There’s a pattern in the following stills from various scammer videos, see if you can spot it.
Here’s one run by Comantra I captured back in Feb:
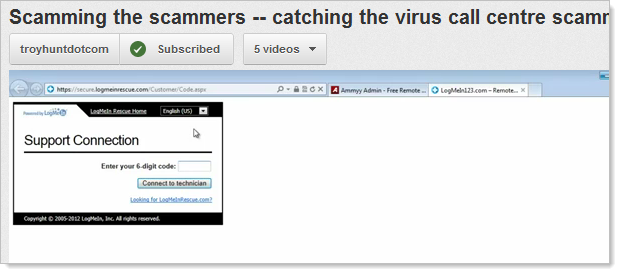
And here’s another one from when an unknown scammer called me in late April:
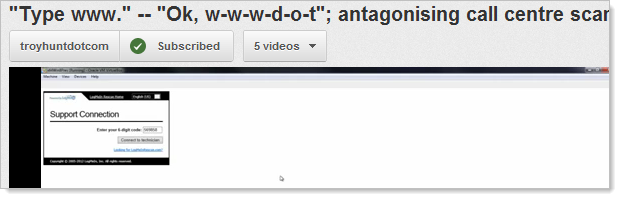
Now here’s one from Noah Magram who’s the principal software engineer for Sourcefire:
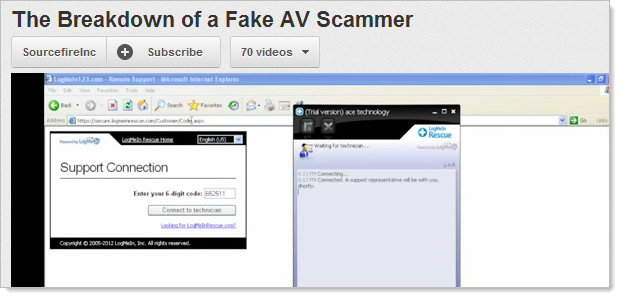
Noah’s video in particular gained some serious exposure when it hit YouTube a couple of weeks back. In fact he’s had about 157,000 views at the time of writing and each of those viewers has seen the same thing they’ll see in my videos and any number of other similar videos on the web – they’ll see LogMeIn:
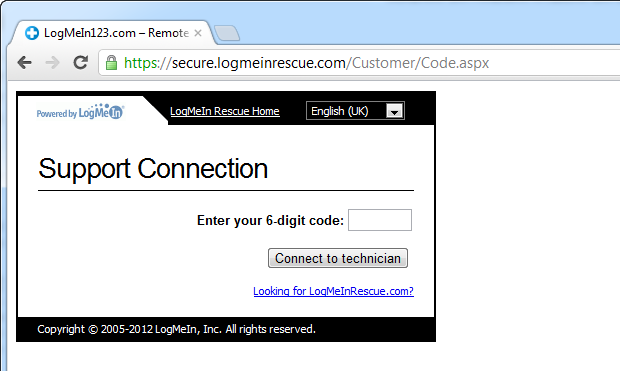
LogMeIn know about this scam and they know their software is being used to defraud unsuspecting victims, yet despite all this nothing has been done to mitigate the problem.
I first contacted LogMeIn back in Feb after I captured that first video. I got in touch with their Director of Corporate Communications and in essence the response boiled down to “after a scam happens and we find out about it, we terminate the account”. A defence was put forward that in order for LogMeIn to work, it “requires mutual consent”. Of course it’s clear from the videos that by the time consent is required, the FUD has well and truly been established and it’s highly unlikely the victim won’t consent to the use of LogMeIn.
LogMeIn also made the point that there’s an “omnipresent kill switch” which allows the end user to terminate the remote control at a later time (the software remains persistent after the session). The problem here is that as you can see in that first video, the victim has already been defrauded by the time the call is over so exercising the “kill switch” later on is an action taken well and truly after the proverbial horse has bolted.
So time passed and the following month I had another call which, as you can see from the second image above, also featured LogMeIn. So I emailed them again. Actually, I did more than that, I suggested they consider the mockup below:
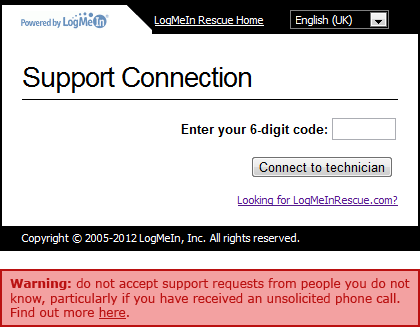
I pointed out that clearly, whatever they’re doing is not working as the scam persists. My experiences are obviously only a tiny slice of what’s actually going on out there – how many other people are being conned? Anyway, I was told the idea was “under consideration” and that was the end of it.
Fast forward a few weeks then Noah’s video came along. I followed up with LogMeIn again (this is the third time now), as I thought this was a good illustration of the problem, particularly given the audience the video has attracted. This was the week before last and as of now, there has still been no response.
So what do we make of all this? Well clearly whatever it is that LogMeIn are doing to curtail this scam is not working, that much is clear. But it’s also clear that there’s not much willingness to actually do anything about it. For the unsuspecting victim, there is no warning on the website to suggest that they’re about to embark on a process which could not only cost them a bunch of cash, but could irreparably damage their operating system (go back to Noah’s video). On the available evidence, LogMeIn is just not interested in fixing the problem; they’ve become complicit in the scam.
I’ve had dozens of emails from people who have innocently been defrauded by this scam. Plus there are hundreds of comments on my various videos and blog posts – this scam is rampant and it’s regularly catching unsuspecting victims.
I thought carefully before writing this post and I’m doing so only after exhausting other avenues. I am going to ask a favour of readers and that’s to click the image below if what you read here concerns you:
Call to action: click here and retweet:
Help let LogMeIn know that this scam is just not on and they need to start doing something about it that actually works! C’mon LogMeIn, be a good netizen and do your bit to make the web a safer place.