Here’s how it usually works: someone big gets hacked or a serious risk gets disclosed then all sorts of articles pop up with journos quoting people like myself on all the same questions that inevitably get asked. I’ve been doing a bit of that today in the wake of the eBay attack so I thought that rather than just have these one on one conversations which then get dispersed all over the place, I’d capture a bunch of responses from discussions I’ve had here.
Just one more thing – it’s very early days in the life of this incident, indeed it’s less than 24 hours since eBay asked everyone to change their passwords. With that in mind, here’s what people are asking and what I’ve been able to contribute to the discussion:
What happened?
It seems that the credentials of a number of employees were compromised which then allowed the attacker(s) to gain access to the eBay network and exfiltrate customer data including name, “encrypted” password, email and physical addresses, phone and date of birth. This appears to have happened some months ago in February and March but seems like it has only just been discovered now.
How did it happen?
Phishing attacks remain one of the most successful means of extracting credentials from people so that would be a likely candidate, as would the simple fact that people reuse credentials at an alarming rate and a compromise in one asset often leads to one in another (although I have no idea of eBay’s internal password rotation requirements). It’s not yet clear whether those credentials were sufficient for the attacker to gain access to internal systems directly without a second factor of authentication or not (i.e. did they need to VPN and an RSA token first).
What did eBay do wrong?
The most obvious answer is that they took a long time to detect the intrusion – two or three months by the look of it. Of course it was more than just an intrusion though, not only did the attackers gain access to eBay’s network with employees’ credentials, they also managed to exfiltrate the data without timely detection. That’s a topic that often comes up in infosec quarters – how well equipped is an organisation to identify when data is being pilfered? Perhaps not very…
How come credit card info wasn’t obtained?
In all likelihood, eBay applied very different security controls to their payment info to what they did their personal data. These are two very different classes of data and indeed they come under separate controls, namely payment card info being subject to PCI DSS. The data was quite likely sandboxed away in a different corner of the company’s infrastructure and was subject to different access controls. It’s not like the card data would have just been sitting there in database columns next to the other breached data.
By the same token, let’s re-read their message on this:
we have no evidence that any customer financial or credit card information was involved
What’s being implied here is that absence of evidence is evidence of absence and that’s not always the case. There have been many prior examples where attacks have occurred and companies issued statements on the scope of the breach only to revise it upwards shortly thereafter, sometimes multiple times.
Could other data within eBay have been accessed?
A common practice among attackers is to “pivot” between various services within a compromised environment. For example, credentials may have granted access to the web application which enabled the retrieval of user data, could that information have then been used to move laterally between other services and pull other classes of data? Quite possibly and inevitably the ability to do this is quite common, particularly in larger organisations with a broad range of services.
The most pertinent question in eBay’s case is if this activity was even detectable. Particularly if it was occurring under legitimate employee identities, what degree of confidence do they have that requests orchestrated by the attacker were actually captured and can be identified? Conceivably, yes, other data could have been accessed but without confirmation (or emphatic denial) from eBay, we can only speculate.
Were the passwords “encrypted” or “hashed”?
It’s always hard to tell because the terms are used so interchangeably when they are in fact two very different, very discrete cryptographic processes. eBay has said (emphasis mine):
As a result, a database containing encrypted password and other non-financial data was compromised.
You’d hope that what they really meant was “strongly hashed” passwords but we need to appreciate that phrasing it this was doesn’t resonate quite as well with the predominantly consumer audience they’re speaking to in their announcement. Yes, they’re asking people to change their passwords and that may read as though they don’t have sufficient confidence in their cryptography implementation (exposed key or weak hashing algorithm), but of course this is also an arse-covering exercise on their behalf.
Shouldn’t they just have reset everyone’s password for them?
We don’t usually see this done and particularly in eBay’s case it would be a hard argument to make. Firstly, if the passwords were stored cryptographically and there’s a reasonable degree of confidence that they couldn’t be reverted to plain text, a reset may be overkill. Of course they’ll still ask customers to change it themselves (see the previously mentioned arse-covering), but it may have little real impact.
Secondly, you’re talking about sending 145M password reset emails and asking everyone to come to ebay.com at around the same time and perform a CPU intensive process via a (hopefully) cryptographically laborious hashing algorithm. This has all sorts of ramifications on the availability of a service the scale of eBay’s and may well lead to them effectively DDoS’ing themselves. Incidentally, eBay password resets require you to verify your identity via email or SMS first so at least the attacker can’t just change someone’s password without first compromising other services as well.
Thirdly, if they were genuinely worried about attackers logging in with stolen credentials then they’d be issuing a pretty immediate reset which has serious usability implications for people using the system. Not only is that painful in terms of user experience, but it would inevitably cause a massive spike in the number of support calls they had. Again, lots of ramifications.
Who could have done this?
What’s intriguing about this situation is that the data does not appear to have surfaced within any sort of short timeframe of when it was obtained. It hasn’t turned up on Pastebin or any of the usual hacktivists haunts and indeed you’d expect eBay to be able to protect this sort of info from script kiddies with too much time on their hands. It’s unlikely that it was an opportunist attack like, say, Bell.
Then there are the career criminals; these are the guys who make a living out of compromising data and then selling it. But if that was the case, we’d have likely seen this issue surface much earlier as we did with Target and in many more incidents beforehand. Granted, credit cards apparently weren’t exposed but even the data that was alleged to have been breached has value on the underground. It’s quite possible that it wasn’t criminals or that they simply didn’t obtain data of sufficient value.
Which leaves that other class of attacker – the nation state. We’ve all pretty much accepted that our worst fears regarding government intrusion have well and truly been realised in the past so that’s certainly a possibility and indeed they’d have the resources to find ways into anywhere they set their minds to. I don’t necessarily mean the NSA (remember when we used to be worried about China?!), but the simple fact that you have 145M people in one of the world’s largest market places inevitably poses as an attractive proposition to many different state actors.
What else could they have done?
It’s hard to say without knowing the details so I can only speculate based on what we know. The most obvious omission in their publicly facing web presence is the lack of two factor authentication. In my view, we’re fast approaching an era reminiscent of when SSL began gaining such prominence all those years ago – if valuable web assets aren't implementing 2FA, customers are increasingly dissatisfied. Whilst not necessarily helping to avoid this current incident, 2FA significantly mitigates the impact if passwords were indeed retrieved and cracked. Incidentally, PayPal has a 2FA implementation already so at least that option is available on the money side of most eBay interactions.
Edit: Apparently the 2FA from PayPal can also be used with eBay. There’s no info on the eBay password page about this nor on the page about how to create a password.
Clearly the other major question they’ll be asking is if they couldn’t have done more to keep the attackers out of the network if they did indeed use staff credentials and the answer is easy in retrospect – “yes”! What they can do differently will, of course, depend on the attack vector used but clearly there is a deficiency. Same again in terms of their data exfiltration detection – if large swathes of data existed the premises, should they not have known about it earlier? Probably.
And finally, should the compromised staff accounts have ever had this much access to such a large volume of valuable data? I mean should, say, Mary in accounts be able to pull 145M identities out of the system? It’s still not clear how many records were compromised but clearly it was enough to constitute a major incident that may have been avoided by more stringently applying the principle of least privilege.
At least it’s easy to change the password to a secure one, right?
No. Barely a week after writing about The “Cobra Effect” that is disabling paste on password fields, I find that I cannot copy out a strong, random password from my favourite password manager but must instead manually type in a subset of the characters (my usual length is infeasible to manually enter – twice). So I type it all in and…
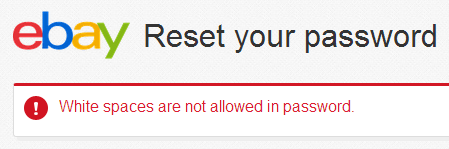
Great, so let’s dumb it down a bit more so I try this one:
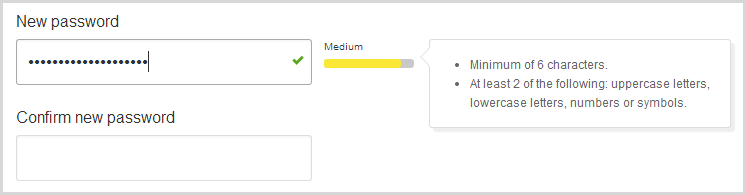
,83eQYr$m76H>ojqj[Em
Secure? 20 random chars with at least four lowercase, four uppercase, four numbers and four symbols – this is must be some sort of super password, right? No, apparently it’s just a medium strength:
Of course this begs the question – what does constitute a strong password? Fortunately eBay can help you with this handy tip sheet:
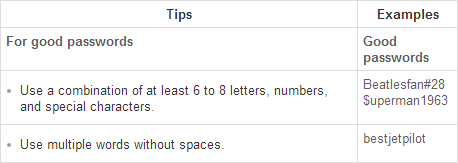
Aha! So naturally I immediately go to change my password to “bestjetpilot”:
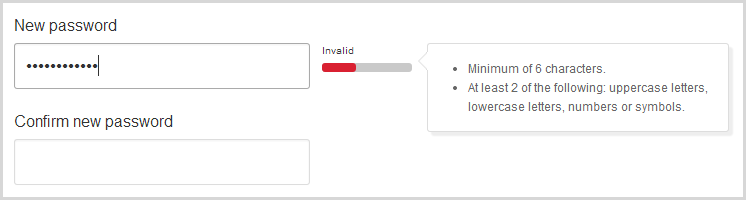
Well how about that – invalid. But I followed the instructions!
Interestingly, that’s the guidance on the .com.au domain’s password page but it doesn’t appear on the .com or .co.uk pages. Down here, we also get this very handy advice:
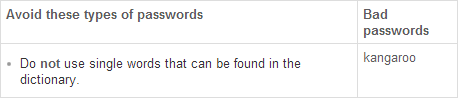
Crikey! No bloody kangaroos in my flaming password?!
I’ve admittedly diverged from the intended topic a little here but the point is that eBay has some work to do with how it communicates and implements passwords.
What else can we expect to see happen as a result of this attack?
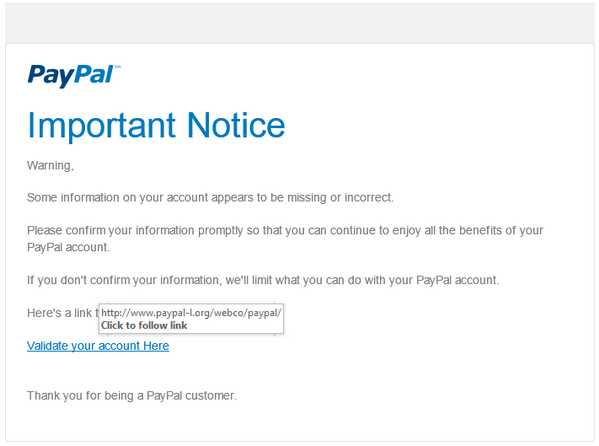
An inevitability after an event like this is that phishing attacks will ramp up dramatically. We see plenty targeting eBay already at the best of times, but we can expect to see many more like this one which has already come in since the breach:
Indeed eBay has referred to just such a risk in its announcement of the breach:
Following a cyberattack of this nature, it is common that fraudsters will try to exploit well-known brand names like eBay in an effort to obtain personal information. They attempt this fraudulent activity through phishing emails, texts, phone calls and fake websites.
Attacks like these get an added air of legitimacy in the wake of an event where people are expecting notifications and they are inevitably less suspicious when one arrives. Of course the same old guidance applies and the easiest way to avoid a phish like this is to simply type in the ebay.com address directly into the browser yourself and not trust any links in email.
How do we stop this happening again?
We (as an industry) are frequently too sloppy when it comes to our software implementations, of that there is no doubt. But let us also not lose sight of the magnitude of what we’re talking about here: eBay is making it possible for two and a half billion internet connected people to browse through over 100 million items in an online store from tens of thousands of kilometres away over a connection reaching speeds approaching that at which light travels. All the bits that go into this are an enormous engineering feat that we often forget as the technology becomes so mainstream.
The point is that there are a lot of moving parts solving often complex problems and that there will always be points of weakness in computer systems. Remember the enormous hurdles Stuxnet overcame only a few years ago and whist the eBay attack may well not have been this sophisticated, the point is that seemingly impenetrable security can be overcome with enough resources. For eBay, the question is not whether they can stop this from happening again, but whether their measures were “reasonable” enough and that’s a story that’s going to take a while to play out.