Let’s go through just some of the ways you can hand your valuable datas over to people that want to get somewhere in between you and whatever service it is you want to talk to at the other end.
You can get pineappled and certainly that’s been a favourite of mine to demonstrate because it’s just so damn easy (it’s also kinda cool, if I’m honest).
The router you connect through can be pwned and its DNS changed to help pay for Brazilian hookers (yes, you read that right).
The Tunisian government can just siphon up all your packets as they pass through the ISPs under their control. Ok, maybe you’re not in Tunisia, but I think we’re all a little wary of the American government lately too…
And so on and so forth. I saw a great story today on the risks of public wifi which puts the threat of a man in the middle attack (henceforth an MitM attack) into perspective. As an iOS user, when I read stuff like China's Massive iCloud Hack, I get a little concerned. As an iOS user travelling to China, I get a VPN and that’s where Cloak comes in.
There are many consumer-orientated VPN service and I’m told that many of them are excellent, which I’m sure they are. I decided to give Cloak a go in part because their website made it super simple to understand, in part because the Twitter account actually reached out and made contact when I mentioned it (pro tip: this matters to a lot of people) and also in part because it has a free intro and good pricing plan. It was only after I started using it that I found some other neat tricks as well. It’s a dead simple app and it looks like this:
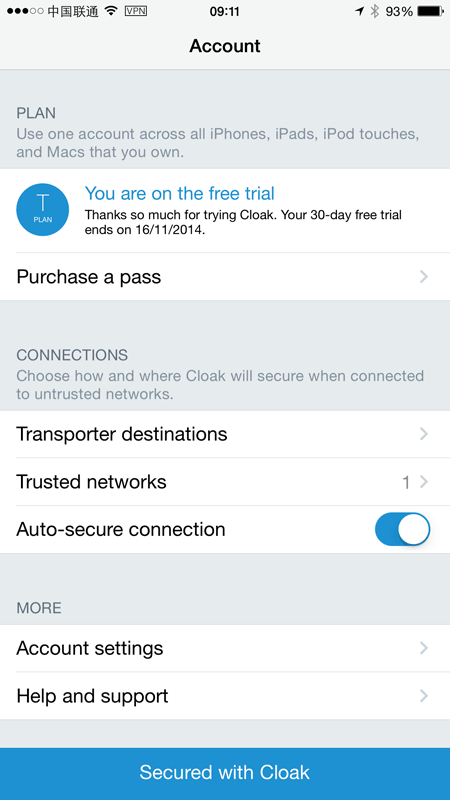
This is really, really simply and that’s what really got me excited about Cloak, not much more than the plan you’re on and a few basic settings. Let’s go through them.
Trusted networks
Cloak has this concept of a “Trusted Network”, that is ones that you don’t feel you need a VPN service on. Keep in mind what this does and does not mean though; I “trust” my home network but once the traffic goes out the door on copper wire, it’s game on. Conversely, when you’re on VPN it’s game on when the packets hit the exit node at the VPN provider. Still a risk, just different. My trusted networks look like this:
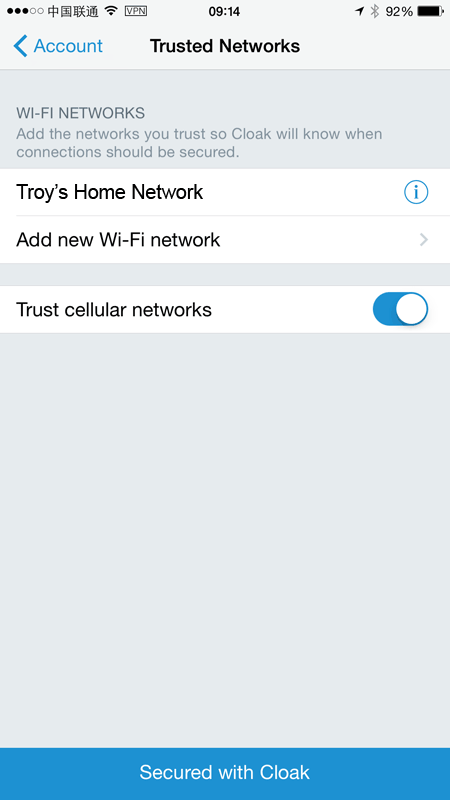
Note how cellular networks are trusted by default. Note also that this doesn’t mean you can always trust cellular networks (hi Iran!), but they usually don’t pose the same risk as your random local cafe wifi network, particularly the ones with zero encryption on them.
Anyway, the idea that by defining a whitelist of trusted networks you can have Cloak auto-enable when you connect to an untrusted network. This is enormously cool as it allows you to approach free wireless hotspots with reckless abandon. Ok, maybe not too reckless, you need a connection before the VPN kicks in and there’s always that little gap where traffic may traverse an unencrypted network, but it certainly gives you the option to browse via foreign networks with a confidence that you wouldn’t otherwise have.
When you connect to a network that’s not on Cloak’s whitelist, you’ll see the VPN connecting in the settings:
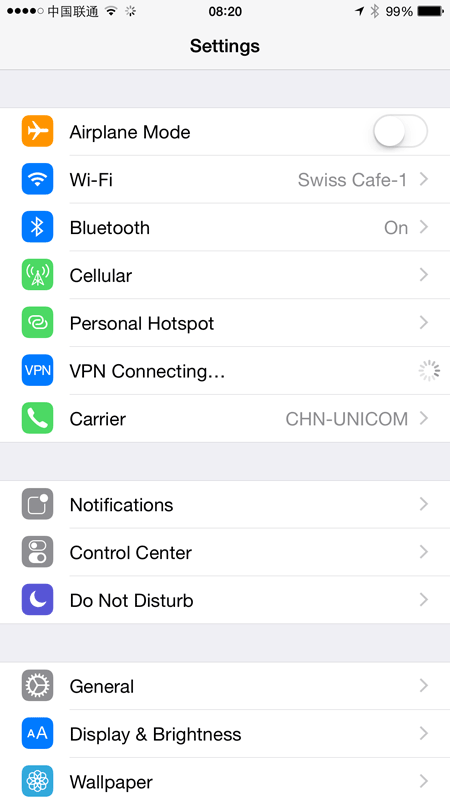
Sometimes it’s mere seconds, other times… it never happens. China in particular is notorious for blocking VPNs (it turns they’re just a little too effective for the government’s liking sometimes) and I found it to be very unstable a lot of the time. Then again, I found my corporate VPN service on my laptop to be unstable and the hotel wifi to be generally flaky so don’t let that cast a dispersion on Cloak. In earlier testing, I found Cloak rock solid all day long on stable wireless networks so I’m pretty sure where the blame for instability lies.
Once connected, you get iOS’ standard VPN indicator up next to the network connection indicator:

You can confirm the connection is secured by jumping back over to the Cloak app. This was my first test when I hit the airport in Sydney:
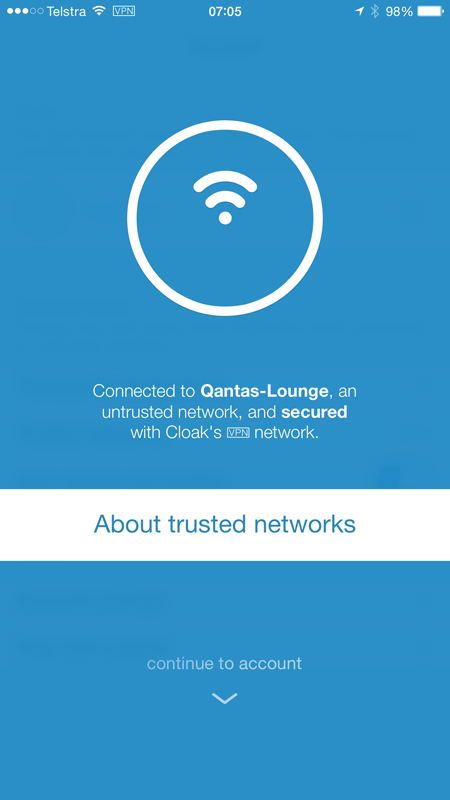
That’s it – now everything between the device and the VPN provider is encrypted.
Speed
You’re always going to take a hit on speed with a VPN, you have to. It’s not just the encryption process, but now rather than going from your service provider to destination address via the most efficient route possible, you’re going from your service provider to a VPN exit node to the destination address. How far that exit node is from either the origin or the target can have an impact on speed.
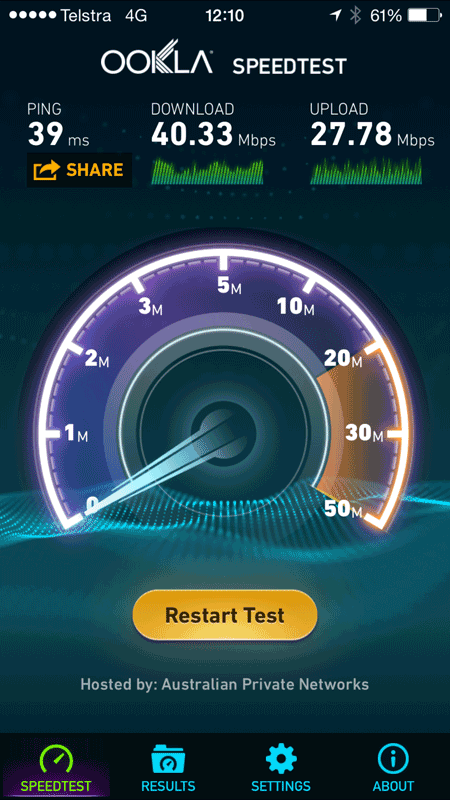
Here’s a good example: before leaving Sydney I enable Cloak over my 4G connection and ran a speed test. Here’s no VPN:
Now here’s Cloak in action:
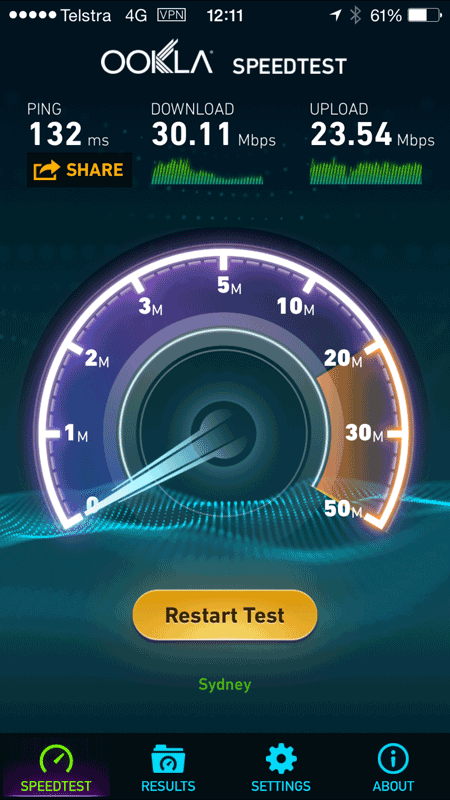
Keeping in mind that speed tests can fluctuate at the best of times, the latency has more than tripled and consequently I’ve lost a quarter of my down speed and about 15% of my up speed. But I’m still getting 30Mbps over Cloak which frankly, is pretty darn good (at least by Australian network standards).
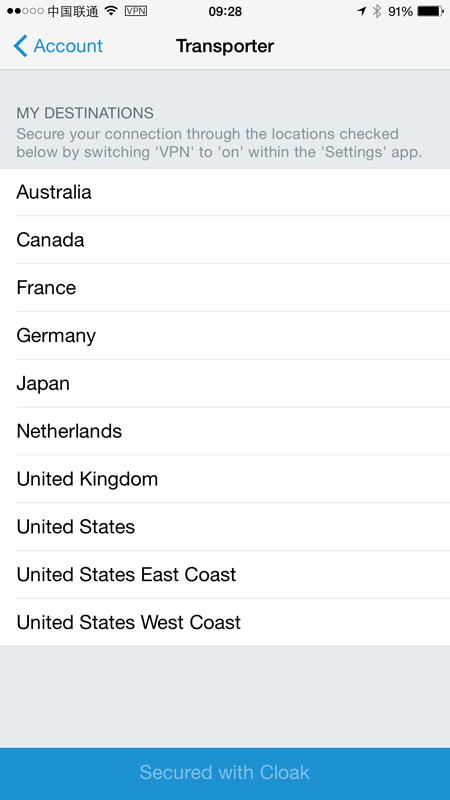
Transporter destinations
The idea of a transporter destination is an exit node for the VPN. If I exit through Sydney then firstly, it’s a short hop if I’m already there and secondly, I get a Sydney IP address accompanying my outbound packets. Change the transporter destination and I get a different IP in a different location.
Here’s what’s available:
Once I select, say, “Australia”, I’ll need to update the device with a new profile:
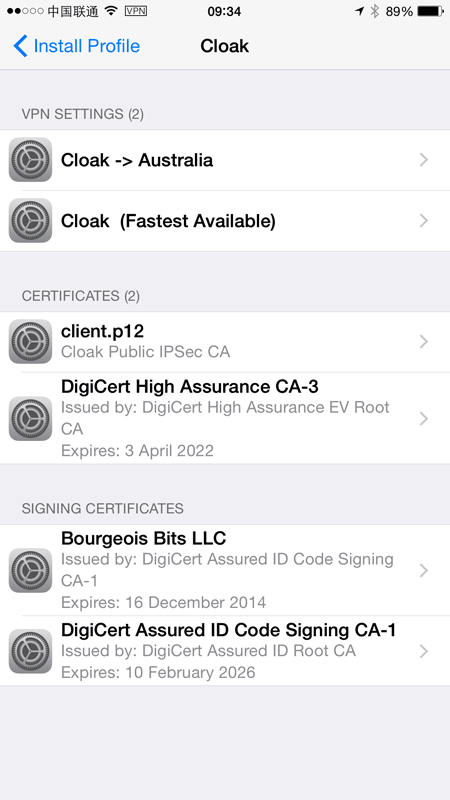
We can see here that there are now two VPN settings: the Australia one I just selected and “Fastest Available” which is the default position. This just makes sense – make things go through what is inevitably the closest exit node or alternatively, specify your own which may be some distance away but gets you outbound in your country of choice.
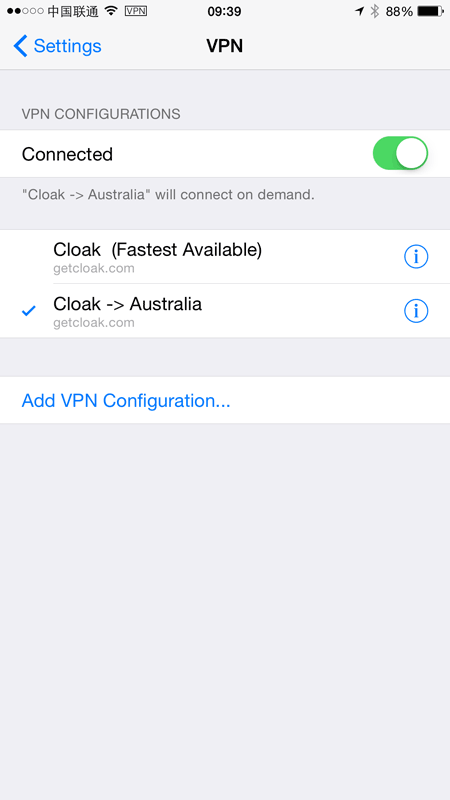
That done, I can now select the VPN profile I’d prefer from the iOS settings:
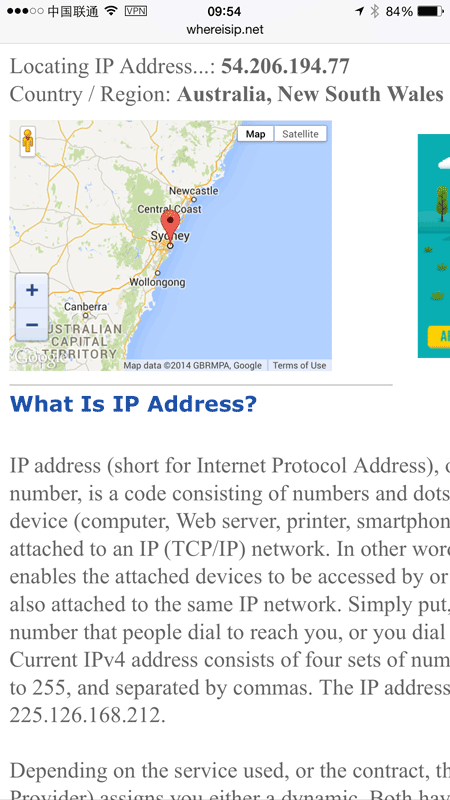
Which means that when I check my IP address, it feels just like home:
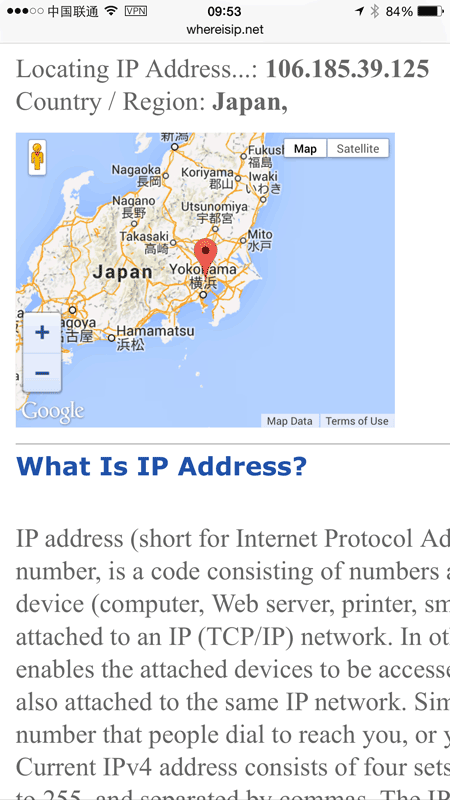
Go back to the fastest location and I’m in Japan which would be the closest node to my Beijing internet connection:
Switching takes only a few seconds so it’s a very, very low-friction exercise. I ended up leaving Cloak connecting via the fastest possible route because for my purposes, my main concern is keeping the clear traffic off China networks (because we really trust the American ones that much more…) and getting access to the services I want which are accessible from pretty much everywhere outside China.
Exiting from a location other than one in close proximity can be enormously advantageous. For example, China isn’t real keen on Twitter and Facebook so I don’t want my traffic exiting from anywhere there, instead I want it going out from somewhere more friendly to free-flowing social media; Japan isn’t too far away and doesn’t impose the same restrictions.
Syncing
I use both my iPhone and my iPad extensively and one of the things I like about the Apple ecosystem (and to be fair, others do this too), is the unified experience across my devices. My bookmarks, my photos and most of my iThings line up nicely across the two. Cloak also syncs settings and once a change is made, prompts me to sync things via a notification at the bottom of the screen:
I sync, open Cloak on the iPad and see this:
Tapping the notification in the footer downloads the updated profiles and now everything lines up just nicely across devices. In this case, I now have the Australian transporter destination on the tablet.
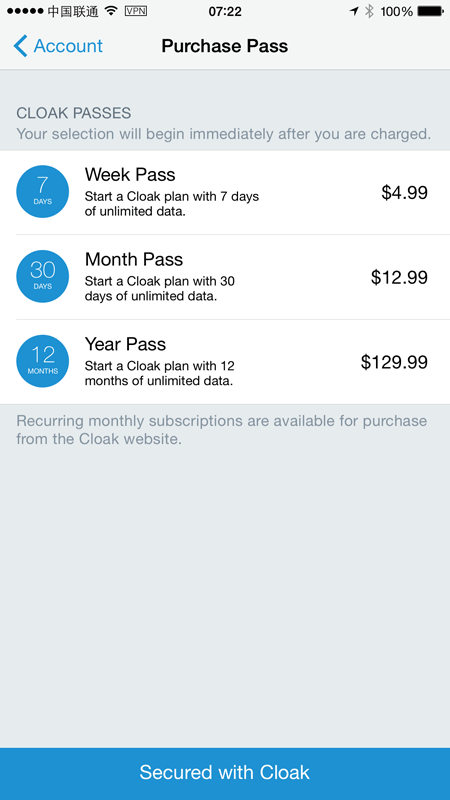
Plans
I mentioned being keen on Cloak because I could get a free demo, but frankly the cost is inconsequential anyway. I’m prone to comparing the cost of cheap things to my cappuccino budget and for a week away in China, we’re looking at less than two cups:
The thing I love about this model is the “Week pass”. I spend most of my time at home on trusted networks so I don’t need an ongoing subscription, but I also regularly travel to places where I don’t trust the network or I need to “be” in a different country. Being able to just fire it up for a week fits my movements just perfectly. Note there’s also unlimited data during that time too so it’s not going to chop me off if I decide to, say, update iOS on all my devices while travelling (which incidentally, I did just this week).
What a VPN won’t get you
Let me touch briefly on this and it’s by no means specific to Cloak. A VPN service like this won’t get you total anonymity. Yes, it can protect your data between your device and Cloak’s services, but remember you’ve identified yourself to Cloak (you need credentials) and they are now handling all your packets. They get subpoenaed for their records and you’d have to work on the assumption that your browsing habits would be accessible to law enforcement in their jurisdiction.
Your data exiting their VPN also has no implicit encryption. There are various precedents of data being intercepted well up the request pipeline (hi NSA!) and you have to work on the assumption that everything between Cloak and the service you’re connecting to is fair game.
As a rule of thumb, I don’t use VPNs for anything I wouldn’t normally do from my network at home. I don’t assume anonymity – there’s Tor for that and if you’re really keen, you can browse anonymously via that through your Cloak VPN.
Get Cloak
I wrote this because I go on about transport security enough that I wanted something I could recommend from firsthand experience in a location where you really need it. The only discussion I’ve had with the Cloak guys was via Twitter so this is as independent and as unincentivised as it gets.
Cloak rocks, get it.