Well we almost made it through the first day of the new year without a major data breach; it got to about mid-afternoon my time then wammo! The 2014 breach count was off and racing.
If I’m honest, I actually spent some procrastinating over whether this could really be considered a breach and indeed if the data was even of any functional value to an attacker. I came to the conclusion that it is and, well, it is. Let me explain the thinking and why I’ve made it searchable via Have I been pwned? (HIBP).
Within the last 24 hours we saw the “breach” of 4.6 million Snapchat phone numbers and usernames:
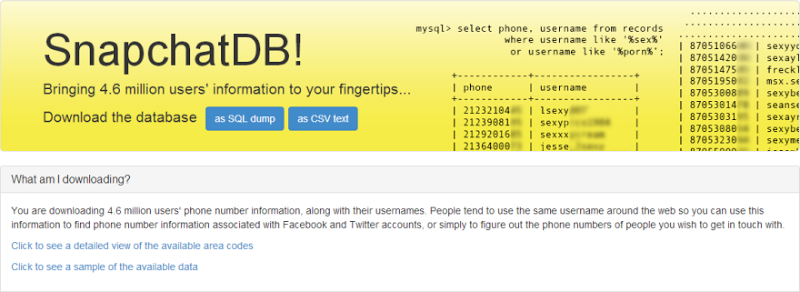
Often we’ll see such breaches come by exploiting vulnerabilities like SQL injection or by gaining remote access to the server environment but in this case, the exploit appears to tie back to research published by Gibson Security last week. The information at present seems to indicate that the data was obtained by using a simple enumeration technique against the API that sits behind the mobile apps. Ask the mobile app about a phone number, get back a result with a username. Increment the phone number by one and repeat. Lots.
I actually spoke recently at Microsoft’s TechEd about the risks in APIs behind mobile apps and this is exactly the sort of thing I was talking about. Easy to consume, fast to enumerate and frequently poorly secured. But I digress, let’s get back to the breach.
It’s not like Snapchat were unaware of this risk which really makes it all the more puzzling, in fact in response to the aforementioned research they released a statement a couple of days later:
Theoretically, if someone were able to upload a huge set of phone numbers, like every number in an area code, or every possible number in the U.S., they could create a database of the results and match usernames to phone numbers that way. Over the past year we’ve implemented various safeguards to make it more difficult to do. We recently added additional counter-measures and continue to make improvements to combat spam and abuse.
“Theoretically”, does not a good security defence make! In practice, there’s clearly a gaping hole in their API and whilst I get it – their model depends on searching by phone number – I’ll go out on a limb here and say that I doubt users of the system would expect their identity could be so easily compromised by anyone who knows how to increment a phone number. Theoretically.
How might usernames and phone numbers be exploited?
What risks do leaked usernames and phone numbers pose? In the US at least (and that seems to be where the bulk of the data is from), the mobile number gives you a location as an area code on land lines in other countries would (at least that’s my understanding). More than that though, the association of username to phone number starts to open doors to social engineering attacks: “You’re receiving this SMS from Snapchat and we need you to verify your password for account johnsmith”.
But exploits against Snapchat is the obvious one, let’s not limit ourselves here. Oftentimes, usernames are unique enough to have a reasonable degree of confidence (the definition of which will differ from case to case), that the same one in multiple locations does indeed belong to the same person. What this breach (yes, that’s a reasonable term to use), gives an attacker is the ability to start resolving other accounts to phone numbers.
For example, let’s take “mralexgray” who was in the Snapchat breach with phone number 91728484XX (the publicly leaked data obfuscated the last two numbers) and is located in New York. Now that’s a relatively unique username, let’s plug it into Facebook and see what we get:
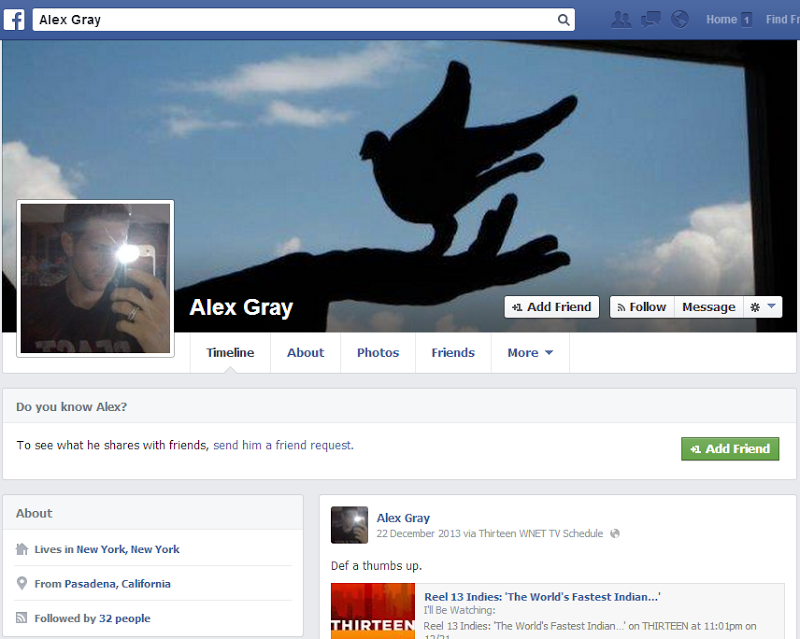
Lives in… well there you go. Now Alex’s Facebook profile is public and that’s just fine, but he may well not have wanted his mobile number being made public but by virtue of shared username, those two pieces of data now make up his public profile. You can extend this logic to many other breached accounts across many other entirely independent services that are tied together by common username.
What’s the value of learning you’ve been pwned?
Most times, when someone finds they have an account that’s been compromised by using HIBP, they can take fairly affirmative action. Changing their password on the impacted site is the obvious one, changing it on the other sites they’ve reused it across is the (unfortunate) other common one, but what do you do if your phone number is in the Snapchat breach? Change it?
Of course not, at least not in most circumstances. But it does give users in the breach the opportunity to consider what the impact may be. For some, a phone number is a personal piece of data they work hard to keep private and this breach may result in a heightened awareness of potential abuse. It may result in exercising extra caution – particularly in the short term – with regards to potential attacks that leverage the fact their online identities may now well have a unique phone number tied back to them.
The other angle is that when someone finds their account pwned, it brings the whole issue of trust and security on the web back to the front of their mind. We willingly hand over information every day and it’s usually not until we see it breached and out there on public display that the potential ramifications of laissez faire sharing of data combined with sub-par application security really hits home. This is a reminder for all of us.
Searching HIBP by username
In order to make this data searchable, I had to extend the concept of searching by email such that you can search by any string. It means you can do this:
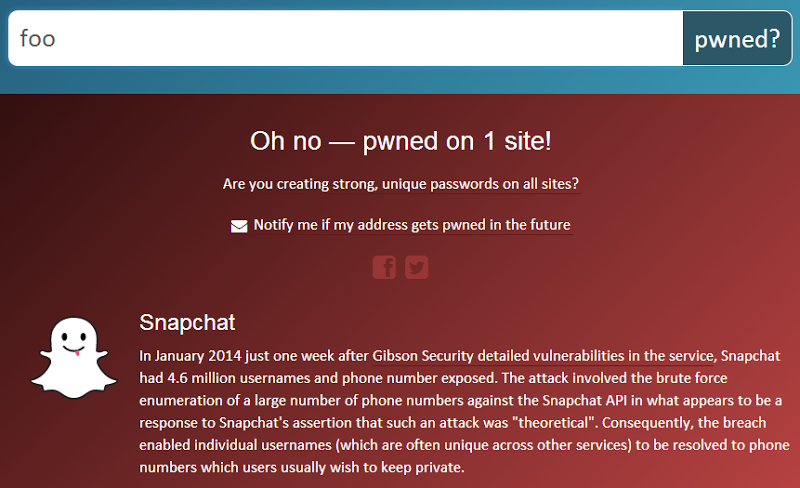
Over time, I’ll add the usernames from other data breaches I’ve already imported (at least where the username is not simply the email address), which will make it a lot easier both for impacted users to find breaches and to add subsequent breaches of a similar nature to this. Obviously searching by username is not quite as precise as email (two different people could use the same username on two different websites), but it’s usually enough for an individual to decide if their account was compromised on a particular service.
Subscribing to notifications when your account is breached
The free notification service I launched only nine days ago is going strong with many thousands of subscribers already signed up which I reckon is a pretty good result for the holiday period. It’s still free (and I’ve every intention of keeping it that way) and you can still sign up with only an email address and you’ll get automatically notified if it appears in a subsequent breach on any website loaded into HIBP.
I’m thinking about how to build notifications of breached usernames into this service as well. Right now I’m halfway through building domain-wide searches (i.e. tell me all the emails that have been pwned @troyhunt.com) but I can see a lot of value in the username notifications too so facilitating that is definitely front of mind.
Go forth and search for pwnage
That’s it for now – Snapchat joins Adobe and half a dozen others that have had the misfortunate to be compromised and customer data exposed so go forth and search and subscribe.