We tend to get very focused on digital security controls; firewalls, antivirus, software updates and then all the usual practices I spend so much time talking to developers about, stuff like defending against SQL injection, cross site scripting and a whole raft of other attacks against systems. But the bigger risk – and it’s one that doesn’t get near as much coverage – is attacks against humans. Whereas most of the time we’re thinking about attacks against the systems, we tend to neglect weaknesses in the organic matter controlling them and as a result, social engineering attacks are enormously successful.
I’ve just wrapped up Ethical Hacking: Social Engineering and when reflecting on what I should write here, it was honestly hard to know where to even start. I’ll start somewhere that’s familiar to a lot of people – with this:
It’s now four years since I recorded this and it has well over a million views. It’s also where I kick off with the social engineering course because that’s exactly what goes on – a scammer tries to socially engineer me into believing that my PC is full of viruses and I should pay him money to fix them. I decided to include key parts of this video in the course and narrate them because it’s just such a great demonstration of so many social engineering behaviours. For example, the scammer begins by establishing authority in claiming he’s from Microsoft and has received alerts from my PC before instilling fear when he explains how my PC is infected with viruses. He proves his authenticity by taking me through the event log (these are the viruses, y’know!) then “fixing” the PC to create a debt he consequently attempts to monetise. I distil the lengthy video down into the key points that best demonstrate the attack styles and we see these behaviours repeated at numerous other points during the course.
One of the things I realised when writing this post was that there were some really interesting social engineering attacks that hit the tech headlines during my production of the course. For example, there was Brian Krebs’ post on PayPal’s lazy authentication which boiled down to people being able to easily – and repeatedly – take over his account just by relaying publicly available information about him to PayPal support. The other one that made quite a few headlines even in the consumer news was Amazon’s customer service back door. This one exploited Amazon’s online help service again, by using readily available information found on the web.
In fact, that’s a common theme in social engineering; the use of OSINT or “Open Source Intelligence” data and you can find it everywhere from social media sites to WHOIS records to online telephone books. The amount of information available on people is extensive and not just from disparate sources, but aggregated into services like pipl where you just pop in a name and get back a unified view of the individual. Try it on yourself and you might be surprised by just how much it finds.
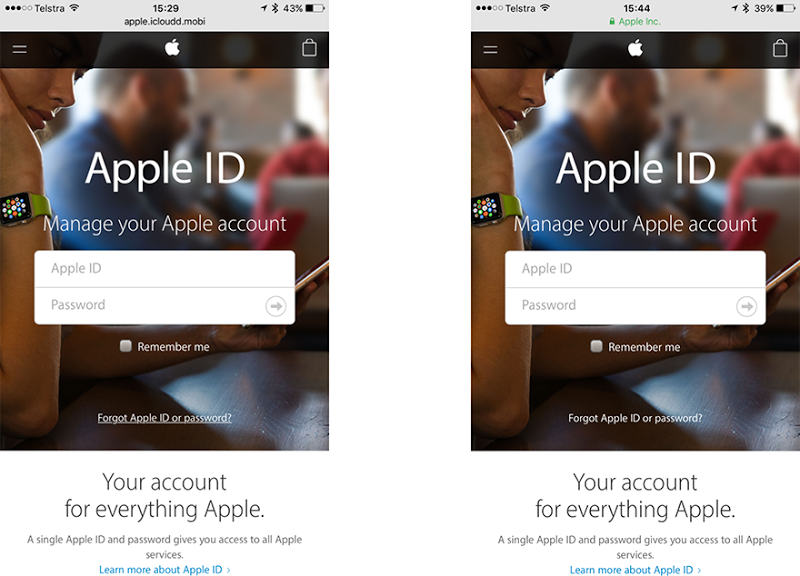
There’s a heap of other aspects of social engineering I delve into in the course, one of the biggies being phishing. I walk through a bunch of typical examples, for example the affinity with attackers using subdomains such as paypal.com.attackers-real-domain.com in order to fool victims who focus solely on the first part of the URL. Whilst many phishing attacks stand out due to various obvious indicators (and indeed there’s a school of thought that suggests this is intentional), I’ve also seen some exceptionally good ones lately. You’re probably more technically inclined if you’re reading this blog and will know what to look for here, but do you think the average consumer could spot the phishing site below?
I also walk through how to mount your own phishing attack with the very cool Phish5 service and indeed I wrap up the course by saying you should go and give this a run to “condition the humans”. The traditional approaches to defending an organisation against social engineering attacks tend to be to force people through mundane training they must then sign off on and promptly forget or just to whack up a bunch of security posters which become “white noise” in the office, I mean just look at some of these! They don’t change behaviours, certainly not when compared to hitting them with a service like Phish5.
In creating this course, I drew from a bunch of first hand social engineering experiences I’ve previously written about, for example This is your bank, please verify your details and Happy birthday! Now anyone can login to your Betfair account. For those of you who watch the course I’m sure you’ll see a lot that resonates and you’ll identify all sorts of places that you’ve been exposed to social engineering either as a victim (if you have kids, you’ll have suffered physiological manipulation!) or opportunities where you could exercise it to your own advantage (I talk about my experience with identify verification at the doctor’s).
This is first and foremost the best social engineering course I could make and I’m enormously happy with how it’s turned out. Due to the nature of social engineering, unlike my other courses it’s a course that can be watched by anyone regardless of their technical competency because it’s so focused on human behaviours. Secondly, it also forms part of the Ethical Hacking series I’m contributing to and it’s now the fifth course I’ve contributed with fellow author Dale Meredith having created seven others. That distinction is important; if you want to study for your Certified Ethical Hacker cert then that’s great and we firmly believe that Pluralsight has the best possible material for that but equally, this course is much broader than just one certification as I said from the outset, each course must stand on its own as an exemplary example of security education on the discrete topic it covers.
Ethical Hacking: Social Engineering is now live!