It’s the Low Orbit Ion Cannon and yes, you can be arrested and sentenced to a prison term for using it to mount a distributed denial of service attack on a website. But let’s not get ahead of ourselves, there are a few things to understand first.
LOIC has shot to fame in recent years as the tool of choice for what we colloquially refer to as hacktivists, or in other words, folks with an axe to grind – usually for political purposes – who use the web to express their displeasure. They’ll usually be anonymous (that’s with a little “a”) and may associate themselves with groups such as Anonymous (with a big “A”) or others such as LulzSec and UGNazi. The names or how active they presently are isn’t really the point though, I’m interested in looking at the nature of DDoS as this is where I see a lot of misunderstanding.
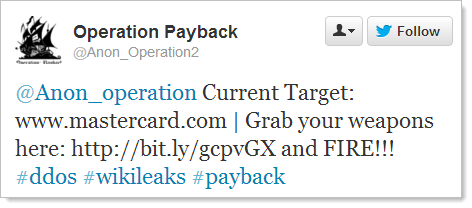
Here’s how it often begins, with a call to action for hacktivists to join in an organised DDoS:
The result can be devastating for the target; MasterCard suffered major outages on at least two different occasions as a result of this a couple of years back. There have been countless DDoS attacks by hacktivists since, the latest newsworthy event being the takedown of the US sentencing commission website just this weekend in retaliation for the legal action against Aaron Swartz, undoubtedly a contributing factor to his recent tragic suicide.
But the results can also be devastating for those involved in orchestrating these attacks. This is Christopher “Nerdo” Weatherhead:

Chris was 20 years old when he was involved in the MasterCard attack. Last month (two years after the attack) he was convicted of conspiracy to impair the operation of computers and faced the prospect of up to 10 years in jail. Last week he was sentenced to 18 months imprisonment. Prosecutors described Chris as “a cyber-criminal who waged a sophisticated and orchestrated campaign of online attacks on the computer systems of several major companies" and alleged the actions he was a part of caused damages of £3.5 million.
Hopefully that sets the scene as to the significance of this kind of attack, let’s take a look at the mechanics of LOIC, DDoS and the possible ramifications for those who want to get involved.
Understanding DDoS
Let’s start with the basics; in layman’s terms, a denial of service attack is the web equivalent of trying to squeeze a whole bunch of fat blokes through a single revolving door in one go. Throw enough of the big fellas at the door at once and nobody else will be able to use it. The denial of service on the door is effective both because of the nature of the payload (the larger gentleman) and the volume (the fact there were many of them).
As it relates to websites, a DoS substitutes the big guys for data packets and the door for the network interface to the web server. In other words, if you can flood the web server with enough junk data then it struggles to serve legitimate requests. DoS tools will typically multithread the connections and depending on the protocol used (usually TCP, UDP or HTTP) form the requests in such a way as to cause maximum workload on the target all in the name of making the attack as effective as possible.
A distributed DoS or DDoS is when the process is spread out over multiple clients all sending junk data to the web server. Naturally 10 clients sending is going to have a significantly greater impact than a single one. Now make that 1,000 or 10,000 clients and you start to see how valuable crowdsourcing is to the would be DDoS’er.
Maximising the effectiveness of a DDoS
The effectiveness of a DDoS attack tends to be measured in both the rate of data flooding the target and the duration it lasts for. More of each obviously makes the attack more effective. In terms of rate, just sending standard old HTTP requests alone to a web server isn’t real efficient and there are a number of ways of stepping things up.
One of the key objectives of a DDoS is to increase the workload the server has to do in order to process the request. If you can make the server work hard enough it will struggle to serve legitimate requests even if the actual volume of data it’s receiving is not high. A common approach is to issue malformed requests which depending on the server being targeted, can significantly increase the workload involved in processing them. Cisco talks about a number of different styles of DDoS attack including Teardrop:
While a packet is traveling from the source machine to the destination machine, it may be broken up into smaller fragments, through the process of fragmentation. A Teardrop attack creates a stream of IP fragments with their offset field overloaded. The destination host that tries to reassemble these malformed fragments eventually crashes or reboots.
But it takes more than just a single stream of malformed packets, a successful DDoS also needs volume and common way of increasing volume is to launch an attack via botnets. A botnet is a collection of PCs infected with malware and controlled centrally by a “botmaster”. The botmaster will usually manage his minions via a command and control server or in other words, a central location that infected PCs phone home to in order to take instructions. ADK Research has a fantastic graphic on this:
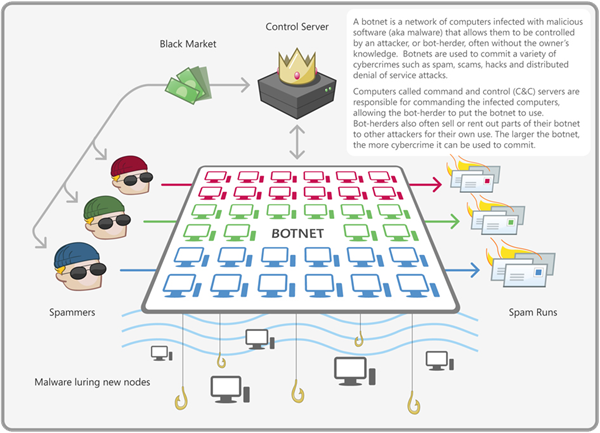
The relevance to DDoS is that a botmaster has an extensive capability at his fingertips; the number of infected machines could easily number in the thousands or tens of thousands (the Srizbi botnet allegedly contained 450,000 infected machines) and this provides him with enormous potential to mount a distributed attack. Of course this all happens from otherwise entirely innocent PCs distributed around the world, they’ve simply been infected with malware.
Going back to the infographic, botmasters commoditise their botnet by selling access to it via underground channels. And that’s really what it becomes – a commodity – one that someone can rent for a period of time for a sum of money. A few years back it was reported that the average price for renting a botnet for DDoS purposes was only $67 for a day. Of course rental prices will depend on factors such as the number of bots and their location, but you get the idea.
Another way of maximising DDoS effectiveness is via DNS amplification. There’s a great post over on the CloudFlare blog where they talk about this after an attack they had in September last year. They say the attack was 65Gbps which they liken to watching 3,400 HD TV channels at the same time. Put that in perspective; you’d normally consider a 20Mbps broadband connection to be fast and that’s precisely what they’re talking about – 3,400 of those maxed out. Simultaneously. Here’s what it does to traffic volumes:
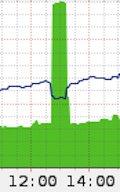
In short, the DNS amplification attack exploits misconfigured DNS resolvers which allow anyone to query them from anywhere using the UDP protocol and a forged header with the source IP of the target. What this means is that the DNS resolver sends a response back to the target rather than the original requestor. The amplification is achieved by making a small query that results in a large response. Multiply that out over a number of open DNS resolvers and only very small input is needed to result in large responses.
But there’s another way of maximising the effectiveness of a DDoS attack – crowdsourcing. This is where LOIC comes in as it leverages the power of a large number of simultaneous users, just like in the botnet example. The difference in this case, however, is that the LOIC users are willing participants.
So getting back to LOIC…
The thing about LOIC is that it makes mounting a DoS attack really easy. First of all, the software is freely available and you can easily grab it off SourceForge. When you fire it up everything is in a nice friendly GUI:
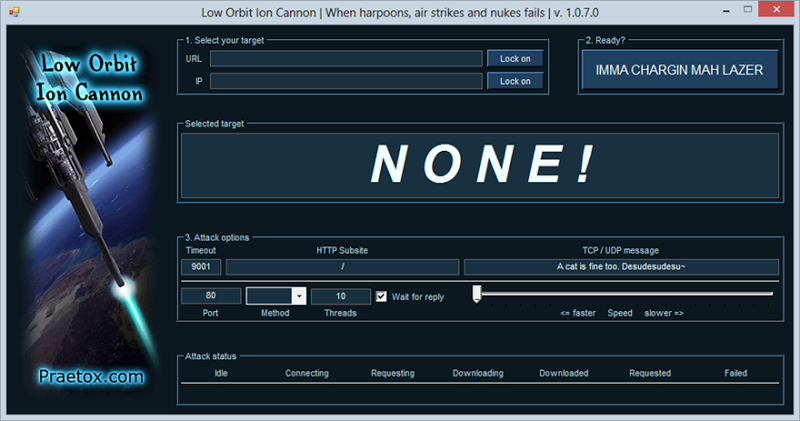
Enter a URL, choose an attack method (TCP, UDP, HTTP), hit “IMMA CHARGIN MAH LAZER” then watch it fly:
That’s all of about 60 seconds to download, configure then begin attacking. Plus it has a bit of fun with you if you screw something up:

There’s a little bit of configurability but for the most part it’s literally just point and shoot. If all that seems too hard then you can even grab Hive Mind LOIC from SourceForge and configure it to be orchestrated by IRC or RSS:
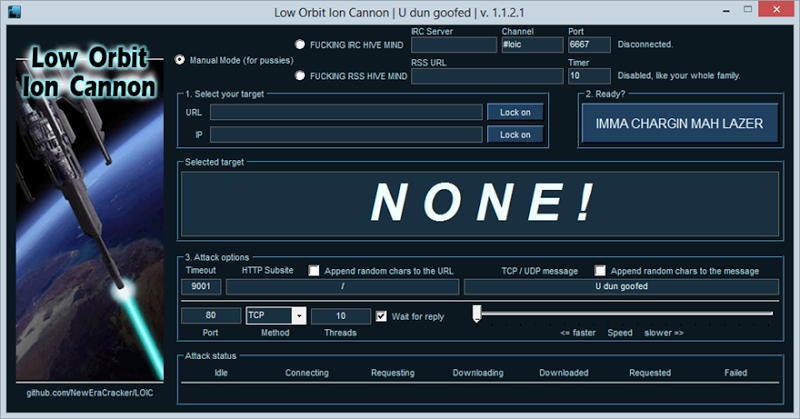
In other words, allow someone else to control the DDoS attack using your PC as one of the attackers. Trustwave has a piece on LOIC DDoS Analysis and Detection where they identify a typical IRC-driven command as follows:
!lazor default targethost=www.moneybookers.com subsite=/ speed=3 threads=15 method=tcp wait=false random=true checked=false message=Sweet_dreams_from_AnonOPs port=80 start
Obviously this just includes all the parameters of the attack which Hive Mind then pulls from IRC then gladly executes. The target could be anything and the attack happens without any direct involvement from the individual who installed the software but of course it does come from their machine – and their IP address.
One thing about both these variants of LOIC is that they’ll make your antivirus a bit unhappy:
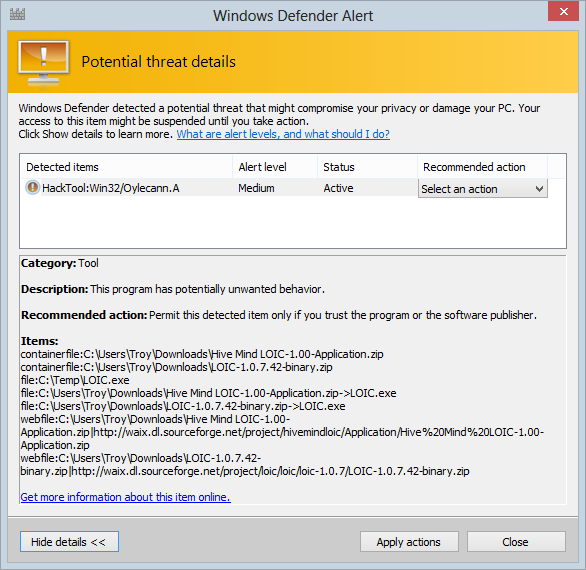
Microsoft’s Malware Protection Centre reports it as:
HackTool:Win32/Oylecann.A is a tool that may be used to send a flood of network packets, like TCP, UDP and HTTP, to a designated target.
Sounds about right! If that’s concerning to anyone or they simply didn’t have the desire to install software of this nature on their machine, there’s always JS LOIC:
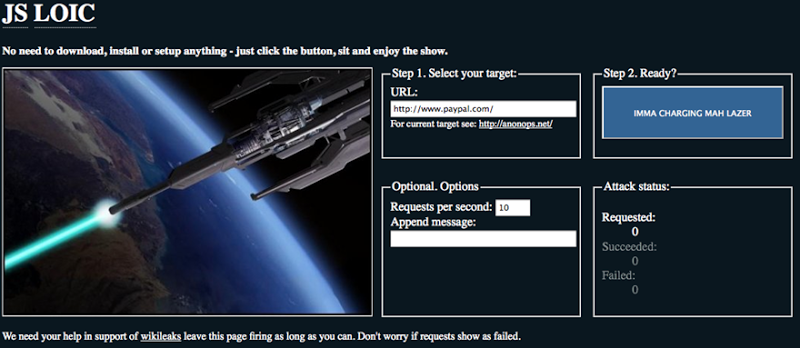
This is an entirely JavaScript based version of LOIC that runs directly in the browser. It can be hosted on any website and set to attack any target, all it needs is a browser. Unlike the desktop version it only supports HTTP (no UDP or TCP), but it will issue 10 requests per second (a configurable default) to a randomised image path which will cause a “404 not found” on the target machine. The randomisation ensures no caching of the response and the request is a simple HTTP GET which may also include a customised message in the query string (assumedly to leave a calling card in the web server logs). You can sit down at any PC (internet cafe, office environment, etc.) and launch a DDoS attack using JS LOIC right now.
Is DDoS’ing hacking?
A DDoS attack typically does not involve exploiting any vulnerabilities in the target website. There’s no probing into SQL injection risks or circumventing access controls, it’s an extremely low-tech brute force attack. My view – and some will disagree – is that a DDoS attack is not hacking. It’s malicious, the intent is to cause outage and damage to the service availability of the target but that’s it.
Frankly, I think it’s almost giving the attack vector too much credit to brand it as hacking. It’s hard to both have an understanding of security and call Christopher Weatherhead a “cyber-criminal” who launched a “sophisticated" attack. A 14 year old with no understanding of information security opening up JS LOIC in his browser cannot reasonably be called a “hacker”, at least not if we still want to use that term to brand competent career criminals who specialise in data theft and digital espionage.
Can I be locked up for using LOIC?
One of the “defences” by those who feel LOIC is something they can get away with goes like this:
The risks involved in using Hivemind LOIC seem pretty slim. A “virus” could have caused your computer to launch similar attacks – this sort of thing happens more often than you’d think. Your computer illiterate aunt’s Gateway PC that is still running Windows 98 may very well be involved in hundreds of these attacks. Also, once a succesful DDoS attack knocks a server offline, the log files that’d normally be used to determine where connections were coming from most likely won’t be accurate.
Same deal with this FAQ on Your Anon News:
Will I get caught/arrested for using it? Chances are next to zero. Just blame you have a virus, or simply deny any knowledge of it.
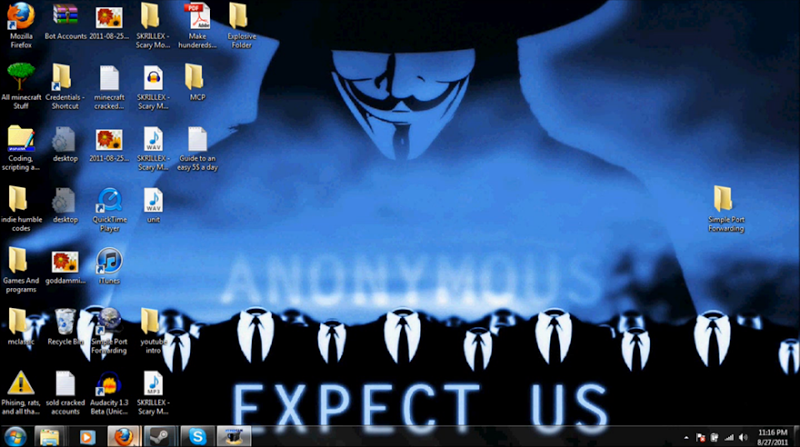
A virus doesn’t spend copious amounts of time on IRC, browsing 4chan, updating its Twitter timeline or communicating with mates on email about the next raid. Combined with data they may pull from the target site (and there’s a very good chance your IP will be in the logs in at least one network segment), the user’s ISP and possibly with the support of social media providers, a very clear picture will likely emerge. Using LOIC will fit neatly into this picture in a way it never fits into a computer illiterate aunt’s. If the authorities come by and ask for a look at your PC after observing DDoS activity from your IP address, it’s hard to deny being involved in hacktivist activities when your desktop looks like this:
Of course it may be a different story if LOIC users are extremely cautious about their operational security and take the right steps to carefully obfuscate their identity. That’s one of the things about LOIC; it makes no pretences whatsoever about protecting the identity of the source. There are many, many references to this on various forums and discussion boards – the info is easy to find. There’s also a very interesting paper titled Attacks by “Anonymous” WikiLeaks Proponents not Anonymous where they conclude:
It became clear, already with the first analysis, that the tool does not take any precautions to obfuscate the origin of the attack. This means
that the IP address of the attacker is included in the packets sent to the victim. The simplicity of the attack came to a surprise, since techniques are already known to obfuscate attack traffic.
The paper goes on to say that using LOIC is like “sending a menace letter with a return address”. So the only way to stay safe is by obfuscating your IP address through a service like Tor, right? The problem is that even if you do a great job of obfuscating your identity, it only takes one tiny little slipup and everything comes undone. Take this photo as an example:

This was posted by Higinio O. Ochoa after he was involved in hacking into law enforcement websites in the US. It only took one photo with the geolocation data still in it for authorities to track him down.
Or there’s the now infamous “Sabu” of LulzSec fame who we now know as Hector Monsegur:

He slipped up in a variety of ways including simply forgetting to anonymise his identity before connecting to IRC on a couple of different occasions and accidentally disclosing his ownership of a domain name that could be traced back to him during an IRC chat. Both Hector’s and Higinio’s activities were undoubtedly more malicious and more persistent than a simple DDoS attack, but it just goes to show how you can be brought undone by a simple mistake.
Getting back to DDoS arrests, there are many, many precedents of the law catching up with anons who turn out to be not so anonymous. In late 2010, a 16 year old Dutch teenager was arrested for using LOIC as part of Operation Payback against companies that had begun refusing to process payments to WikiLeaks. This lead to retaliation against the national prosecutor’s website which quickly results in the arrest of another Dutch teenager, this time a 19 year old. Apparently the guy just fired LOIC up from his own PC connected directly to the internet without taking any identity obfuscation measures. As the article in the link says “That's a pretty silly mistake to make if you're going to attack the website of your country's national prosecutor”. Indeed. Then there was Giordani Jordan in the US a couple of years back, Dmitry Olegovich Zubakha in Cyrpress and a two unnamed teenagers in Norway last year plus of course Christopher Weatherhead in the UK who we now know is in jail. It’s a rapidly growing list of global arrests.
What’s all this about DDoS being legalised?
A couple of weeks back an online petition was opened asking the US to legalise DDoS as a form of protest. The petition asserts the following about the nature of a DDoS:
It is the equivalent of repeatedly hitting the refresh button on a webpage. It is, in that way, no different than any "occupy" protest. Instead of a group of people standing outside a building to occupy the area, they are having their computer occupy a website to slow (or deny) service of that particular website for a short time.
There are many, many reasons why this won’t gain any traction. Firstly, there’s a fundamental difference to an occupy protest in that there is no physical presence, in fact participants often go to great lengths to ensure anonymity. In most places on earth, citizens have the right to peaceful protest and if they go a little too far and break the law than the authorities step in and take action. Many involved in DDoS attacks only seem to do so on the basis that they believe they won’t be identified.
The other big issue related to physical presence is jurisdiction. If I jump on a plane and head over to the US to mount an in-person protest then clearly I come under their jurisdiction and am subject to their laws. If I sit at my PC and fire up LOIC against a US server, things get a lot greyer. As we saw at the start of this post, a UK citizen was convicted for a DDoS attack on a US company so even if this petition did get picked up, they’d still need bilateral agreement for it to make one iota of difference to guys like Christopher Weatherhead.
But legalities aside, the act of “a group of people standing outside a building to occupy the area” is a fundamentally different concept to a coordinated, targeted attack mounted by anonymous individuals not with the intent of peaceful protest, but rather with the intent of causing serious business damage to the target. That intent alone kills any chance of legalising the activity.
To DDoS or not to DDoS…
For anyone thinking of getting involved in a DDoS attack, ask yourself this: would you be happy for your identity to be disclosed and your actions tied back to you? There are many protestors “in real life” who are happy with this – even if the legal consequences are severe – as they’re invested enough in the cause to devote themselves to it regardless of the consequences. Question is, how many people firing up LOIC actually feel the same way?