Last week something a bit unusual happened; Java was found to have a serious vulnerability. Ok, stop laughing, Java has obviously had many serious vulnerabilities over many years, what’s different this time though is that the US government’s Computer Emergency Response Team (CERT) took the unprecedented step of telling folks to stop using it altogether.
Here’s the word from Homeland Security:
Due to the number and severity of this and prior Java vulnerabilities, it is recommended that Java be disabled temporarily in web browsers
And:
This and previous Java vulnerabilities have been widely targeted by attackers, and new Java vulnerabilities are likely to be discovered. We are currently unaware of a practical solution to this problem.
Ok, so that’s not great and for me, it’s the final nail in the coffin. I say final nail because I’m well aware of the reported risks but until now, simply hadn’t been driven to the point of uninstalling Java. When I finally got down to thinking about it, I couldn’t put my finger on what sites I actually used that required Java in the browser. Oh sure, I know the damn thing pops up every other week with a security update but other than that, I rarely, rarely see it.
So on the weekend I nuked it. Gone from my 2 Windows 8 machines, gone from my Windows 7 machine, gone from my wife’s MacBook Air. So did this mean the web became unusable? Or was it business as usual, only more secure? Here’s my experience.
Performing a Javaectomy
Firstly, in case you’re not sure if Java is even installed or not, check out the test page on java.com:
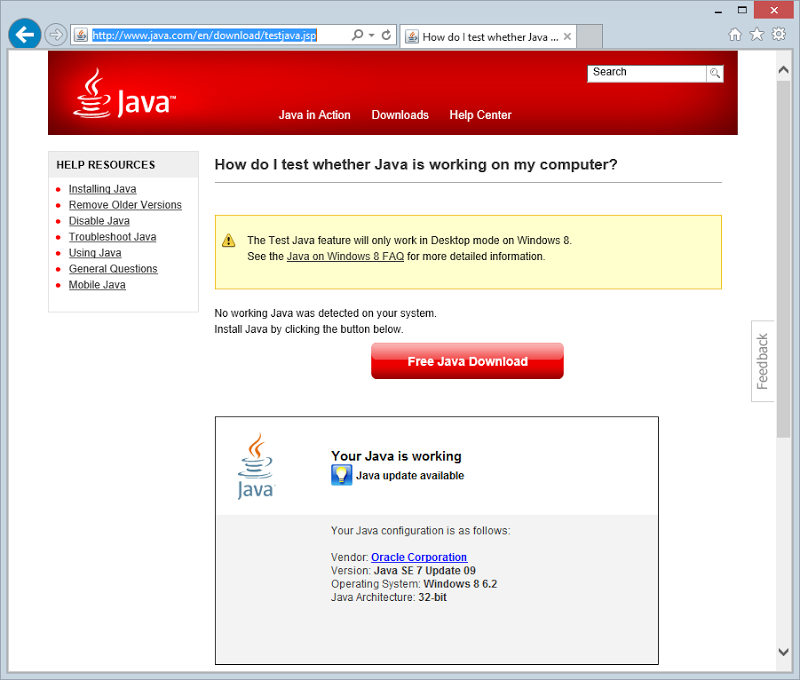
Ok, so present and active in this case. Nuking Java from Windows 7 and 8 is pretty straight forward, just locate it in Programs and Features, right-click then uninstall:
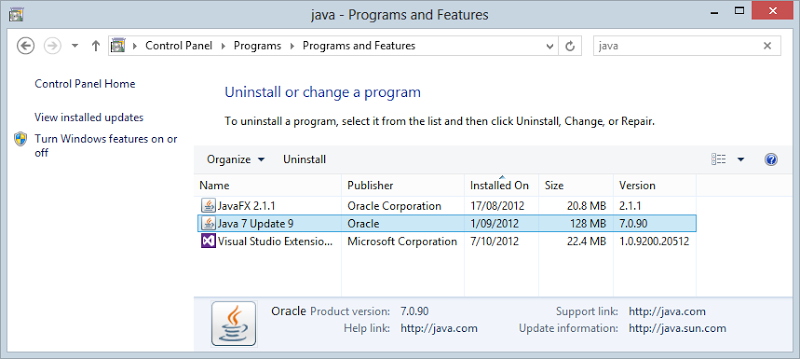
A subsequent visit to the Java test page will be a whole lot less enthusiastic:
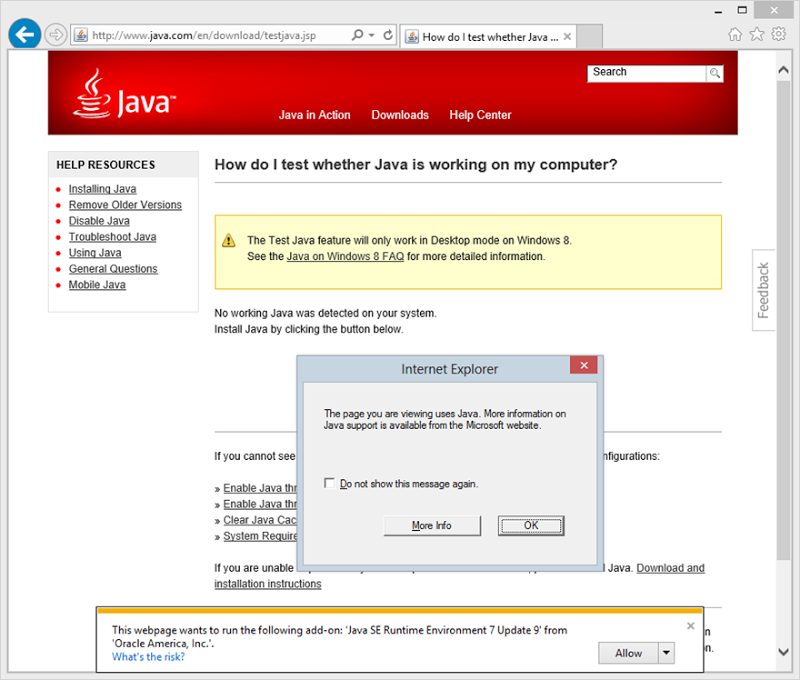
That’s it – no more Java! You’ll see variations of the message above in different browsers but the context is always the same (i.e. doesn’t exist, prompt to download).
Here’s what broke:
Nothing.
Sorry, did you just say “nothing”?
Nothing. None of my banking (I checked multiple banks in Australia and overseas including an old account at HSBC in the UK), none of the internal corporate sites I regularly use, none of the news or forums or reference material websites I use, just nothing.
Clearly this won’t be everyone’s experience, but it should be most peoples’ experience. There is simply not the need for Java in almost every modern interpretation of a web application. I won’t say it’s never needed as there are edge cases I’ll come back to, but it’s extremely rare.
Why Java, why?
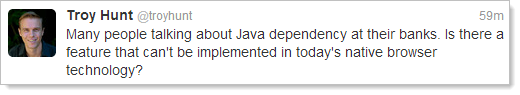
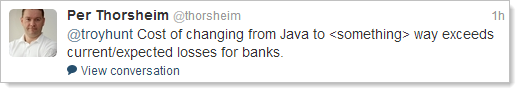
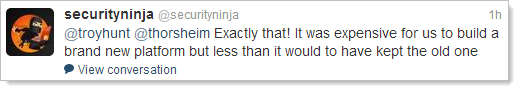
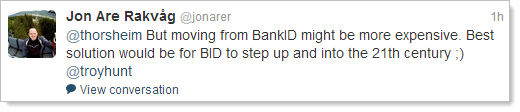
I mean why does it persist today? Why do we need Java in the modern era of HTML and pretty clever web browsers? In general Twitter discussions I heard a lot about banking dependencies (particularly from European / English followers), but very little about why there was a dependency. What’s the Java value proposition?
With the caveat that I am not and have never been a developer of Java, the consensus seems to be primarily because of legacy reasons. Given my lack of Java knowledge, I asked the masses:
Almost exclusively, the responses suggest the Java dependency was a hangover from a bygone era:
Keep in mind those three are from folks who devote a great deal of time specialising in information security.
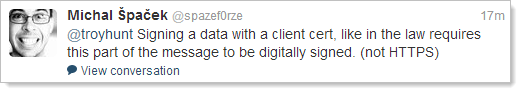
However, there are some valid cases – edge cases – where there might be a need. For example:
Of course the usability aspects of managing client certs are a nightmare but I do appreciate the value proposition they present. Still, there’s an argument to be made about the practical security advantage they provide in a two factor authentication world.
In reality, I suspect this response is far closer to the truth:
So in short, the predominant reason why we still need Java is the dependency on it by financial institutions that are using it simply because they haven’t been able to adapt to modern web development practices. Clearly this is very anecdotal but it was repeated over and over again by a wide range of people. So the very folks that we entrust with our money are the ones requiring us to compromise our online security in order to access it!
Keep in mind also that once Java is required you can rule out access via mobile devices such as iOS gadgets – they simply will not run Java (to their credit). In the banking world, there are often native alternatives (which IMHO are often a better, more secure experience than the browser based ones anyway), but from a pure device compatibility and audience reach perspective anyone standing up a site with a Java dependency is excluding a very large, very rapidly growing segment of their audience. In fact my own stats for troyhunt.com show that over the last month, about 1/3 of the audience had no Java running (they’re the green bit):
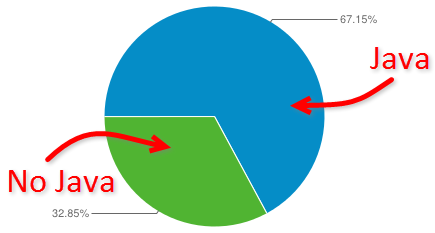
Expecting Java – not smart.
It’s now patched, but that doesn’t really change anything
The specific risk that got US-CERT all uppity has now been patched in Java 7, Update 11. But it doesn’t really change much in so far as it’s just a continuation of a common pattern that goes like this:
- A serious Java vulnerability is discovered
- Exploits are developed (this may happen before the previous point is publicly known)
- Oracle patches it a while later
- Everyone goes back to business as usual
Lather, rinse, repeat. In amongst that cycle some people inevitably get pwned (knowingly or otherwise) and of course step 3 isn’t even effective until people actually take the patch which can be some considerable time. We went through a similar cycle in October and before that in April when even the poor old Mac copped it via the Flashback trojan. There are many, many more examples.
I like the way Brian Krebs summarises Java in this post (emphasis mine):
It’s nice that Oracle fixed this vulnerability so quickly, but I’ll continue to advise readers to junk this program altogether unless they have a specific need for it. For one thing, Oracle tried (and failed) to fix this flaw in an earlier update. Also, it seems malware writers are constantly finding new zero-day vulnerabilities in Java, and I would not be surprised to see this zero-day situation repeat itself in a month or so. Also, most users who have Java installed can get by just fine without it.
Brian goes on to suggest that if you really need Java, just enable it in a browser that you only use for specific sites that demand it. I'd put it in something like Opera and disable from my usual Chrome, IE, Firefox trio because I do appreciate there are some people who are dependent on it, just try to keep it locked away somewhere out of normal sight!
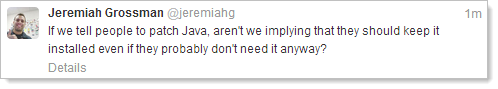
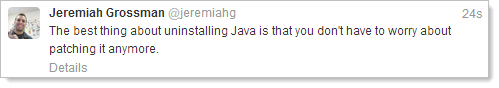
But ultimately, I think Jeremiah Grossman’s advice hits the nail right on the head:
At least I know I’ll never miss a patch again!
Update, 15 Jan 2013: Right after posting this, more news has come out via US-CERT saying that Java “Still poses risks to users” even after the update. Here’s the key message:
Unless it is absolutely necessary to run Java in web browsers, disable it.
Again, this is after update 11 came out. Can’t get much clearer than that.