I love beer. This comes as no surprise to regular followers, nor should it come as a surprise that I maintain an Untappd account, logging my beer experiences as I (used to 😢) travel around the world partaking in local beverages. When I received an email from someone over that way who happened to be a happy Have I Been Pwned (HIBP) user and wanted some cyber-assistance, I was intrigued. You'll never believe what happened next...
The tl;dr is that someone with a BeerAdvocate account was convinced the service had been pwned as they'd seen evidence of an email address and password they'd used on the service being abused. They reached out to my guy (we'll call him that for the sake of brevity) who then reached out to me. The relevance to Untappd is that they both share the same parent company (Next Glass) which picked up BeerAdvocate earlier this year and inevitably, they also now share some of their human resources.
Peeling back the layers a bit more, it's interesting to understand what the indicator of compromise was that alerted the (unhappy) BeerAdvocate user in the first place. With the caveat that I have nothing but circumstantial evidence to tie this person to the one who reached out to Next Glass, there's a thread on Reddit that aligns very closely to the facts of the matter:
In february 2020, I received an email from Netflix that I had signed up for an account. This was to an email address that is completely unique to beeradvocate (as is the custom I do with many sites I sign up for). Someone had registered a new Netflix account with my email / password associated with my BeerAdvocate account. This email address & password combination has existed only in two places: my memory and beeradvocate's database. Not even a password manager.
My going in position when contacted was that this would be yet another case of someone unfairly misattributing a breach to an organisation based purely on what they believe to be a unique email address or password being used in a way they didn't expect. I see this all the time and I literally have a blog post in progress titled "Has a Site Been Breached Because I Received an Email to an Address Unique to Them?" It details many different reasons for this behaviour that are entirely unrelated to a breach and in my experience, there is almost always a non-breach explanation. But not this time.
Plugging the email address in question into HIBP resulted in only a single hit:
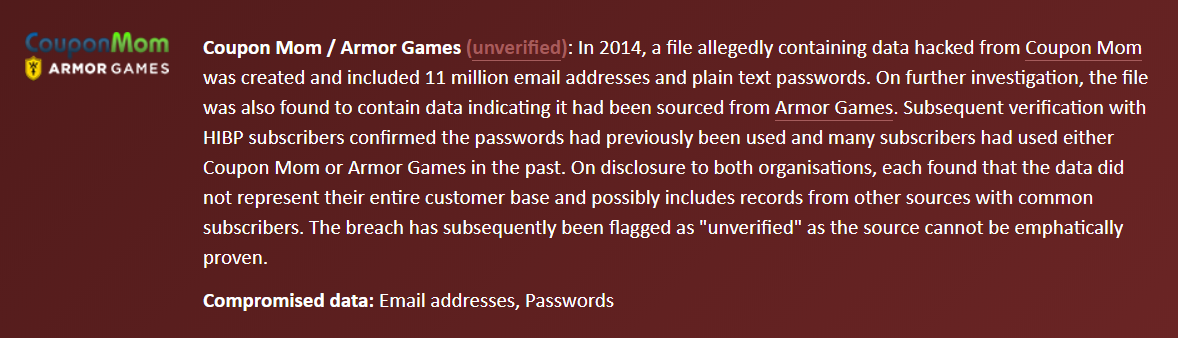
Unverified breaches are incidents where the data is legitimate (for example, people's real email addresses and passwords), but I haven't been able to confirm the legitimacy of the source. Per the description in the breach above, that incident definitely had data that could be traced back to both Coupon Mom and Armor Games, but what else might be in there? I pulled out the original breach and searched for "beeradvocate". 816 rows came back:
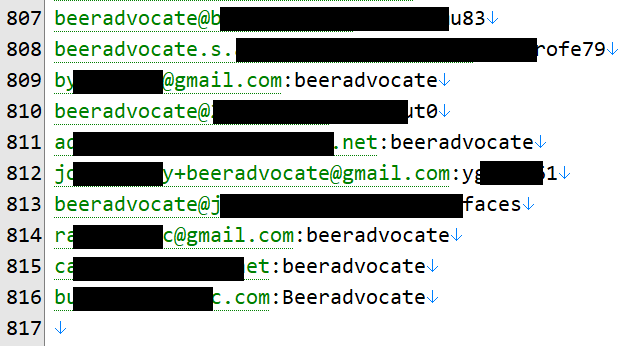
Well that's... damning. You simply don't have that many matches without there being a very high likelihood BeerAdvocate had suffered a data breach. For every one instance of an email address or password with the string "beeradvocate" in it there'll be another 100 instances that still came from their service but didn't use a customised email alias or (let's face it) very poorly chosen password. On the balance of evidence, they had indeed been breached and their data rolled in with at least the two other organisations into what was now effectively a credential stuffing list.
On Friday, BeerAdvocate / Next Glass contacted impacted customers and published a public disclosure notice:
After a thorough investigation from an independent third party cyber security firm, it was confirmed that BeerAdvocate user login credentials (email address, BeerAdvocate forum password) were lost and aggregated along with breaches of other websites into a breach dataset that became known as CouponMom 2014.
I'd argue that they're not lost, instead there's actually a lot of backups of them! They dated the breach back to "seven or eight years ago" and stated that "a since-retired password hashing method allowed some passwords to be derived". They don't state which algorithm was used, but it's a safe bet it was MD5 or SHA-1 which was already pretty fundamentally flawed by that time. I personally would have approached a number of things around this incident differently, but Next Glass still deserves some kudos for taking the concerns of the individual who raised this seriously and seeing it through to its conclusion, especially given they inherited this breach by virtue of the BeerAdvocate acquisition.
Just one more thing - I've often been asked why I don't discard the source data of a breach once processed and email addresses loaded into HIBP. Putting aside the fact that discarding it doesn't actually make it go away (a quick search found this data still being extensively traded), historical breaches can be enormously useful in establishing the origin of subsequent breaches. This incident exemplifies that and without ready access to this data I don't know that BeerAdvocate would have established the breach, notified their customers and given them the opportunity to go and change that same one password they use across all their other accounts...
Cheers! 🍺