I watched a discussion unfold on Twitter recently which started like so many of the security related ones I see:
When website errors make no sense! @Argos_Online my password is more complex than your system can handle. What gives? @troyhunt #insecurity pic.twitter.com/64VA7qINGP
— Jon Carlos (@billywizz) June 10, 2017
This was a very misleading error message on Argos' part and as it turns out, what it really mean was that they only allowed up to 20 characters in passwords. It's the classic arbitrary limit story; for various reasons which may include legacy dependencies, ignorance or very often, a database column of limited length (which then implies no password hashing and quite likely plain text storage), Argos were denying users the ability to use long passwords.
Now there'd be nothing remarkable about this story if it weren't for the ongoing dialogue which eventually led here:
Thanks Alicia. Please pass this gif on https://t.co/0d5imtWrtm i believe intel might know better than your dev/mgnt team!
— Jon Carlos (@billywizz) June 10, 2017
This is your classic password strength indicator which applies simple mathematics to work out how strong the thing is. More characters of more types equal more strength, right? A perfect example of this sort of maths is on display at howsecureismypassword.net (the service used for the calculations in the image Jon posted). For example, the password "password" is cracked "instantly":
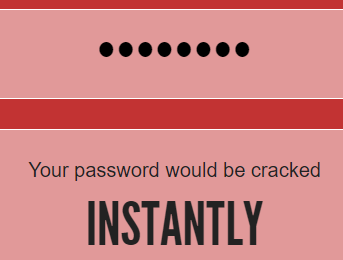
However, if you got smart and used a technique that no hackers know and changed that password to "Passw0rd!" (that's with a zero), you're looking at a lot longer:
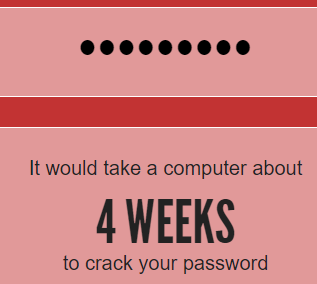
Whoa! That's awesome! I'm not sure exactly how much longer than "instantly" 4 weeks is, but it sounds like a lot.
Moving on, having referenced the password strength meter, Jon got a rather predictable response from Argos:
Checked out the GIF, it shows that a password with 20 characters takes 35,000,000,000,000,000,000,000 years to crack. That'll do! ~ Alicia
— Argos Helpers (@ArgosHelpers) June 10, 2017
Now I'm not sure exactly what that number is, but I know it has a lot of commas and looks impressive ergo, 20 characters is more than enough for anyone, right?
The problem with all of this is the dependencies on maths and the failure to recognise that this is simply not how people create passwords. Now you may well be an exception (as am I) in that you use a password manager and generate random passwords in which case 20 characters is just fine. (Except that short arbitrary limits can play havoc with password managers.) Even with a fast hashing algorithm like MD5, nobody is cracking a genuinely random 20-character password in an any amount of time that should worry you. But the problem with short arbitrary limits is more complex than that.
Passphrases are a perfect example and this classic XKCD comic illustrates them beautifully:
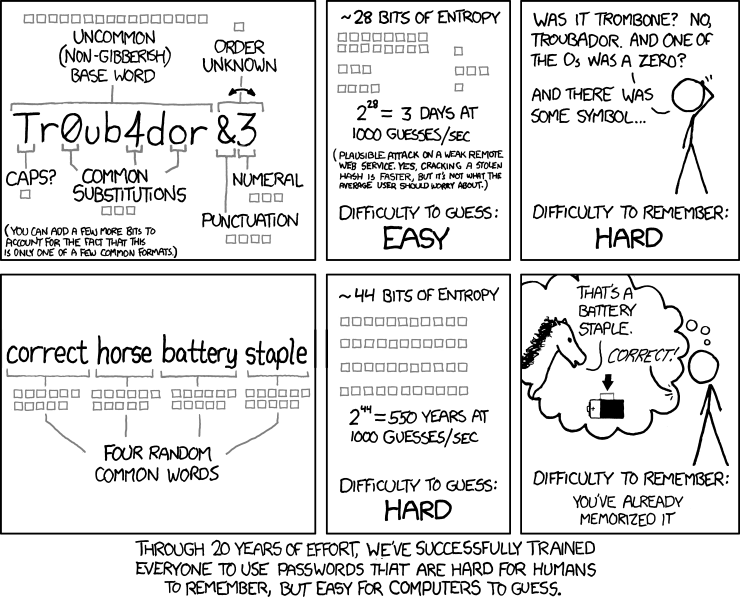
Now you can look at this in two different ways: firstly, it's a 27-character password so it's long (and consequently disallowed by Argos) which means it's very, very strong:
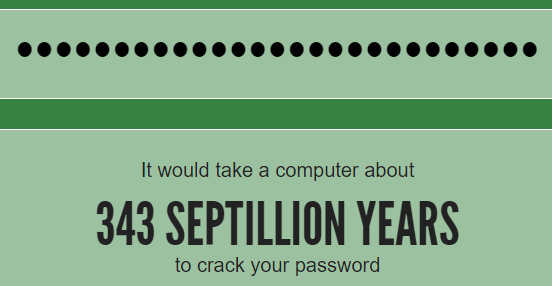
But the other way of looking at it is that it's totally useless. Why? Because it's a very well-known password courtesy of that cartoon and just like "Passw0rd!", it's going to appear in any password dictionary worth its salt. These passwords won't be cracked in 4 weeks (let alone any period measured in septillions), it'll be a significantly shorter time than that. How long? well that really depends on the hashing algorithm. I frequently refer to Jeremi Gosney's Nvidia GTX 1080 Hashcat Benchmarks in my workshops and you'll see that that the difference between say, MD5 and bcrypt can literally be 2 million times. 2 million times - how do the password strength calculators cater for that? Easy - they don't.
But let's get back to Argos for a moment and see how they go with handling a few sample passwords. We'll start with the registration form:
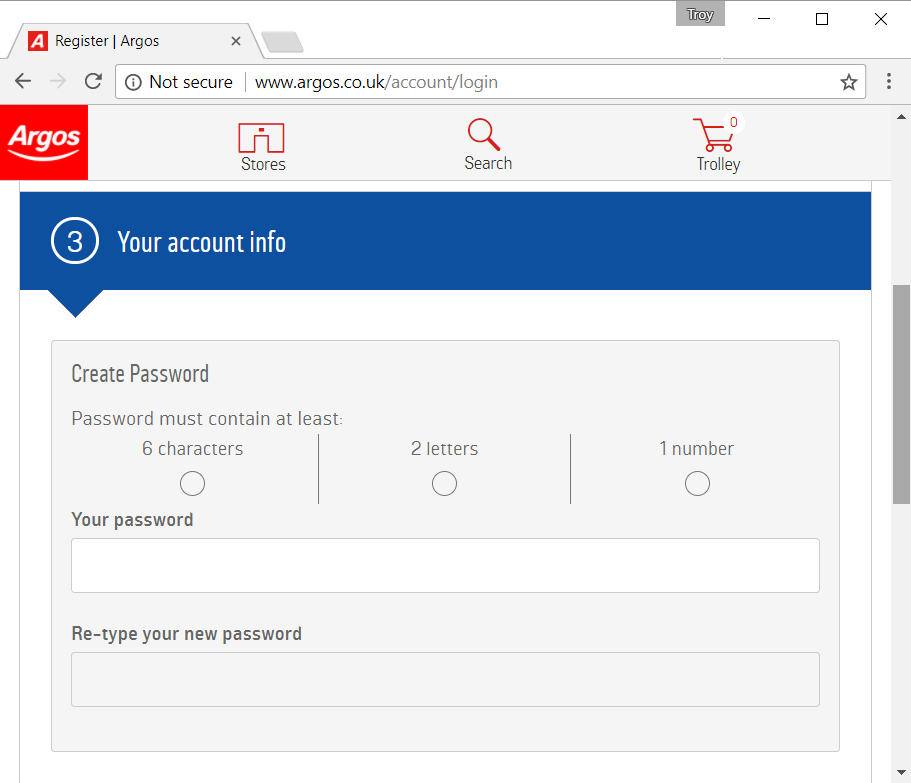
Right off the bat, the "Not secure" warning next to the address bar doesn't inspire confidence. C'mon guys, this browser warning came into effect 6 months ago already! Ironically, they can issue a valid cert if you manually enter the HTTPS scheme but clearly most people aren't going to do that.
So let's try some passwords of various configurations, for example XKCD's "correct horse battery staple":
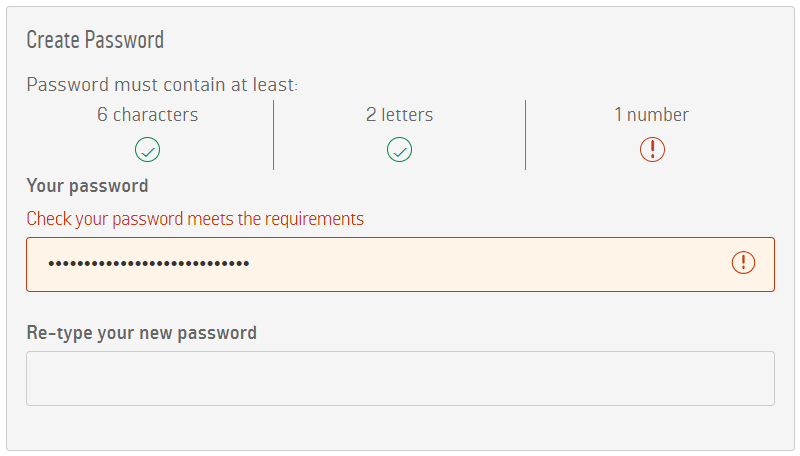
Even though the structure of the password is very strong (remember, we're talking "343 septillion years" here), it's rejected. But didn't Argos themselves just lean on the premise of a 20-character password being very strong? Yes, they did, but because there's not a number you can't use it (plus it exceeds their 20-char max). Now as I said earlier on, you shouldn't be using this exact password anyway, but obviously that's not the reason it's being disallowed here.
So let's dumb it down as far as we can and use "passw0rd" instead (that's with a zero in it):
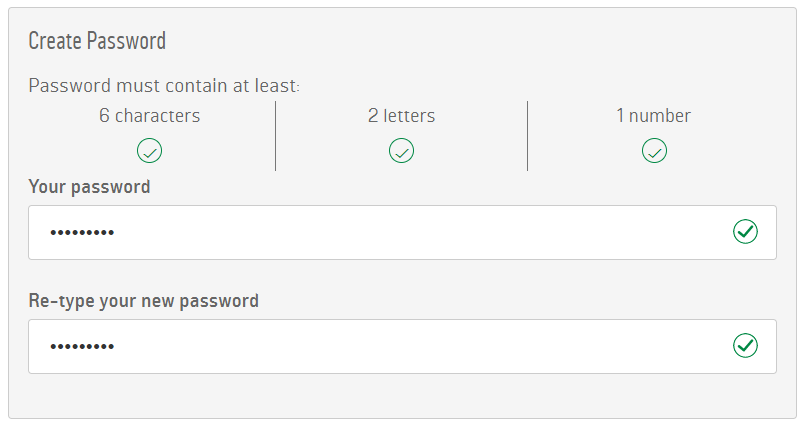
Success! This is one of the worst passwords conceivable yet it's allowed whilst good ones are rejected. In fact, it well and truly exceeds their minimum criteria as it has 8 instead of 6 characters. As I showed recently, even when using a strong hashing algorithm like bcrypt as CloudPets did, when you allow terrible passwords like this they'll still be readily cracked if they're ever exposed:
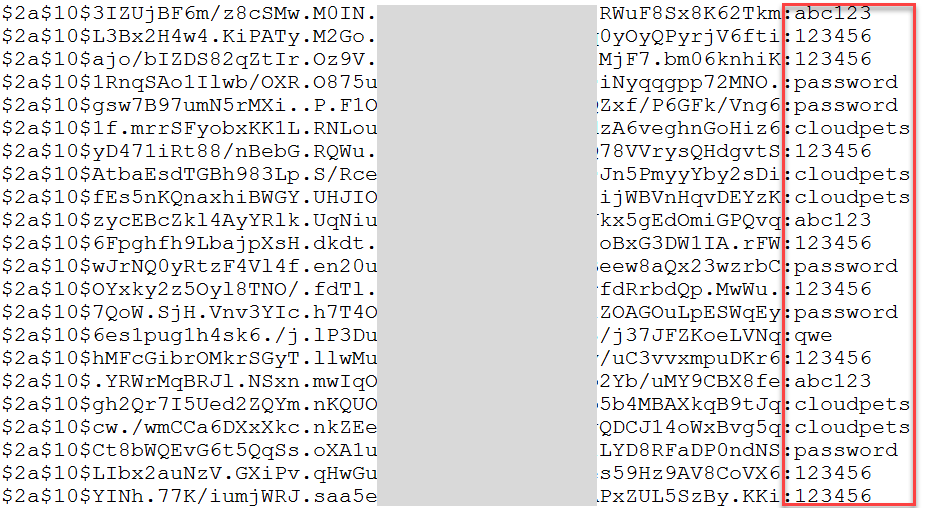
Here's the bottom line with all this: password strength meters which simply run JavaScript in the client and apply basic mathematics are woefully inadequate. Likewise, websites applying similar maths to enforce "strong" passwords in no way guarantee that actual strong passwords will be chosen. All these calculators neglect the human element of passwords and that's an enormously important part of the picture.
So what should we be doing differently? Fundamentally, it's an education issue and the key tenets people need to understand boil down to the risks of password reuse and, of course, what genuinely constitutes a strong password. NIST recently created some great material along these lines and I'm presently writing a much more comprehensive piece on that. (Incidentally, that NIST guidance also recommends allowing at least 64 characters in a password.)
Password strength indicators like those above are nothing more than simple calculators. They know nothing of human behaviour and that's an absolutely critical element of how passwords are created, managed and indeed compromised. "Good" password indicators don't necessarily mean they're good and "bad" ones don't necessarily mean they're bad. More on that in the coming weeks.