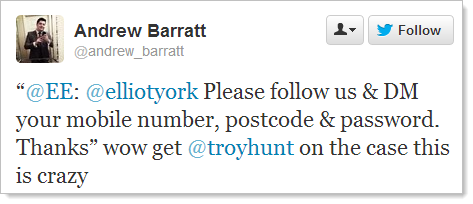
It happened again – someone tweeted me about a negative security experience and I just had to take a look:
C’mon, really? This can’t be for real. But a little more investigating and here we are:
This is bad (for reasons I’ll discuss shortly), but it’s far from isolated:
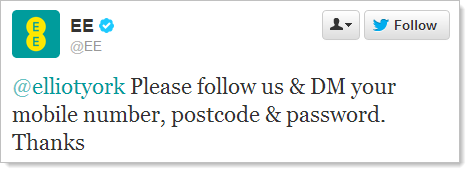
EE is over in the UK and they’re “the new network for your digital life” who brings you “4G and Fibre Broadband”. A quick look at All My Tweets and it seems that requesting passwords through Twitter is a standard operating procedure. So what’s wrong with all this? Let’s count the ways.
DMs likely result in transmission over insecure medium
If you’re like me (and from memory, this is the Twitter default), a DM leads directly to an email and as we all know, email is totally unsuitable for sharing anything sensitive. If you DM someone your password and this default behaviour is retained, that password is sent over an unencrypted medium where it can be eavesdropped on.
It also resides in a mailbox so what you’ve got now is a treasure-trove of credentials with no cryptographic storage whatsoever. This brings me neatly to the next point…
Twitter DMs should not be considered secure storage
Who on earth ever thought it was?! Sure, Twitter provides SSL to logon and then access your DMs but it’s not intended to be a secure storage repository any more than what email is. The other thing is that Twitter accounts get breached on a relatively regular basis (it’s usually the fault of sloppy password management), ask @DearShirley how that worked out for Westboro the other day (yes, we’re all happy about that result anyway but you get the idea).
Anyway, short of EE purging their DMs on a regular basis, what we’ve got here is gold mine of credentials with nothing more than a single Twitter password protecting it.
You can still login to Twitter over an insecure connection
You still need to be a little bit careful about your Twitters:
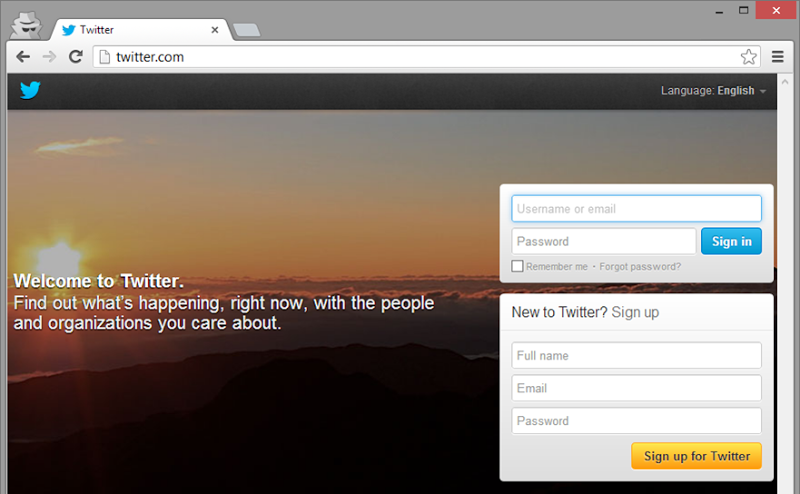
Yes, yes, I know it posts to HTTPS, but then you know that’s not enough, right? Unfortunately, even in the wake of serious incidents relating to logon forms being loaded over HTTP, not everything is up to scratch yet. It was just last year that the Tunisian government was found to be harvesting social media credentials by injecting script into logon forms loaded insecurely and whilst progress has been made, we’re clearly still not at the security position we really should be.
But we know this, right? I mean we know that Twitter or Facebook or any number of other social media tools are not designed to be the bastions of security. It’s not just logons, there have been all sorts of issues relating to security over the years. These are social media services first and foremost, not secure communications services.
EE is almost certainly not storing passwords in a cryptographically secure fashion
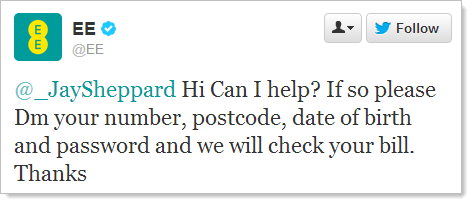
Take a look at this:
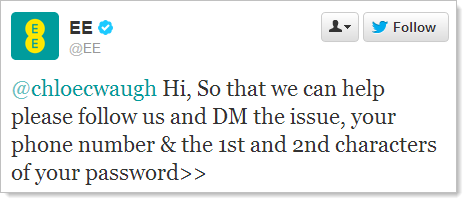
See the problem? Ok, here’s how proper cryptographic storage of passwords works: plain text is provided, it’s hashed (after being combined with a salt, of course) then the cipher is stored in the database. Hashing algorithms provide a deterministic result (the same input always produces the same output) so although you can’t un-hash, you can always feed in the same password and match the cipher. The same password – not the 1st and 2nd characters or any other subset of the full password.
What this says is that passwords are stored either in plain text or encrypted, neither of which is satisfactory, not by a long shot. There’s simply no way you can take a portion of the password and compare it to a properly secured password in storage. Per the comment below, this would be possible with Shamir’s Secret, whether that’s what EE is doing or not, well, there’s also Occam’s razor…
Something is amiss in the customer service process…
What EE’s request appears to boil down to is a verification process. Granted, it’s odd that the data requested seems to vary between requests (the first one didn’t ask for a date of birth), but passwords are a common identity verification process.
But not the password used for accessing web assets. When I hire a DVD (very rare in the streaming video era), but when I occasionally do, a person asks for a password. Through any other online medium with any consciousness whatsoever about security, this simply isn’t done and for many very good reasons.
To begin with, verification of identity is often done over the phone and your phone line is an insecure medium. No verification of authenticity, no encryption, it’s just wide open. It’s the PSTN equivalent of logging on over HTTP. Whilst EE’s request was via DM, I’ll wager that EE is asking customers on the phone for the same password they use to logon to their online assets.
Also, people are an insecure medium! Verbally providing the password that would allow an operator to go home and personally access your account whilst sitting at their PC is just not on. Common processes of identity verification (think of the last chat you had with your bank), don’t allow this sort of behaviour to happen. Most companies implement fairly regimented processes to ensure an employee no longer with the organisation loses access to any online assets quite promptly; how’s that work when they know their customer’s passwords?!
The other problem with a DM is this:

It’ll differ between Twitter clients, but it’s very, very easy to reply publicly rather than DM. I know I’ve done it before and I know I’m not alone – what if that’s your password? EE has hundreds of instances where they’ve asked for a password to be sent via Twitter, how many responses have broadcast it to the world? A safe bet would be “more than one”.
Here’s how it should be done
A very quick rundown of verification without firing the one password around the internets:
- Password verification is feasible, but not with the same one used for general web access. Often there is a PIN used for phone verification which is entirely unique to the one used for automated online verification.
- Alternatively, verify using information already known about the customer. For example, phone the person! I mean they’re in the telco business, they have the technology, right? Alternatively (and I do appreciate the overhead the phone poses), verify via the registered email address.
Again, think back to your last banking experience as usually they’re a good yardstick for security (but not always, *cough* CitiBank), what sort of information were you asked to verify your identity? Almost certainly, it was nothing that could then be taken and leveraged with the anonymity the online world provides to actually cause some form of adverse impact to the account.
Finally, passwords remain a very imperfect authentication method but they’re the best damn mousetrap we have right now. However, one of the things that makes passwords so vulnerable is that we keep reusing the damn things. Case in point: earlier in the year I found 59% of accounts common to both Gawker and Yahoo! Voices used the same password. And speaking of Gawker, how about all those Acai berry tweets that popped up right after their breach due to customers reusing passwords with Twitter? Nasty stuff, but something that we fallible humans do and it’s a good reminder why folks like EE are not just jeopardising the security of their own accounts, they’re jeopardising the security of every other account their customers have reused their passwords across.
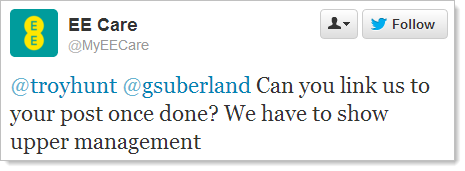
Oh – one last little thing as it just slipped onto my timeline; responses like this are great:
No really, this is a great way to elicit feedback and it can only be a positive thing for all if EE take it on board and objectively assess the risks and make a conscious security decision one way or the other. There’s nothing here that’s not readily publicly observable anyway but hopefully shared in this context EE might take a more secure approach in the future.
Update, 31 Dec 2012: There’s one other very, very important point I neglected to make and I’ve inadvertently demonstrated it perfectly in the image above. The @MyEECare account is fake and has been suspended in the 7 hours since I wrote the post. There’s now an @EESupport account doing the same thing; same avatar as @EE, same branding too. Obviously it’s not Twitter verified like the official account, but it’s convincing enough that were they to ask someone for their password via DM, I reckon there’s a damn good chance they’d get it. Your average consumer isn’t going to do their own due diligence on the account authenticity before sending personal data – particularly when it’s presented like these ones – and that’s a serious risk indeed.