So I’ve just wrapped up another Web Directions presentation where the Pineapple has featured. The what now?! You know, the WiFi Pineapple, that little guy with the ability to do all sorts of nasty things to wireless traffic. Now I’ve Pineappled before, but I’ve never Pineappled quite like this and that’s all down to the Mark V which performed significantly better than the old IV when it comes to the act of Pineappling people.
You can read the background on the device in the links above if it’s unfamiliar to you, let me give you an example of what I see in the Pineapple UI. Keeping in mind that the most recent record is first, here’s a device probing for known SSIDs:
KARMA: Successful association of 84:38:35:56:6b:80 KARMA: Checking SSID for start of association, pass through slqwireless KARMA: Probe Request from 84:38:35:56:6b:80 for SSID 'BigPond0AC3' KARMA: Probe Request from 84:38:35:56:6b:80 for SSID 'DCA-STUDENT' KARMA: Probe Request from 84:38:35:56:6b:80 for SSID 'DCA-STAFF' KARMA: Probe Request from 84:38:35:56:6b:80 for SSID 'QUT' KARMA: Probe Request from 84:38:35:56:6b:80 for SSID 'ABC_WIFI' KARMA: Probe Request from 84:38:35:56:6b:80 for SSID 'Goat' KARMA: Probe Request from 84:38:35:56:6b:80 for SSID 'School House' KARMA: Probe Request from 84:38:35:56:6b:80 for SSID 'maryellen' KARMA: Probe Request from 84:38:35:56:6b:80 for SSID 'slqwireless'
The last line and the second line tell the story. The device has previously associated with an SSID of “slqwireless”. This network did not have any encryption so when the Pineapple observed the probe request and then changed its own SSID to “slqwireless”, the device happily connected to it. It has now been Pineappled. Further up in the Pineapple interface I also see this:
44473 84:38:35:56:6b:80 172.16.42.246 Artemis 01:84:38:35:56:6b:80
This tells us the device on that MAC address is named “Artemis” and has been assigned an IP address of “172.16.42.246”. This is useful as it means we can start to take a stab at who owns the device and when requests are then made via that IP address, we’ll know who’s making them. Often the device is named something like “SerenasiPhone4S” which starts to narrow things down a bit. Is there someone in the immediate vicinity named “Serena” and using an iPhone 4S? There’s your target.
So that’s how we can identify the devices and potentially the individuals connecting, now lets’ look at what we can do after that.
DNS spoof
This is my usual approach as it’s not something that’s really going to invade anyone’s privacy (later approaches we’ll discuss are a different story). What DNS spoof does is simply routes requests for a host name to another target. For example, you could reroute all requests for google.com to troyhunt.com. That would work for all HTTP requests to Google but not for HTTPS requests as you now have an encrypted transport layer (I’ll come back to that too).
Now this approach only works when the Pineapple actually has an internet connection, for example by being tethered to my PC via ethernet whilst the PC wifis into an access point. Doing this would mean we could do things like, say, load the normal page then replace every JPG image with my photo instead (crikey, imagine that?!)
Instead, I use the built in web server on the Pineapple to serve up a little web page of my own. I call it Pineapple Surprise and as you can see from that link, it simply loads a page like this:
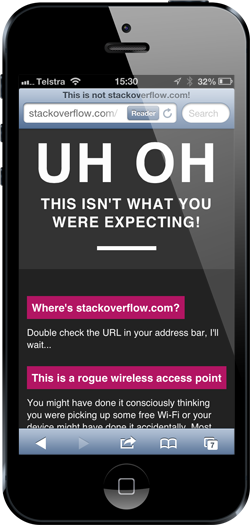
My objective is purely to raise awareness about the risks of unknown wireless connections and apps that don’t sufficiently implement SSL and that’s the best way I can think of to do that without invading anyone’s privacy and I’ll talk more about that in a moment. But if you did want to do that, well…
TCP dump
Going back to the point about routing traffic through an intermediary, a dead easy approach with the Pineapple is just to capture every packet that connected devices send through it. Every packet! This means that for every request that’s not made securely over HTTPS, the Pineapple has your data and it can be read by an attacker. Credentials, authentication tokens, personal data on web pages – if it’s not properly protected then it’s captured, stored and can later be analysed using a tool like Wireshark.
That’s seriously nasty business and every single one of those devices that connected to my Pineapple at Web Directions could very easily have succumbed to an attack like that. But again, it only matters when the traffic isn’t sufficiently protected by the app! That’s the real story here.
Manipulation of insecure responses
A little while back I wrote about how Your login form posts to HTTPS but you blew it when you loaded it over HTTP. This is exactly the sort of risk the Pineapple can exploit; who cares if the site posts over SSL when the page your entering your creds into has a keylogger that’s already captured them and sent them to the attacker before you even hit the submit button?! I’m sure you can see the problem.
SSL strip
Ok, so secure requests are ok, right? Kinda. Let’s imagine you go to your credit card account by typing “americanexpress.com” into the address bar then hit the enter key – what happens? The browser makes an HTTP request to the domain where it then responds with an HTTP 302 “Redirect” asking the browser to load the HTTPS version instead. That works just fine – usually.
SSL strip has the ability to take that original request, receive the response from the server then make the HTTPS request itself. It then sits in the middle talking HTTPS to the server but HTTP to the client. So long as the client isn’t explicitly making HTTPS requests, you’re cactus.
Web Directions results
Nothing answers the “Isn’t a man in the middle attack really just a bit hypothetical?” question like pointing out how many people are willingly sending their data over a rogue access point! Actually, “willingly” is probably a bit unfair as the device will connect of its own accord without the owner consciously connecting to the Pineapple. So I turned it on and had a wander around the Web Directions conference. Many people were Pineappled:

Once Pineappled, it meant a lot of this sort of thing was happening:
In this context and IMHO, this is a very good thing. It’s a good thing in that it’s very impactful and in this context, the Pineapple wasn’t doing anything unethical. During my talk where I demonstrated how easy it was to inject a keylogger into a form loaded over HTTP, it made a world of difference being able to then refer to all the connections the Pineapple made.
All told and in the space of about 30 minutes, attendees broadcast probe requests for 997 SSID:
#HKAirport Free WiFi, #WiFi@Changi, @Free WiFi, _FREE WiFi by inlink., _FREE Wi-Fi by inlink., _FreeSkyFii_, _Heathrow Wi-Fi, _The Cloud, 101, 106F3F760DA7, 1110, 123456, 1435, 144Flinders, 1888hotel, 25T2, 28Qlix04Wlan48, 2bORnot, 2WIRE138, 3000, 3002, 35Guest, 3MobileWiFi-1514, 3YZ9Bq7ymQ_2, 4786016, 5099251212, 5B2-3-2 My Vien, 7390, 7390 5GHz, 78600093, 7EB3CC, 89ClientWifi, 98-2-3, 999, AAA, Aarons Hotel, ABC_WIFI, abc123net, abgtest, ACHERNAR-BG, acubluecoat, ADAC Free Wireless, Adapptor2, Adapptor3, adhoc2, ADMIN-HP_Network, AdshelWifi, ADSL4546, AE6QM, AEGISWAP, Aeroexpress free WiFi , AFV-WiFi, ahck, ahp, AirFranceLounge, Airport, Airport_Hotspot, AIRPORT-FREE-WiFi, ajf, AKP, albastru, Alexanders, AliceSprings, ALICE-WLAN24, A-MAR401, amptech, ana, ANDKAT, AndroidAP, AndroidHotspot1907, AndroidTS, ANMMCorp, annetwerk, anthonywireless, Apex_Free_Internet, Apple Demo, Apple Store, Aran Irish Pub, Arcanine, ARC-Guest-WiFi, ARTCInternet, ARTIS-002, ARTIS-402, ARTIS-405, Atlantis, Atlas-City-E2-1, Atlassian, Atlassian-Guest, AUBERGE2, AUNSW-AEGIS-WIRELESS00, Aussieville, Aussieville 5GHz, Austin's Pizza, auteuil, AUVIC-AEGIS-WIRELESS00, Avi-MBA, AWG-WiFi, Azure, Azure@MantraOnKent, BagelsBeans, bajafresh, BalmainBackpackers, bananafritter, banksia, Barcelona Guest, Bauhaus, Bayview Boulevard Sydney, Bbox-8F1A55, BCECLINK, bcolbert, BeanBag, behone, belkin.155, Belkin.5BA6, Belkin.7A18, Belkin_G_Plus_MIMO_ADSL, Belkin_N_ADSL_7B7F75, belkin54g, BELL_WIFI, Bellagio-Rooms-Cox, belmont, BestWestern, BFA, bigplanet, BigPond0AC3, BigPond14F9C1, BigPond15AC61, BigPond1A85, BigPond1FD3BC, BigPond498146, BigPond4D0601, BigPond564C, BigPond8ACB24, BigPond9B9665, BigPondA053E5, BigPondA24DD7, BigPondB141FF, BigPondD89D5B, Bite_TV_Free_WiFi, biteme, bittoncafe, Blackwattle Deli, bluAir_3000743, BlueArc Group, BlueBuildingLinker, bob, bogus, Boingo Hotspot, bojenci, bojing331, Bonkuras, BONNIE, bowen-dlink, BRHotel Guests, BRHotelBondi, BrisyDoyles, Brunello, BTHomeHub2-6CR8, BTHub3-FJG2, BTHub3-GZJP, BTHub3-J8W8, BTHub3-M7SF, BTOpenzone, BTOpenzone-Starbucks, bts-2, bts-3, BTSYDFE, Bubba, BUFFALO-B43120_G, Bullys Public WiFi, Bunker Bean, Bunya-Park, buzzLounge, BYOD, CABANA Vip L, CABANA Vip P, cabana2, CableWiFi, CACTUS, Cafe de Paris Budapest, Cafe Del Sol, CAFEhotspot, CafeScreen_Free_WiFi, CafeScreen_FreeWifi_CS, Cambridge Forum Free Wifi, Cambridge Forum FreeCR, Campbells, Cargo Free Wireless, Carriage House, castillo, castillo2, Cattery, CentaraWiFi@F1, CentaraWiFi@F2, CentaraWiFi@F3, centerinn, Central Market Guest, Centre Wireless, CESMa, CFC-002, chaos, charcoal, Chemist Warehouse 04, ChinaNet-EpjH, ChinaUnicom-SPIA, ChloJo, CHNSW-WIFI-30, chromium, ChuckInternet, chunky, CIAL_Free_WiFi, Cisco08788, citizenM, CityRail_WiFi_Trial, Club Lime FREE Wireless, CLUBHOUSE_FREE_WiFi, cluMac, CMCC-TEST, CMH, COMOWIRELESS, Compound677, CONDADO, Confab, Conference@PanPacific, Connect Free WiFi, Connectify-ala, Coolangatta Virgin Lounge, CoopCas, CorePower Hotspot, CornXchange, cottamgoble, Courtyard_GUEST, CP Public Wireless, CPA_Staff, CPH Hotspot, CPH Voucher, craigieopen, Craig's Network, cretan, CrinitisFreeWifi, CRITERION, Crowne Plaza Conference Wireless, Crowne Plaza Lobby Wireless, Crowne Plaza Public Wireless, Cruise Bar, CSC2, csiro-internal, CSUconnect, cupcakes, Curio, CW-LT46 Wireless, DABMDB0606648MD, DABMDB0606648VC, Dad's iphone, Damocles, Darling Harbour Hotel2, DarlingQuarterFreeWifi, DarwinAirport, datavalet, David Liu, davieconsulting, DAVITIAN, daxattacks, DCA-STAFF, DCA-STUDENT, DDIGITAL02, def, derp, DerpNET, detguest, Dexters Lab, dexters table, Dexters-Lab, diana, DigiBiz, Digital_Guest, dlink, DLink-FC058F, DL-Talkback, dmagic2, doomed, Doyle, DoyleAndroid, DoyleFamily, drupal, DSL-2642B, DSL-2730B, dudan1105, dugommier, DUNAHOLEL, DUNAHOTEL8, Dusty Couch, DV's Wi-Fi Network, DwsLink, ECF201MAC-001a, EdgeTest, eduroam, eh-home, eircom5350 7244, elsoldelsols, elucid2, Endor, EngineRoom, EngineRoom2ghz, esa-public, ethostream, ethostream pub, Ethostream_Lobby, ethostreamRSC, ETIHAD WI-FLY, etphonehome, ETUD_POLYTECH, event@upf, Excelsior, exhibitors, Falkor, Fanta Wi-Fi, Farinangio, FASTWEB-1-n9df5Q5Lpdtj, Fernroyd_EXT2, ffd2ri, FFXCorp, FFXGuest, FICUSNET, FightClub, fitzrovia, Fletcher, Flexa, FlexaMobile, FlexaMobileLTE, flyingpings, FPM, FP-WLAN, FraserConnect, Free Beach WiFi, Free WiFi, Free Wifi Bagels&Beans, FREE WIFI by SYD, FREE WIFI by SYD db, FREE_INTERNET, free-hotspot.com, FreePiemonteWiFi, FreeWifi, FSASYD, FTE-790F, fuji, GA-GUEST, Galaxy Cafe.. Yum Yum!, gammy, GARbageNet, Gates 10-14, gaurij, gazillo, gazillo otg, gctechspace, GD, Geisel-Privathotels, ginterlude, GirlsOnly, giunone, gizemKablosuz, GMZ, Goat, Gogata, gogoinflight, GoldClassButler, GoldenPark, goldensand56, goldensandB3, GoldensandC3, goldensandc34, goldfishandkoala, Goldsbrough Public Wireless, Good Guys Free-WiFi, GoogleGuest, Greg Masselos's iPhone 5, Grumpy-noWEP, GTAdventures, GuciAU, Guest, GUEST_INTERNET, guestnet, guOttawa, GW_1, GW_Wireless, HAdata, HAGL 16-01, HAGL 17-01, halfmoon, hanywifi, Haq, Haymarket Library, heads, Helen...s iPhone 4, HG655D-EA28CE, HH0581 - iPhone 4s - iOS6.0.1, Hide yo kids, hide yo wifi, High24, High5, Hiscock_Extreme, Hiscock_Extreme_N, History_in_Ernest, HMM-GUEST-WLAN, HoiAnNet_MegaWifi, Holiday Inn Lobby Wireless, Holland Casino WIFI Hotspot, home, homenet, homerun1x, hommelnet, Horizons Guest Lounge, Hostel, HotCafe_Le_Central_WiFi, Hotel, HOTEL CECIL, hotel des grands hommes, Hotel dos Cavaleiros Level-1, Hotel_Ibis, HotelBlue, Hotel-ILF, HotHouseWiFi-L1, HotHouseWiFi-Up, HotSpot, HotSpot Aeroport de Bordeaux 1, HP-Print-10-LaserJet 100, HTC Portable Hotspot, Hubertushof, HUBTELECOM, Hyatt, IAC - Hanmer Top 10 Hotspot, iamnotpregnant, iBahn Mobile Streaming, Ibis Public Wireless, Ibis Wireless, IBM, IGNconference, ii1729E2primary, iiguest, iiNet Guest Internet, IKEA_FREE_WIFI, ILikeYourCat, Illuminera Strategy, IMAP, indieWIFI, Infinity, Infomedia, Innovation, INSTICC, INTAC, Intercon_Guest, Interislander, internet, Internode, Intertain_media, interwebs, iPad, iPhone, ipixel wifi, IQNet, IRI, ironwharf, ISI-GUEST, ISI-SECURE, island-2DE6D0, ISWC, ISWC_5GHZ, ISWC_L1, ISWC_l3-L4, jack, jadeguest, Jadons-iPad, James's iPhone, jdwireless, Jim Moginie's Guest Network, John.........s iPhone, Joy...s iPhone, JS Conf, JudcomWifi, JudcomWifiOne, Jumbo, juseral, jv, Ka26, kamenoi, KANA, Keith's Wi-Fi Network, KellyNet (Main), Ken_Low, KEVINSONYA, KHDVC, KIA Wi-Fi, kiado kocsma, killilan, kingfist, kiwifoo, Koruclub2, kost, krishnajaal, KTS Airport Network L10-01, ktstudio, KT-Wireless, kubi_Hall, Kursalon, KW, kyriad mirande D, La Maza, Lager, LAGUNA GARDEN, LAIR, Lawson Network, LAX-WiFi, LDC, LDGuest, LEOA5F-1, leonard-laptop, LeopardShark, Les, LEXI, LGAQ Advocate, lightwire, Lilianfels Resort & Spa, LINC_Tasmania, Linksys, linksys-g, liron htc, Littleguy, Livebox-a5b1, Livebox-B148, Ljubljana Resort1, Loaded, Loaded Comms, Lobby@PanPacific, LockLoadWiFi, lonet, Lord Nelson Brewery, Lords Gym Cafe, lsr, lululanantaise, macbook, MacBook Pro di Simona , Macquarie OneNet, madteam, Mahony, maimon, Mall Offers WiFi, MARIADORRESIDENCE, Marina Hotel, maryellen, Massive, mathelode, MAURINET, max, MaxKirwanCafe, maxspot, Mayflower, MB-CIAB2, MBS Visitor, MC-CIAB, McDonald's FREE WiFi, MCGhotspot, mdb, media_air, media_fast, media_slow, medialink, mediam, MeinFernbus, Melbourne Virgin Lounge, Meriton_116, Meriton_530, Meriton_Campbell_4, METEOR, mgmg6709, MIA-WiFi, Michael...s iPhone, Mimi, MM, Mobile Device, Mobile-Dev, Modern_Hotel, Mogo, mojito, MonkeyNet, Moon Unit, MPLUX AirPort, mr whippy, murphy, museumpublic, My 3 Suns, mycoitpiece, MyPort Hotspot Sails 3, NACHO_INTERNET, ndtns01, neecebun, Needlebox Network, nemanja, net1, NetComm Wireless, NETGEAR, NETGEAR22, NETGEAR30, Nethome, NETHUI, NetHui2013, NETHUI-WF3, NetworkAccessNetGear, NEWSLTD-INTERNAL, NiceAirport, nicta_wireless, NIDS-Gov, nietos, ninml1005071, Nintendo_3DS_continuous_scan_000, Nivarda, NOODY_POMPEIRESORT_R2, nostringsattached4, NotFree, notube, Novotel Lobby Wireless, Novotel Public Wireless, NPS Wireless, NSWiFi, NUCLEOLUS, NUCLEOLUS 5GHz, NUS, NWCUSBAP....L.e.i.r.i.t.h......., OBS, OnAir, one-north Wireless, ono7025, onQ, Opals-Public, OpenFCT, OpenHub, Optus Wireless Broadband, OPTUSDN5184D6, OPTUSV37094E, orange, Orcon-Wireless, OTEL-URHAY, OWL, p&c@home, pacificint, PageUp People N, Panda-Gurmet, Pandora WiFi, paradise, Paris 1, Paris Baguette, PARKROYAL, PCC, peelst3unit, PEJGuest, Peppers Guest, PetraHouse, PHILS, PHM Visitor, Plate Restaurant , Pluto, PMG-SYD-01, PocketDoyle, pocketwifi-599d, pocketwifi-9b5f, Policy Aust, polimi-protected, POLYTECH-CONGRES, Positively Wellington Venues, Potsy2, Power, PR@SIT_HOTSPOT2, PT-WIFI, PUBLIC, Punsch am Mehlplatz, Punta Cana WiFi, Qantas-Lounge, Qantas-WiFi, qbnew1, qqmoar, QT-Guest, Queensland_Rail_Free_WiFi, QUT, R7V4Q, radiohead2, radiohead3, Radisson on Flagstaff Gardens, Railscamp, Railscamp (2.4GHz), RajSandy, RAMMMOODIEWLAN, RCL282W, Red Mill House, reepy-t, Renaissance-GuestRoom, renoir, RESTAURANT, Restavracija, restricted.utexas.edu, Rey, Riley, Robert's MacBook Pro, robots, Rodimarota, roma room hotel, ROMANWALL-4L, RoRox, Rowlandson, Royal - 575, royal-wifi, RT3052_AP, RTA1025W-BD1868, RV_WLAN, SAGEM_A83A, saintclaude, Sally's iPhone, SAMC, samit4me, sapienza, scarlett, scassy, scharffe, Schiphol_Airport_WiFi, School House, ScientificNetworkSouthTyrol, scs, sdl-53463, SEA-WL, Sebel Residence East Perth, seehotel, SFO-WiFi, SFR WiFi Public, SG5, SH, Shangri-La, ShazamN, Shinas, SHOP-FREE-WIFI, Shrimp Groove, Silicon Lakes, silvermaple, sim_zone1, sjcfreewifi, sjohnson53...s iPhone, skanzenclub, skiff engineroom, SKY37200, SKY7D7D5, Skynet, skynetglobal, skyview, SLC, Slingshot Rugby Supporters, slqwireless, Small Multiples, Small Multiples Guest, Smurfville, Snoogans, Snoogans_2GEXT, snosnhoj, Sofitel Conference Wireless, Sofitel Public Wireless, sokol_zg, Sonic.net-155, SOS Brigade, spin, spinner, SPROCKIT, sputnik, Squaw Valley Institute, SquawCreekPublic, squiz.fb, SRIGuest-Secure, ssau, ssyd05, Starbucks Wireless, Starbucks_WiFi, STARS Hotspot, stead, Steitz, Sterling Cooper Draper Pryce, Steve, Steve and Rom, steveandglo, steveandglo24, stockdalewan, StPancrasWi-Fi, Studios Tatsis, subnet zero, SUNRISE, Sunshine, Super8, surfdognet, suspiria, sweatandtears, Sweex LW050v2, Sweex_LW310V2, swisscom, swisscom-lobby, sx, sydneyairport.com, SynerScope Wireless, SZIMPLAKERT, TALKTALK-7AAAAA, talPor, TBBWireless, TBL, TCC, TC-CBD, TCwireless, Team America FY, teamrock, TECHED2013-SC, TEDxEQChCh, TEHS_1A7B1E, Telecom Free Wifi, Telekom, Telekom_ICE, Telerik4G, TelerikAPAC, Telfor, Telstra CBD, Telstra6D2F29, Tenda, TerraGoGuest, TESPEAK, Test, TfNSW_FreeWiFi, THALYSNET, The Clarendon, The Coffee Bean - Metro, The Conversation, The Star Guest WiFi, the view you want, The_Abyss, the_office_space, thecakewasalie, thechanlan, TheCoffeBean-PCT-IB, thecolourgroup, TheInternet, theloft, TheLybrary, themadness2, Tho, Thomson28FBE0, Thomson3F56F8, Thomson611B0C, ThomsonBF19D5, Tim Hortons WiFi, TISCALI, TITAN, TitaniaGuest_8-17, TitanWifi, TLBSS, tmobile, Tom, Tomizone @ Starbucks, TOMIZONE @ Sydney Ferries, Tomizone_iiNet_McNess, tompsych, Toronto Pearson Wi-Fi, TOUR EIFFEL, TP-LINK, TP-LINK_22273066, TP-LINK_AEEF41, TP-LINK_SV, TP-LINK~, TPP4G_6B135F, TPP4G_6EB27B, TPP4G_AAA81A, TPP4G_AB5D0A, Travelodge, travesties, treehouse, treehousekidandcraft-guest, trust me, Tsinghua, TSNAirport01, TTHS_7D6309, TTNET WiFi, TTWF_loft, TWPublic, ubnt, UDJAMAFLIP, UGuest, Uni-Bremen, UnivOsunaWireless, uniwide, UniWireless, UoA-WiFi, UoM_WIFI, UOW, UOW_WIRELESS, Upstar, UQ_Wi-Fi, USB-WLAN, USC Wireless Plus, utopia-1F, UTS-WIRELESS, Uts-wireless 2, UTS-WPA, VandA, Veterans MC, vic, VicUni, Villa of Green Palms, VillageGreen, VIP, VIPBellagio, Virgin Media WiFi, VirginAustralia, virgintrainswifi, Virtuoso 2, Virus, Vita brevis, ViViFi 0282, ViViFi 1344, Voice, Voski, VOTANA, vtk32, vtkl8, waikato, walkabout, WAMPETERS, WAPV, wasap, Waterway, WB150-d0:5a:8e, wdc-b, wds-open, WEBBNET, WEBBNET-1, webdirections-open, Websilk2, wegmans, weiyunmak, WellcomeNet, WEST0697, Westin Denarau, Westin-public, WestinWAP36, wf-dbgdev, whaleshark, Wifi - Gangemi, Wi-Fi 4G-1B37, wifi router, Wi-Fi Sea Palace, Wi-Fi Sheremetyevo Free, WiFi Zone - The Cloud, WiFi_7F, WIFI-AIRPORT, WIFI-EMPL, WiFiLoveMCR, Wifizone, wifsyd01, Wignall, williams, wireless, WIRELESS-Guest, wirls, With Associates, with-drive, WJHOTEL-B12, WLAN_DV, wlan1, wlan-ap, wlan-ap67, WLAN-DF0A21, wlan-guest-wpa2-wwb, WLAN-PUB, WLANuni-fr, WLG Airport Free WiFi, wll03, wong, Woodlands37, wookie, wopen-net, WORLDPEACE, WPATubez, wwartPG, Wyong Golf - Public WiFi, X, xianglu, XLI, XoooooX, XSC-WiFi, xuxu, yes optus, Zarraffa's Coffee Toowong, ZduinWIFI, Zenbu.net.nz - Panorama Motel, Zero, zichy, zone50, Zoo_Wifi, ZyXEL, ZyXEL_B21C
There were then 74 identifiable devices that connected (many others connected without disclosing the device name):
airbiscuit, Alisons-iPad, Andrews-iPad, andro, Android_356402040882548, android-11ca7bacbd6e0664, ArcherPhone, Artemis, Atlas, Ben-Mays-iPhone, Bens-iPad, Biagios-iPhone, Bintang, Birchall-iPad, BreisisiPhone5, Cheryls-iPad, Chris-iPhone-2, Chuongs-iPad4, Chuongs-iPhone5, Cobie-iPhone-4, cPhone-5S-2, Darth-iPad, dominlis-iPhone, Dpod, Ed-iPhone, Evans-iPad, fatens-iphone, galah, Heaths-iPhone-2, HelensiPadMini, iPad, iPhone, iPhone-4, iPhonedenPerico, iPhonediagghiai, iPhonicusfourus, James-iPad, Jamess-iPhone, JamessiPhone4S, jareds-iPhone, Jeremys-iPad, JohnAllsiPhone2, jPhone, Kates-iPad, Kirin, LinJL, Macquaries-iPad, miPhone, moby, MorgansiPhone2, Nicoles-iPhone, PeterGoallsiPad, pg-iphone, prettything, R5001519, R5001721, SamuelCnsiPhone, schois-iPhone, SerenasiPhone4S, Shazing, Stephens-iPhone, Steve, SteveHusiPhone2, Steves-iPad-2, Teds-iPad, TessieThsiPhone, Tfone, Tommys-iPhone, Tomsipad, vincescsiPhone2, VINCEs-iPhone, ViviansiPhone2, wls-iPad, XiaoyanisiPhone
Every one of those devices could have had their traffic proxied through the Pineapple, HTTP requests stored and inspected, forms injected with keyloggers and even secure websites compromised using SSL strip on the initial HTTP request. That oughta put some real world context around SSL!