I’ve been considering purchasing one of these t-shirts:
This shirt would announce to everyone who crosses my path that I am, in fact, the world’s greatest lover. They would know this because I have a t-shirt that tells them so and it would give them enormous confidence in my sexual prowess.
If ever I was challenged on the claim, I could quite rightly say that nobody has ever demonstrated that this is not the case and there are no proven incidents that disprove it.
Sound ridiculous? Of course it is but somehow we’ve come to accept this practice – or at least tolerate it – by virtue of images like these:

The futility of this logo struck me last month when I wrote about 5 ways to implement HTTPS in an insufficient manner (and leak sensitive data). Here was a site that despite the assertions of the owner that it was “secure”, sent sensitive data in the clear, had mixed mode HTTP and HTTPS content, sent auth cookies over an insecure connection, didn’t flag sensitive cookies as secure to begin with and relied on HTTP to load the login form. Oh – and had a “Norton Secured” logo.
The futility of the logo really struck me when I read this forum response from Top CashBack after they were asked “how safe are your bank details in TCB”:
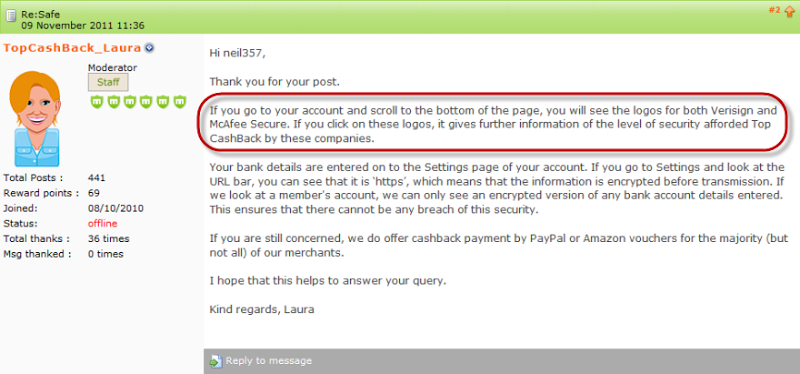
The site is secure because it has logos. Not just one logo, but two logos. This is beginning to be reminiscent of the entirely nonsensical padlock icon bitmap.
So what exactly does this logo get you? According to Norton (or rather Symantec who owns the brand), you get consumer trust:
- 77% of consumers recognize the Norton Secured Seal.
- 65% of consumers agree that a website displaying the Norton Secured Seal is safe to browse and won’t give them a virus.
- 55% of consumers agree that a website displaying the Norton Secured Seal means that the website protects their online privacy.
It’s the last two points that I found particularly interesting so I thought I’d take a browse around at sites displaying the logo. Almost every random example I picked where this logo had been used had basic security flaws. Not obscure hypothetical flaws but rather easily observable, readily exploitable flaws.
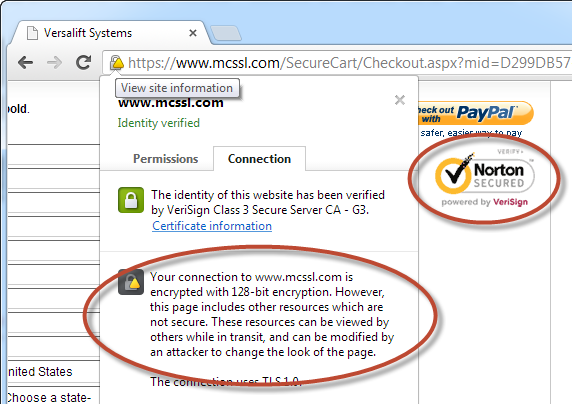
Versa Lift has mixed mode HTTP and HTTPS when you go to checkout:
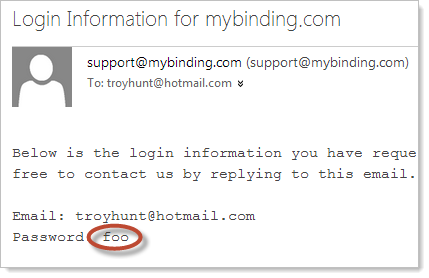
MyBinding.com also messes this up:

And then they let you choose a 3 character password. And email it to you:
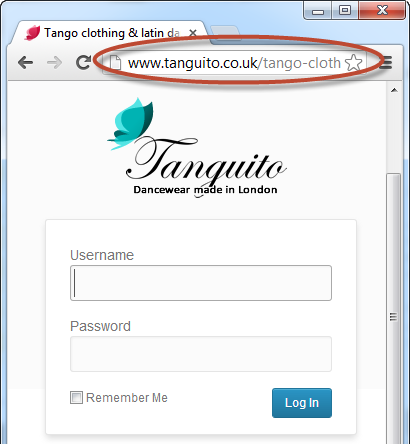
Then there’s Tanguito dancewear which has many impressive logos:

And no transport layer protection whatsoever on the login (and no, it doesn’t even post over HTTPS which would still be insufficient anyway):
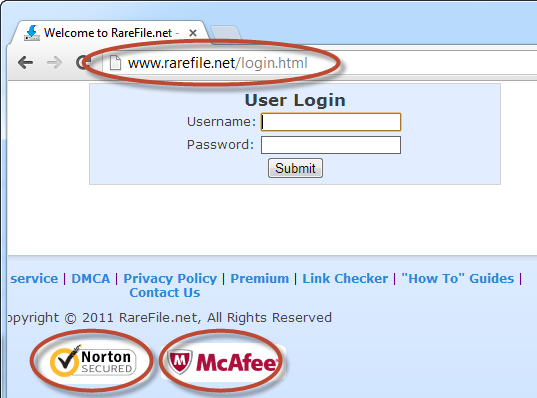
There’s also no HTTPS on the RareFile login (and we have multi-logos again):
None on Chemical Containers inc. either:

Or there’s iMeds with the simplest of reflected XSS:

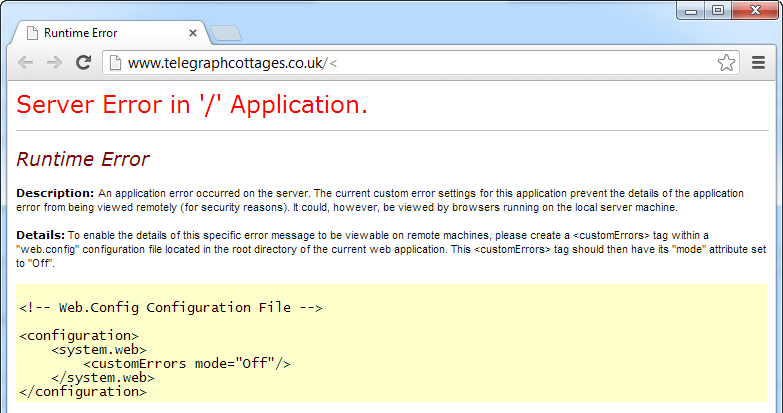
Continuing with the non-SSL theme, there’s Telegraph Cottages:

But get one illegal character into the URL and we have a case of Yellow Screen of Death via security misconfiguration courtesy of a misconfigured web.config:
And so on and so forth. The list goes on and on and on and, well, there’s a lot.
Of course there’s (unfortunately) nothing unusual about websites getting basic security practices like these wrong but when they do so and claim to have reached some higher moral security ground by virtue of a Norton or McAfee or any other seal then that’s just downright misleading. Claiming that the website is “safe to browse” or that it “protects [consumers’] online privacy” simply by the presence of a bitmap image is way off the mark. Who knows, maybe these cases have simply abused the acceptable use of the imagery but one thing is for sure; they’ve got their basics wrong on the security front and no number of security logos will change that.
If you believe the marketing hype (and I would definitely take this with a grain of salt), one of these little logos could lead to a 11% improvement in sales and 52% lift in sales from paid search. Suddenly the value proposition to websites becomes a lot more tangible and again, it all comes back to establishing trust. Unfortunately it’s just not warranted in so many of the cases where the logo appears.
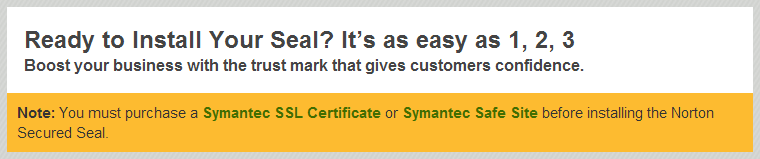
But of course it begs the question: what exactly do you need to do in order to display this seal which will boost your appeal with consumers? Have your site audited by security professionals? Scanned by a comprehensive dynamic analysis tool? Self-assess against a set of stringent criteria? Nope, you buy one of their SSL certs or have them check there’s no malware on the site:
Now interestingly, in theory, this also means embedding the seal with a piece of script which appears to go some way to verifying the fact that the page displaying the seal is indeed protected with one of their certs. Clearly this isn’t the case in some of the examples above but how is a consumer to know that? And whilst there’s absolutely nothing wrong with a Symantec SSL cert (at least not to my knowledge), when used as intended the presence of the seal merely verifies that the page in which it is embedded is loaded over HTTPS. The whole idea of OWASP calling part 9 of the Top 10 “Insufficient” Transport Layer Protection is that there is far more to SSL than just having a cert; it has to be used correctly!
At the end of the day, the only real difference between the t-shirt at the start of this post and the website badges above is that it’s simple to disprove the claim of the latter.