, nobody had seen the data I'd been sent. Yet somehow - magically - they had determined they were in the clear.
Changing pace for just a moment, I want to throw Surebet247 a bone (it's the only one they'll get) because it does look like they had reason for some initial suspicion. Within Sheriff's message to Tefo he also said that "your informant was asking for payment and this was demanded from us". In subsequent discussions, Tefo and I concluded that this was very likely correct: someone in possession of the data was shaking them down for cash. Clearly this is not only unethical but also outright illegal and it would help explain Surebet247's apprehension when approached by other parties about the incident. But that's where the bone-throwing ends as clearly both Tefo's and my own intentions were entirely ethical and it would take about 3 minutes of Googling to work out who we both were and where our moral compasses on such issues point. I understand them being skittish, but shooting the messenger doesn't make for good incident response.
Around the same time as the founder's threatening message, Surebet247 elected to go full Iraqi Information Minister on the situation:
Kindly ignore the information going round about a hack into our system which has exposed your information with us.
— surebet247 (@surebet247) January 4, 2020
All sensitive private and financial information are stored on a secured server and protected by the best firewall to prevent intrusions.
Thank you. pic.twitter.com/YT0w2jRX9f
There were many very appropriate responses posted to that tweet (there's huge comedic value in that firewall comment), but I feel this one provides the best summary of their position:
Sure. pic.twitter.com/vlb6oIt21q
— Chris Sylcox [No. 1042994a] (@ChrisSylcox) January 7, 2020
Once again, keep in mind that as yet, Surebet247 had yet to reply to a single message I'd sent them and did not have the data I'd received, certainly not directly from me and I've seen no evidence to date they'd received it from anyone else either. Assuming they based that tweet on Tefo's story, there was absolutely no basis for them to make that statement.
Becoming increasingly frustrated, I tweeted but refrained from naming them specifically whilst I considered how to proceed:
Going through a painful disclosure process at the moment which is tracking perfectly to this old blog post "The 5 Stages of Data Breach Grief": https://t.co/GNhgrLgJDN
— Troy Hunt (@troyhunt) January 4, 2020
Currently transitioning from "denial" to "anger", the remaining stages will follow, they always do...
My gut reaction was that if they wanted to take this discussion onto the public timeline then a series of rebuttal tweets would be appropriate. I drafted them, sat on them for a while then decided against it. I don't want to see this sort of thing play out on the public timeline, not unless other reasonable approaches have been exhausted so I took the drafts and 14 hours after their denial tweet, DM'd them instead:
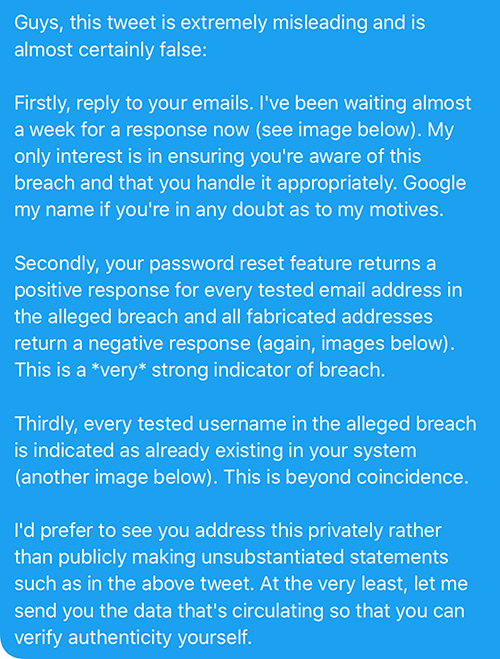
There were 4 subsequent images in the DM thread, the first of which was of the original email to their support address. The second 2 demonstrated the enumeration vector on their password reset feature which confirmed emails in the alleged breach presently exist in their system. Conversely, fabricated emails which wouldn't exist on their system produced an error message. Here are those 2 images:
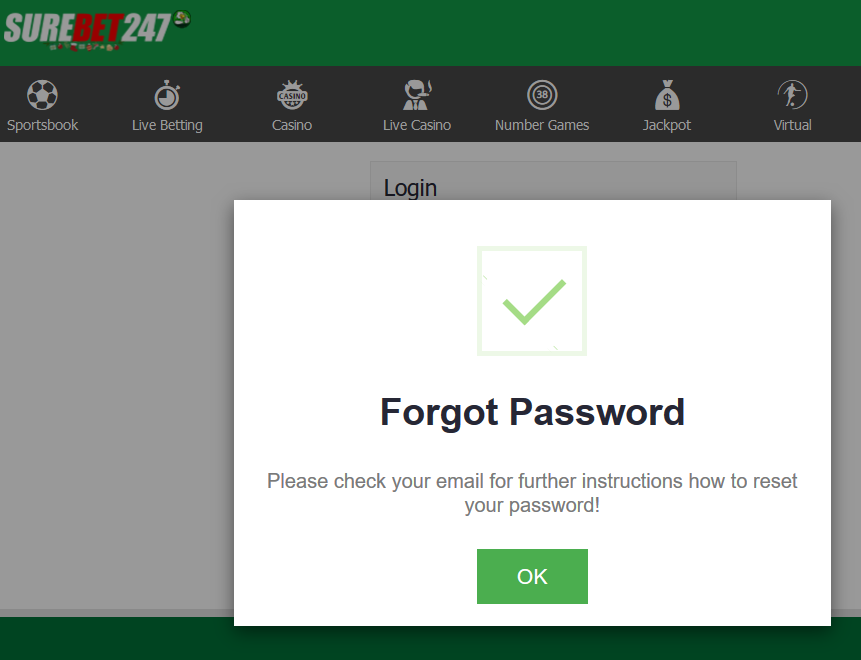
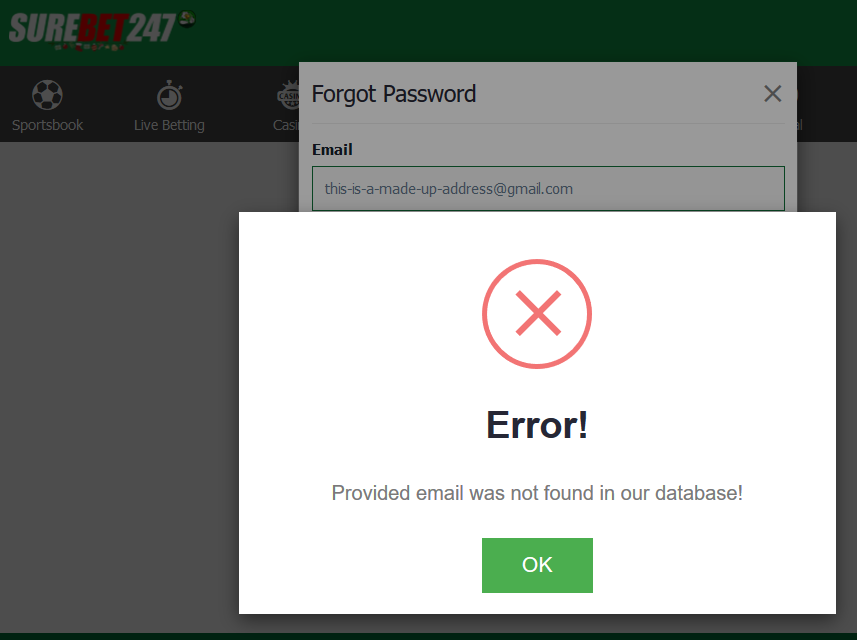
That alone gives me a huge degree of confidence in the legitimacy of the breach (I tested a handful of addresses and they consistently produced the same results), but hey, why stop there? I sent a 4th image showing the registration feature confirming that usernames in the breach exist in the online system:
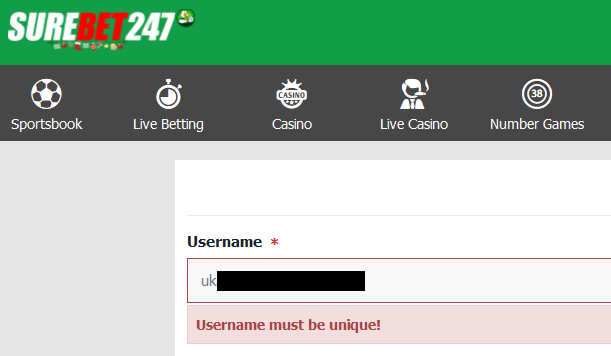
A day passed. Two days passed. Nothing. These guys really want to do this the hard way, don't they?! Expecting them to go down kicking and screaming, I reached out to a handful of my HIBP subscribers who also appeared in the breach and asked them 3 simple questions:
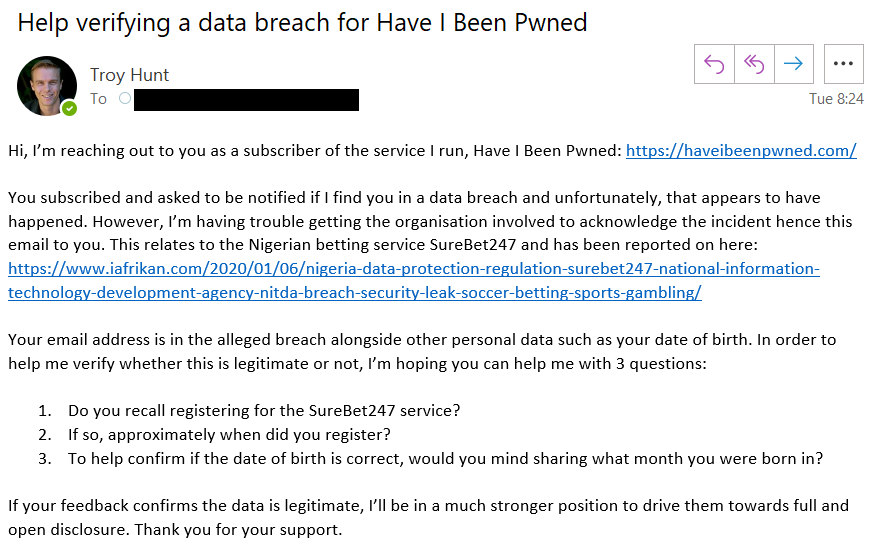
With 3M subscribers in my service, I've always got a good sample set that crosses over with any sizeable breach I come across and as such, I've always got candidates willing to help with breach verification. I fired off the emails and waited.
At the same time, instead of acquiescing to Surebet247's bullying tactics, Tefo upped the ante further by writing a second article after reaching out to Nigeria's National Information Technology Development Agency (NITDA) who had the following to say:
The Director-General, and CEO of NITDA, Mr. Kashifu Inuwa Abdullahi, gave an order for the incident to be investigated by NITDA's Data Breach Investigation Team.
This, of course, is precisely what we'd expect of a regulator and I'll be eagerly awaiting the outcome of that investigation. Speaking of eagerly awaiting, it didn't take long to get a response to my HIBP subscriber outreach emails with a reply promptly coming back from a gentleman named Stefan. Stefan confirmed that he'd used the Surebet247 service in the past and gave me his month of birth. It matched perfectly to the data in the alleged breach. I reverted with his day of birth and in turn, he confirmed it was accurate. Lastly, curious about his European name, I asked him which country he was from and he replied with a single word:
Germany.
Oh, now it's interesting! Once you start dealing with the personal information of EU data subjects it invokes the whole GDPR discussion, a fact that Tefo quickly jumped on and used as material for a third article about how Surebet247 is in violation of the European Union's GDPR.
I also asked another question in the original email I haven't touched on yet: "approximately when did you register"? In Stefan's initial response, he advised that "The first newsletter I found is from 13 feb 2014" (obviously Stefan likes to hold onto all his mail). However, this didn't line up with the data which suggested the registration date was "2016-09-19". I shared that data point with him and he came back with a really interesting explanation:
On 27 sep 2016 I got an email concerning "Migrations Challenges" (telling me that all balances are secure). So, maybe on 19 sep 2016 they migrated to another platform and "registered" everyone per that date?
Sure enough, further inspection of the data showed thousands of records all "registered" on that same day: 19 September 2016, a mere 8 days before the company sent an email about "Migration Challenges".
Another HIBP subscriber responded:
Yes, I know surebet247 service, a betting bookmaker based in my country Nigeria. I cannot recall the date I registered, but I know that it's earlier than 2019, my account there should be over 2 years old. My month of birth is October.
Surebet247 user? Check.
Registered more than 2 years ago? Check.
Born in October? Check.
Every single response I got from every single subscriber that replied to my request for support confirmed precisely the information contained in the "alleged" breach. Now, I ask you: what are the chances that someone sent me a trove of data with so many independently correlating points and yet "no customer data of ours was hacked or exposed", as Sheriff phrased it? If Surebet247 was to offer odds on the likelihood that they'd been breached, they'd be very short odds indeed!
So it's back to Twitter to DM them again, however...
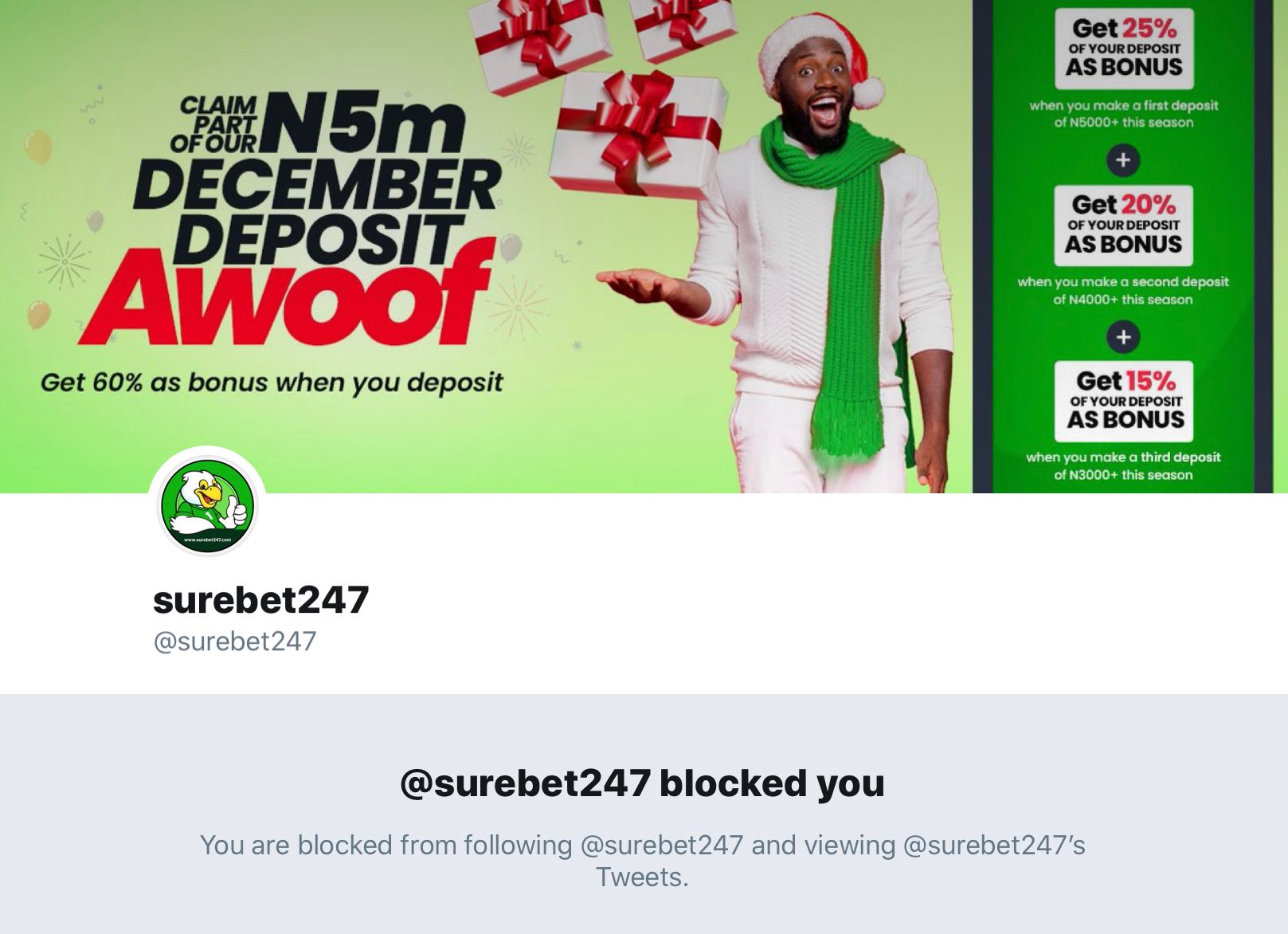
And that's when I decided to write this blog post. 8 days after first attempting to alert them privately to a serious security incident that would not only impact their customers but also impact their own business interests, they decided that this was the most appropriate course of action:
— Stefán Jökull Sigurðarson - CCP Ghostrider (@stebets) January 7, 2020
Now remember, this is a company that handles other people's money! Granted, gambling merely amounts to a tax on people who can't do maths but regardless, you'd expect at least a vague attempt at professionalism. It wasn't just me that was blocked either, I was originally alerted to Surebet247's propensity to silence bearers of bad news by Tefo who'd just discovered he'd lost his primary channel of communication with them. It wasn't just us either, they were on a rampage to drown out other voices they didn't like too:
Oh yeah. You must have hit a nerve. pic.twitter.com/VNZNuYr1fv
— Matt (@undulanti) January 7, 2020
Oh no they got me!! pic.twitter.com/pAfyT4MxZi
— Scott Helme (@Scott_Helme) January 7, 2020
Mention “breach” they block. Got us too pic.twitter.com/DWPirXyOor
— iAfrikan.com (@iafrikan) January 7, 2020
Welp!!! pic.twitter.com/AvpBCiP8V3
— Angry Wizard (@0xRogue) January 7, 2020
Same here. pic.twitter.com/d3IrcwbTsd
— Omokolade Ogunleye (@kolade_ogunleye) January 7, 2020
They blocked me pic.twitter.com/QO2PvsDVKC
— Chris Sylcox [No. 1042994a] (@ChrisSylcox) January 8, 2020
1 tweet was all it took pic.twitter.com/fuAAtmZ5ea
— Baikunth (@baikunth) January 8, 2020
Took less than 2 minutes ? pic.twitter.com/z1LVWYu8kW
— John Shepherd (@john_shepherd) January 8, 2020
Woo! pic.twitter.com/0lHIKRTqXp
— Henge Witch ⚧ (@enbytech) January 8, 2020
It took me 4 tweets the last one input the you have been hacked gif on! ???? pic.twitter.com/jiDE2FlnGr
— mRr3b00t (@UK_Daniel_Card) January 8, 2020
Blocked within a few mins of my post ? pic.twitter.com/wuDjLCvg9q
— Stephen Marriott (@stephenmarriott) January 8, 2020
Must be my lucky day, @troyhunt! pic.twitter.com/t4diMhjPsZ
— Randolph West • they/them • ⚧ (@_randolph_west) January 8, 2020
Sure, here you go. pic.twitter.com/ruIgMM0Wb1
— Tony Sutton (@tony_sutton) January 8, 2020
Took only minutes pic.twitter.com/WjkPppswag
— Peter Tonoli (@peter_tonoli) January 8, 2020
— Joseph G (@Joseph_G167) January 8, 2020
— Paul Moore (@Paul_Reviews) January 8, 2020
And now here we are, Streisand'd all over the place.
The Streisand effect is a phenomenon whereby an attempt to hide, remove, or censor a piece of information has the unintended consequence of publicizing the information more widely, usually facilitated by the Internet.
Because of Surebet247's attempts to censor discussion on this incident, they're getting more of it than ever with the press now starting to jump onto it well beyond Tefo's initial 3 stories:
— NITDA Nigeria (@NITDANigeria) January 7, 2020
SureBet247 suffers data breach and leaks customers’ gambling information https://t.co/xJieqOf9Y6
— Alexa Gómez (@AlexaGm33043450) January 3, 2020
Bad corporate behaviour like this is no longer something you simply sweep under the rug; it needs to be broadcast far and wide as a cautionary tale for the next organisation that elects to follow the same strategy. Per my earlier tweet about data breach grief, the outcome of this process is a foregone conclusion and assuming I haven't made a massive series of errors in the workings explained above, Surebet247 will ultimately come clean about the breach and take responsibility for their actions.
I'll leave you with a quote I've said many times now and it's more relevant in this situation than ever before:
We are now in an era where people are no longer judging organisations as harshly because they had a breach, but are judging them more on the way they handle it.