Many people will disagree with this post, not so much because it's flat out wrong but because there are so many different approaches one can take. It's a very subjective realm but I'm going to put forward some suggestions, make some considered arguments and leave it at that.
The context is twofold as suggested by the title: Firstly, I get a lot of people asking me about how to get a start in the security industry. I've regularly reverted with "stay tuned, I'm writing something" and this blog post is it.
Secondly, over most of last year and the first half of this one, I've been creating material to help people who want to pursue security careers. It's the Ethical Hacking series on Pluralsight that sets people up to get their Certified Ethical Hacking cert (CEH). I want to talk candidly about CEH - both the good and the bad - and give people a path forward that can get them started in the industry.
Here's my experiences, what I think makes sense today and most importantly, here's the tools to make a start.
How I got my "start"
I want to begin here because many people ask me precisely this - how did I get started in security. In my case, it was entirely by accident, but let me explain anyway.
I've (almost) always been a web developer. I started writing software in '95 whilst at university and from day one, it was software for the web. There were a few years before that where I made pocket money working in various part time PC support roles but for the most part, it's always been about building software. I spent a decade and a half doing that before I really began to think seriously about specialising in security.
It was a very organic shift for me and it all began with this blog. In fact, I can tie it back to this exact blog post in 2010 where I began writing the OWASP Top 10 for .NET Developers series. I wanted to write this because I saw a need: developers had a very poor grasp on security and I wanted to articulate it in a way they could easily consume. That blog series lead to my first MVP award a year later which lead to the start of speaking at events which lead to Pluralsight which led to, well, all sorts of things.
All of this ultimately led to where I found myself earlier last year which I explain in How I optimised my life to make my job redundant. As I wrote more and spoke more and ran more workshops, the opportunities piled up. It was never planned - I never sat down and said "I think I'll have a career in security" - and all that makes my path here a bit unique.
I'm not going to recommend that anyone take the same path because it was such an organic thing that simply responded to the environment around me. Other people are in different environments and doing the same thing won't necessarily yield the same results. To be quite honest, the more I think about my journey the more I feel it's been because of the way I communicate and explain concepts than it is my knowledge of security specifically. That's probably a topic for another day though.
Be that as it may, let's look forward and talk about careers in the industry for folks who are perhaps able to plan it a little better than I did!
Infosec is hot
This is a great industry to be in and the timing has never been better than right now. By virtue of you being here reading this in the first place you're inevitably tuned in enough to see just how much security features in the news each day. To my mind, there's a perfect storm of factors contributing to this including the availability of cloud services (it's cheaper and easier than ever to stand things up), the rise and rise of IoT (more devices collecting more data about more things), the actions of Assange, Manning and Snowden (love 'em or hate 'em, they've had a profound impact on our views of online security and privacy), the rise of hacktivism (many of us have had our data leaked under this banner) and many, many other factors. The whole role of infosec in national security is another massive consideration at the moment but again, that's probably not telling you anything new.
There's been many quantitative pieces on the value of security jobs in recent times as well. Earlier this year Forbes talked about one million jobs openings in 2016 alone, 209k of those just in the US. In a report from last year on the state of job market, security roles were found to have "grown three times as fast as openings for IT jobs overall":
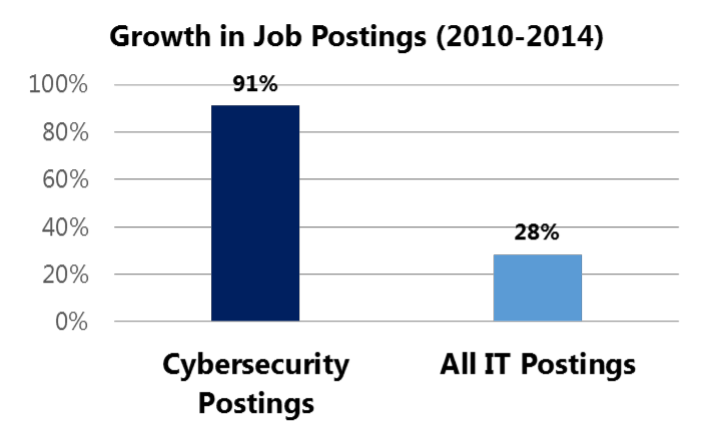
That's also reflected in how well rewarded security pros are; high demand with low supply means a premium salary package:
That’s bad for employers but good news for cybersecurity workers, who can command an average salary premium of nearly $6,500 per year, or 9% more than other IT workers.
I looked around for other figures to further illustrate the point and there's bucket loads of them but frankly, it all contributes to the resounding chorus of "security is hot, there's a heap of demand and it pays a lot of money". Let's get onto carving out a career in it.
Online identities are still a smart career move
I want to start here because I firmly believe that identity and personal brand are extremely valuable assets, regardless of where you choose to specialise. My first ever blog post was about why online identities are smart career moves and I wrote it whilst having a very diminutive presence compared to today. I didn't know how true that blog post would turn out to be and it's one of the first things I recommend people do these days.
Answer questions in places like the Security Stack Exchange site. If you don't know the answer, go and find it then answer it with references. If you have questions you don't know the answer to, ask them there. Just do something to start creating a presence.
Put code on GitHub. Make pull requests to other people's code. Branch interesting stuff. Get involved because all of these things lead to interactions with other people which leads to relationships which leads to opportunities.
Actively go out and create those relationships with others in the industry. Engage with them on Twitter, comment on their blog posts, meet them at user groups. Most people who've successfully made their way in whatever industry it is they've decided to specialise in happily answer questions when asked or take feedback on the things they've created. It gives you an opportunity to make connections.
All of this is free and you can start doing it right now. However, none of this is going to land you a job tomorrow; it will certainly improve your marketability over time, but it needs to be augmented with tangible skills which brings me to the next point.
Certifications and Ethical Hacking
There are many good dedicated security certifications out there that require various levels of investment in both time and money. For example, CISSP (Certified Information Systems Security Professional) is very popular among many security professionals. OSCP (Offensive Security Certified Professional) is another and by all accounts, it's amazingly in-depth and gruelling.
CEH (Certified Ethical Hacker) is the one I've been working on with Pluralsight and I want to start by explaining the background on how I got involved, not having previously done anything CEH related in the past. As I wrote about when I launched the first course in the series, Ethical Hacking content was the number one requested material on Pluralsight:
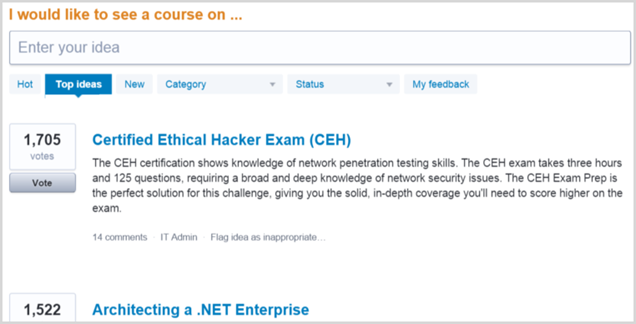
I was over in Salt Lake City in Feb last year for their author summit and they very enthusiastically approached me about writing some of what would ultimately become the 21 courses required to meet the CEH syllabus. I was initially reluctant as I knew very little about the cert and most of what I knew about CEH was from when they had their website defaced the year before! However, as I looked into it a few things began to resonate.
For one, the CEH certification is very broadly recognised and in some cases, required for certain roles. For example, the DoD expects to see it for all information assurance positions:
The United States of America Department of Defense issued Directive 8570 in 2004 to mandate baseline certifications for all Information Assurance “IA” positions. In February of 2010, this directive was enhanced to include the Certified Ethical Hacker across the Computer Network Defense Categories “CND”.
A trawl through the job ads will show many positions looking for CEH qualified individuals and certainly EC Council has made it a very well-recognised cert. I've heard this levelled as a criticism - that they've marketed the brand very well but the content lacks depth - which brings me to the next point.
When I looked at the syllabus of those 21 courses, there were a bunch of them which I thought would create really good standalone courses on Pluralsight regardless of their alignment to CEH. Further to that, many of them were in areas which I'd spent a lot of time teaching and writing about over the years. In fact, the very first course I ultimately created for the Ethical Hacking series was on injection, the same topic that first OWASP blog post had been on 5 years earlier. As I read through the syllabus, the idea of creating content on a number of the modules started to make a lot more sense. Pluralsight also recruited Dale Meredith whose been a Certified EC-Council Instructor for the last decade. He brought knowledge of the cert with him and tackled most of the non-web-centric content. Between the two of us we ultimately built 18 of the 21 courses, each working to our respective strengths (the other 3 courses were created by Jason Helmick and James Murray).
Ultimately, it boiled down to this: The content was very highly requested, the CEH cert very broadly recognised and there was a good chunk of the content I was already specialising in and had taught many time before.
The next issue was around how deep the material went and this is where I wanted to do things a bit differently. Dale and I discussed that at length many times with the folks from Pluralsight as well and I really wanted the content to go deeper than the reference material we were looking at from EC Council. To my mind, the content was very tool-centric so it would talk about using particular software products to mount attacks such as SQL injection. I really wanted people to understand the mechanics at a lower level so when I wrote the course I began with talking about the way queries and data are concatenated then went onto manual exploitation via parameter tampering then eventually, automated tools such as sqlmap. It meant that ultimately, that one course on injection was 5 and a half hours but IMHO, it was the right course to write. It's the SQL injection course I'd write whether CEH existed or not, which brings me to the next point.
One of the provisos of me doing the series was that I wanted every course to stand alone. For example, if someone is just interested in SQL injection and they go and watch that one course, they shouldn't miss out on anything by not doing the entire series. That's also why the courses talk about defensive practices; there's an entire module devoted to data validation, parameterisation, ORMs and so on and so forth because that's what a holistic course on the topic should do. This is the SQL injection course I wanted to write - they're all courses I ultimately wanted to write - which means this:
This is Pluralsight's most requested content ever. We've created the best courses we possibly could on discrete security topics and they're also a superset of the Ethical Hacking modules. This makes it easier than ever to skill-up on security in general and CEH content in particular.
I sum it up in this short interview about why I feel that technical depth is important:
"Be able to do and not just tell." — @troyhunt. Why we've launched a new security category: https://t.co/NWM3uNTHHM pic.twitter.com/4vN2YRaOPz
— Pluralsight (@pluralsight) July 27, 2016
So that's what we've created: over one and a half gruelling years with 8 courses from me, 10 from Dale and a few from the other guys with a combined total of 75 hours of viewing content. You can go through that material then sit your CEH exam with confidence and come out the other end of it as a Certified Ethical Hacker. The question people need to ask themselves though is if this cert makes sense for them and indeed if any cert does.
When a certification does (and does not) make sense
Certs are a means to an end. People get them because it helps them build knowledge and it helps them land a job. There are times when that makes sense and indeed there are times where it doesn't so let me give you an example of each.
If you're starting out in the industry and don't yet have experience to land you the job you're really after, a cert makes sense. In fact, even if you do have experience, a cert can be the thing that provides independent validation of your skills and sets you apart from the next candidate. It can also be a bargaining chip; demonstrated knowledge in the form of an independent assessment is another tick in the "strengths" column.
Where it makes less sense is when someone has that existing track record of demonstrated competency. It also makes less sense if they have the knowledge in these areas they want already; I don't see a lot of practical value in someone sitting their CEH just to get the title and continue doing the same thing in the same role (the exception here would be if that enables them to better negotiate their salary or working conditions).
The point is that you have to know what you're actually sitting the cert for. Further to that, it's important to recognise that this is a stepping stone in a career and indeed you could say the same about any cert or degree or other formal education. You don't do this, say "well that's that done", then settle in for a comfy life of fat pay packets. What any form of further education does is shows commitment; it shows you're serious enough about the discipline you've chosen that you're willing to invest the time, learn the content then demonstrate the knowledge, and that goes a long way with employers.
One last thing here and it's a bit of expectation management which was really clearly highlighted in a piece from last week about intensive coding schools. You're (almost certainly) not going to do any sort of education and with that alone come out and earn big bucks right away. Anyone that tells you elsewise probably has a motive that doesn't involve your best interests! A cert like CEH may open doors and create opportunities you wouldn't have had otherwise, but that's only part of the story.
Nothing beats experience!
This is why I wrote the section about online identities earlier on because that's a great way of demonstrating experience. Augment these things - do everything I wrote about there and do the cert thing and if you can go armed to a potential employer with both of those, you're starting to look pretty good.
Learning with Pluralsight
Lastly, if you've read this far and are thinking that maybe this might be the right path for you then let me talk a bit about Pluralsight. I obviously have a vested interest in people learning from them (I'm paid royalties based on course views), but this is my honest view on the best possible way to get started. I wouldn't have created the content if I wasn't fully endorsed in it.
What I like about Pluralsight's approach (and one of the reasons I started authoring for them 4 years ago), is that they're intent on making knowledge accessible to everyone. The commercial model for the licensing reflects this - you pay $29/m and you get access to everything. You can watch as much or as little as you like but for less than $1 a day, you can take courses such as those mentioned above then go and sit your CEH exam (note that EC Council still has a fee when you do the test).
Being online training, Pluralsight courses are self-paced. You can do them in the evenings, do them on the train on the way to work (you can take them offline as well) and indeed do them in the office as part of further education for your job. You can play them at 1.x speed (without me sounding like a chipmunk!) and you can pick and choose just the modules or clips you're actually interested in. Pluralsight has become enormously successful because this model of learning works so well for so many people.
There are obviously many different paths people take to arrive at their respective security jobs. Mine is totally different to what I've suggested here and as I mentioned earlier, I wouldn't exactly recommend that approach to anyone else. But as a means of getting started and doing so much so easily, I honestly can't think of a better way.
You can get started right now, Dale and I had a blast creating the content and we're enormously happy with the result!
