Who wants free stuff? C’mon, everybody wants a free lunch, right? Yes, yes they do and that’s precisely the trigger used in scams like this one.
Recently I wrote about the mechanics of another Facebook scam where the “bait” was photos of a salacious school girl. Many people – including female friends and my mother in law – readily fell for that one. This one takes quite a different and rather cunning approach which chains together numerous illusions and other means of deceiving the unsuspecting victim.
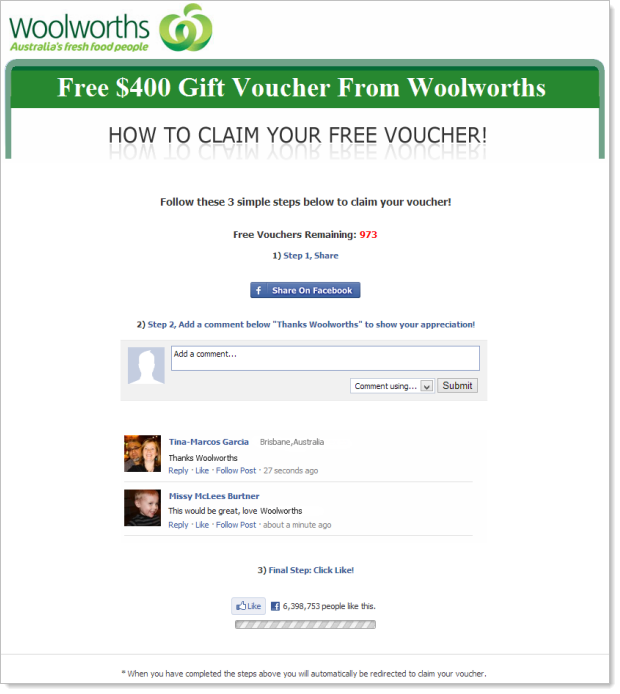
It all starts with a Facebook friend sharing a link to a page with the promise of free goods just like this:
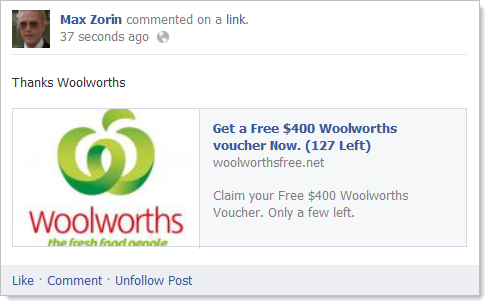
Which brings you to the website at woolworthsfree.net. Many of you reading this will click through to that link and end up at Google so let me start tearing this thing apart and explain what’s happening.
Detecting your potential scamability
The thing with most scams these days is that they have a terrible success rate. Yes, spam and other nasties “work” but it’s really only a very small percentage of them. When the king of Nigeria dies and bequeaths you $50M but only if you can help his grieving widow shift it out of the country, there’s this very, very small segment of the community which actually says “Hey, I could be onto something here”.
One thing this scam does right up front is detects your location and determines whether you’re likely to be sucked in by a Woolies scam or not. Here’s how the magic works:
Firstly, a JavaScript file is embedded from j.maxmind.com/app/geoip.js
Go ahead and click on that and you’ll see something along the lines of this:
function geoip_country_code() { return 'US'; }
function geoip_country_name() { return 'United States'; }
Of course this is just plain old JS with a method to return an abbreviated country code and another with the full name. It works by taking your IP address and dynamically resolving it to a physical location after which it’s embedded as a static string in the JS. It sits over on MaxMind which is a company offering a number of geolocation services.
With the country now known, the site implements a simple little bit of context switching:
var country = geoip_country_code(); if (country == "AU" || country == "AL" || country == "NZ" || country
== "ZA" || country == "CA") { } else { window.location = "http://google.com" }
In other words, if you’re not in Australia, Albania, New Zealand, South Africa or Canada it’s off to Google you go and you’ll never know what you’re missing (or not missing, as it may be). Albania? Maybe it’s one of those things like when some folks think Austria has kangaroos.
Regardless, the point is that this scam is only intended to entrap victims for certain target countries.
Creating a veil of authenticity
Let’s begin by dissecting the page which at present appears like this:
There are three sneaky things going on here. Actually, they’re three outright lies:
- There is a sense of urgency. There are a limited number of free vouchers and the number is counting down in real time!!! Quick – hurry before there’s none left and you miss out!!!
- Authenticity is established. There are two respectable looking everyday Facebook accounts who have commented on the page in the last minute (and they’re very appreciative).
- Popularity is massive. Over 6 million people like this page – it must be awesome!!!
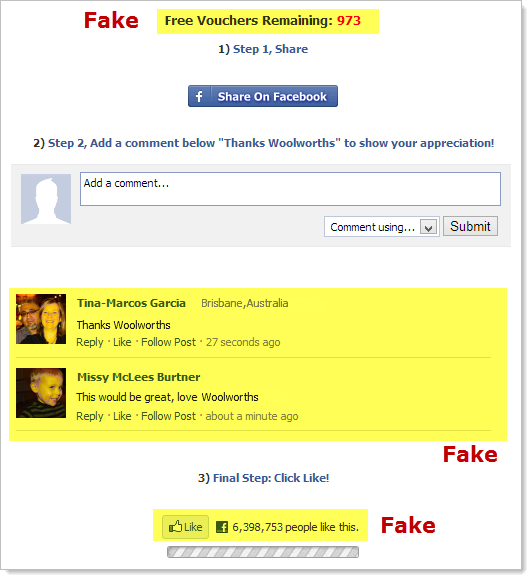
The reality, however, is very different:
Let’s start with the counter. The assentation is that there are limited vouchers and the unsuspecting victim can witness them being snapped up at a fierce rate. Actually, they’re being snapped up at an average of one every 2.5 seconds but we’ll come back to that.
The reality is much more mundane. The counter is an HTML tag which always defaults to 973:
<span id="count" style="color:red;">973</span>
Immediately after this is some JavaScript that calls a function called countChange:
<script type="text/javascript">/*<![CDATA[*/countChange();/*]]>*/</script>
You can probably guess where this is going – countChange is just client script to decrement the counter:
var start_count = 573; function countChange() { var a = Math.floor(Math.random() * 5); if (a == 1) { document.getElementById("count").innerHTML = start_count-- } setTimeout("countChange()", 500) }
Every half a second the script generates a random number that is between 0 and 5. If the generated number is between 1 and 2 then the number of remaining vouchers is decremented by 1. What it means is that the rate of other people snapping up vouchers doesn’t appear to be constant which adds to the believability of the whole scam.
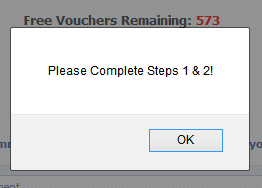
Mind you, all this this is after starting the remaining vouchers at 573 so what happens is that the page loads with 973 remaining (the value in the HTML) then immediately drops 400 then starts counting down. Oh – and because the remaining vouchers will keep decrementing infinitely you’ll eventually go into negative territory:
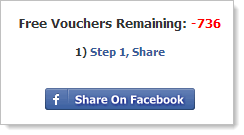
I guess they figure the victim would have given in to temptation by the time to counter zeroed out.
Next up is those other folks who love Woolies so much. Remember Tina and Missy?
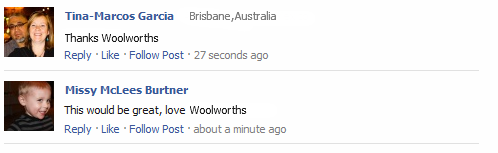
What you’re looking at above is the original image used on the page. That’s right, this isn’t a Facebook widget that dynamically displays the comments of users on the current page, it’s just a manually constructed image which is right here: i.imgur.com/ShlmE.png
And Tina? Well there is a real Tina but she’s a long way from Brisbane:
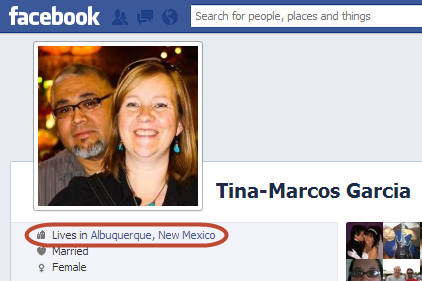
That’s one hell of a drive to get the groceries!
There’s also a real Missy albeit without a location on her profile:
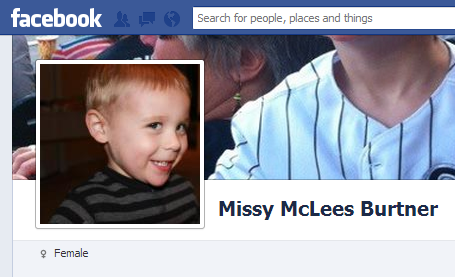
But what about the Facebook “likes”? Surely more than 6 million people can’t be wrong? It’s just another static image:
![]()
Here’s the original: i.imgur.com/RdWZB.png
“Falling for” the scam
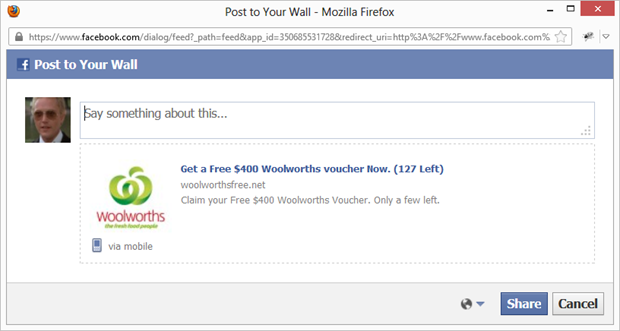
Enough analysis, let’s “fall victim” so we can understand the mechanics in their entirety. Clearly I won’t be using my personal account for this so I’ll pull out my old mate Max Zorin (the penny will drop for some of you) and use his instead. First of all, we needed to click the “Share on Facebook” link which will pop up a window just like this one:
The neatly formatted “share” page comes courtesy of some well-crafted Open Graph tags on the page:
<meta property="og:title" content="Get a Free $400 Woolworths voucher Now. (127 Left)"/> <meta property="og:type" content="website"/> <meta property="og:image" content="http://i.imgur.com/X28SG.jpg"/> <meta property="og:site_name" content="Woolworths Voucher Giveaway"/> <meta property="og:description" content="Claim your Free $400 Woolworths Voucher. Only a few left."/>
This is pretty usual behaviour, but there’s is a slight twist. The URL passed to the Facebook page you see above passes a “link” parameter in the query string such as woolworthsfree.net/?16tl5p42ibjef68
It’s not that this alone is unusual, but if you fire it up again you’ll get a slightly different ID at the send of the string, for example “pfthq95k1twhd6d”. This also isn’t that unusual for a legitimate site as it’s a means of tracking how many click-through come from a particular “share”, it’s just a little unusual to see it in a scam.
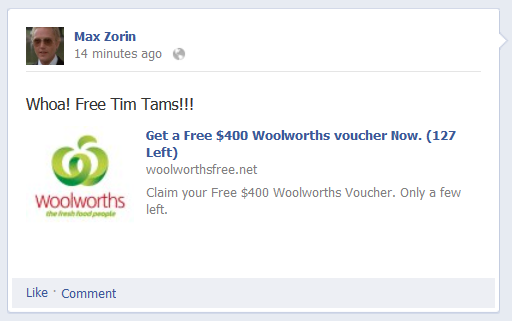
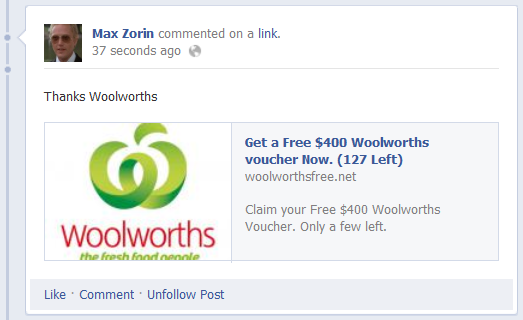
Sharing the page will do exactly what you think it will do and the Facebook timeline updates accordingly:
But there was one other thing that happened at the same time. When the document loaded, jQuery was used to register a click event on the “Share” button:
$("#postos").click(function () { $("#linkos").attr('href', 'offer.php'); });
Looking at the script, “postos” is the ID of the button and as you can see, it changes the href attribute of the “linkos” tag to “offer.php” once clicked. That tag is actually the “Like” button right down the bottom of the page.
As it turns out, this is the only activity with any functional value until we get down to the bottom but let’s humour the scammers and play by their rules.
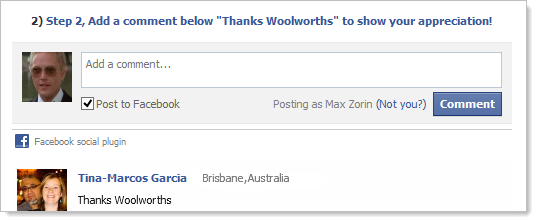
The next task was to write a comment on your own wall saying “Thanks Woolworths”:
Again, it does exactly as you’d expect:
Also again, there’s a unique ID in the link back to the scam so the tracking continues.
Finally there’s the “Like” button at the bottom of the page. We already know this isn’t a real button, there’s not really more than 6 million people who like it and the link has been set to “offer.php”. Incidentally, if you haven’t clicked the “Share” button earlier on, the default action of the like button is to pop up a JS alert:
Assuming we’ve played by the rules, the “Like” button then goes a bit nuts. There are many different possible routes this can take. Let me illustrate the trail of intrigue that unfolds (fans of website optimisation, hold onto your hats because this is going to get a bit bumpy):
Firstly, the “offers.php” page is requested and it responds with an HTML page which embeds the following JS:
if (country == "NZ") { window.location = "http://woolworthsgift.net/nz.php" } else if (country == "AU") { window.location = "http://bit.ly/UKV0cK" } else { }
This is after including that same geo location script from earlier so me being in Australia gets the bit.ly link. The request to the URL shortener is made and it responds with a 301 redirect to jmp.realtraq.net/aff_c?offer_id=9374&aff_id=7278
Going by the name, there’s some form of tracking going on here. Anyway, that link then responds with a 302 redirect to jmp.realtraq.net/aff_r?offer_id=9374&aff_id=7278&url=http%3A%2F%2Fadscendmedia.com%2Fclick.php%3Faff%3D11563%26camp%3D12589%26crt%3D24463%26sid%3D1020df6a2c1371f9187625970b18ae&urlauth=594321535690323592164546614378
Obviously this has another URL embedded in the query string but this time the page loads without a redirect header. However, it then embeds a meta refresh to jmp.realtraq.net/aff_r?offer_id=9374&aff_id=7278&redirect_pass=1&url=http%3A%2F%2Fadscendmedia.com%2Fclick.php%3Faff%3D11563%26camp%3D12589%26crt%3D24463%26sid%3D1020df6a2c1371f9187625970b18ae&urlauth=594321535690323592164546614378
Ok, so we then get a redirect to there which responds with another 302 (no, I’m not making this up!) to adscendmedia.com/click.php?aff=11563&camp=12589&crt=24463&sid=1020df6a2c1371f9187625970b18ae
So that page then loads and embeds another meta refresh, this time to adscendmedia.com/redir.php?goto=aHR0cDovL3RyYWNraW5nMS5hbGVhZHBheS5jb20vQWRUYWcvQ2xpY2svWTIxd2FXUTlNVEUzTmpJbWRITnBaRDAwTkRVZy8%2FZHA9MTE1NjNfMjQ4Nzc5Mzc1
That’s a redirect from the HTML and when that page loads it has an embedded JS script to do a window.location to tracking1.aleadpay.com/AdTag/Click/Y21waWQ9MTE3NjImdHNpZD00NDUg/?dp=11563_248779375
That page then responds with another 302 (oh c’mon!) and has the browser heading off to www.aldaniti.net/wingames/index.php?pk_campania=Njg1NQ%3D%3Dk9x&partner_param=
When that page loads it has another piece of JS in the HTML doing another window.location to www.aldaniti.net/wingames/apple_au/index.php
Believe it or not, that’s the end of the redirects. That’s 9 redirects all told, here’s the Fiddler trace:
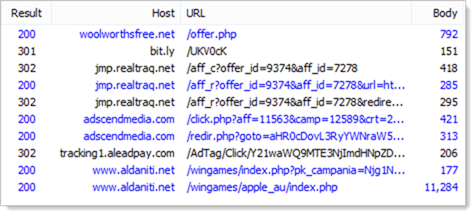
Or in timeline form:
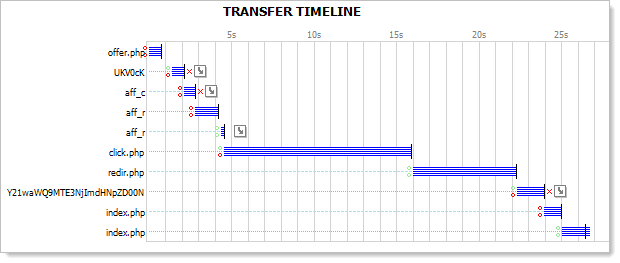
It’s 26 seconds worth of telling the browser to go somewhere else. Clearly website efficiency is not high on the scammers list of priorities!
Anyway, it all ends up on aldaniti.net where you can go off and win a shiny new Apple toy:
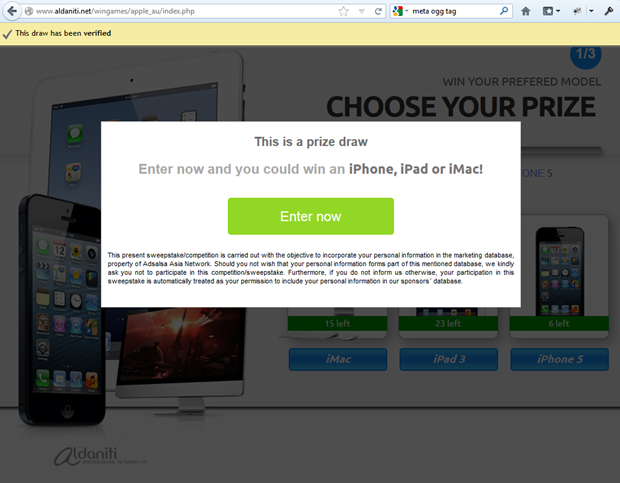
Hey – is it just me or does this look a little bit familiar?!
Hurry folks, there are only 6 iPhones left!
So what’s the deal with Aldaniti? A quick Google search will show there’s a high correlation between the words “aldaniti” and “scam”. These guys appear to have a history of sending out “you have just won something awesome” style junk.
Anyway, if you do click through to the “Enter now” option on the earlier screen then there’s a new popup and this time you’re winning a plasma – just leave your name, date of birth and complete contact details or in other words, a healthy starting point for identity theft:
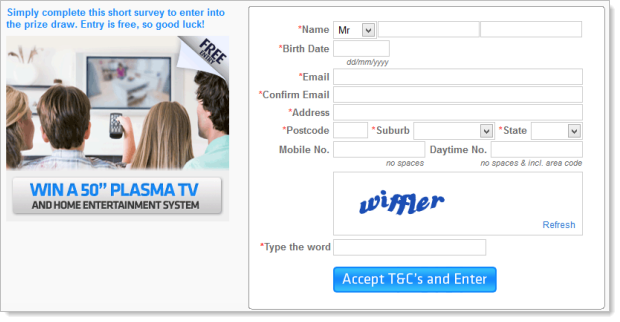
This is over on winatwingames.com.au so now we’re on an Aussie domain for the first time. So the form gets filled in with random rubbish and now there’s a bunch of survey questions about random, unrelated topics:
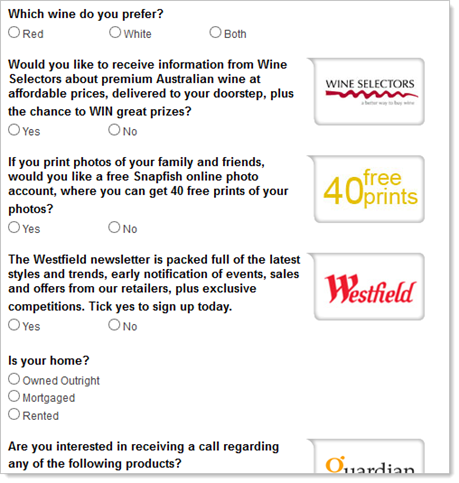
Problem is, you can’t scroll because the window that opened up from Aldaniti did so without scroll bars so you can’t actually get down to the submit button! No matter, arrow keys do the job so the form gets completed then submitted. Now it’s time for more surveys:
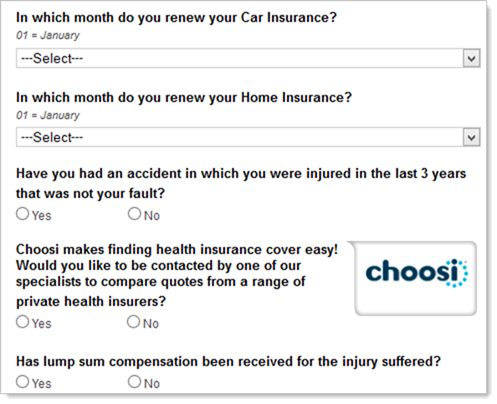
And then there’s another one. And then I ran out of patience. The number of redirects and conditions that seem to be set through the various steps above make it highly likely that not all victims will follow the same path of events. Apple toys from Aldaniti today, Samsungs from Acme tomorrow. It’s a tangled web of guerrilla marketing on top of scam.
You very quickly begin to feel like Alice falling down the rabbit hole but instead of a Mad Hatter and Cheshire Cat it’s redirects on redirects and surveys on surveys. Spend enough time clicking through and I reckon you’d find just about the whole internet passing you by. In fact the only thing I can guarantee you won’t find down there is a $400 Woolies voucher!
Customer outrage
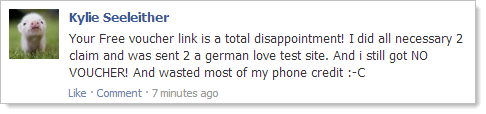
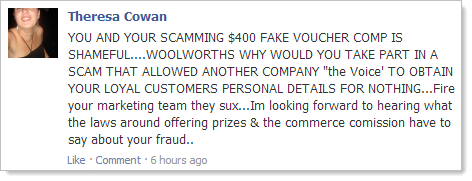
The problem for Woolies, of course, is that on the Facebook side this thing looks perfectly legitimate. If you go back to that image in the opening of this post, when someone sees this on a friend’s wall there’s no immediate alarm bells. What it means is that Woolies’ Facebook page is currently littered with comments like this:
German love test site?! How about this one:
You bastards, Woolies! In many cases such as Theresa’s in that last image, the post then turns into a mudslinging match with other people who are quick to point out the apparent stupidity of the scamee. Not what you want on your Facebook page.
Of course it would only take someone all of 5 seconds to establish that was indeed a scam in the first place:
Even our government's Stay Smart Online website warns about this specific scam. It’s also been on our news back in August and even made it to Gizmodo last week. Undoubtedly there are many different routes the scam can take, there would be more than one variant of it and almost certainly there are multiple other parties implementing similar scams.
Replicating the scam
Clearly these guys have had an impact. Not only has the scam been going for a few months but the “victim statements” on the Woolies Facebook page show it’s still ensnaring victims at a pretty successful rate.
So why stop there? I mean why just stop at Woolies? Good question, and a quick reverse DNS lookup reveals some familiar results. How about harveynorman.org:
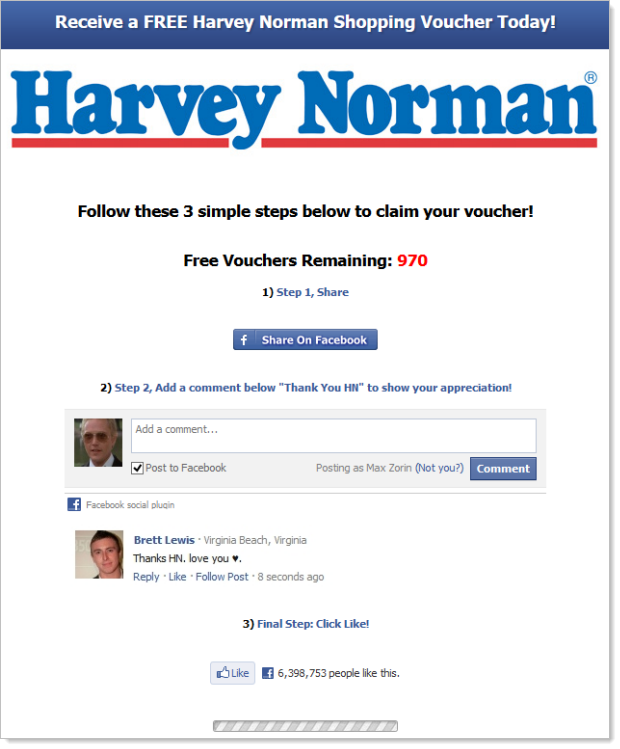
For international readers, Harvey Norman retails goods such as TVs, PCs and washing machines. Clearly the scammers are simply squatting on the .org domain and running the same sneaky game.
And here’s one for the coffee lovers at starbucksoffers.net:
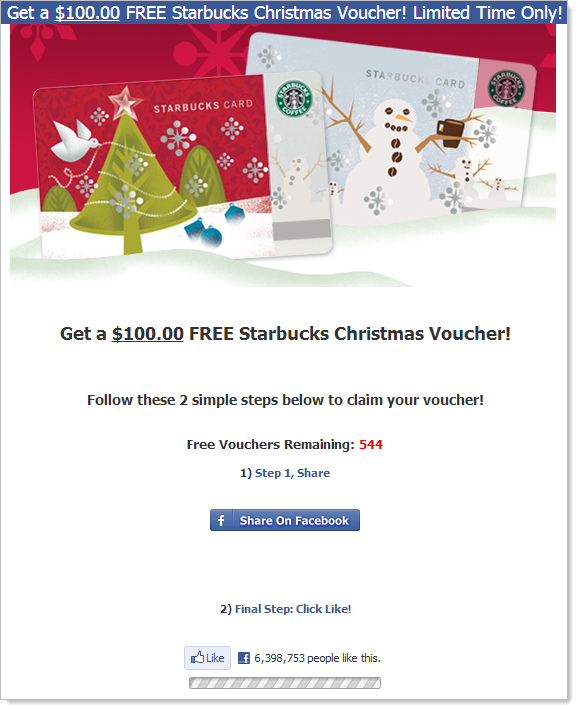
But wait – there’s more! How about a more US flavour at costcopromotion.net. Or there’s even freewoolworths.com which takes a new slant on the scam. I’m sure the list is far more extensive than this but by now I think you’re getting the point.
Tracking down the culprit
While we’re looking at DNS records, how about a quick WHOIS on the Woolies domain:
Administrative Contact: James Smith Lagja e vjeter tek pallati cope cope Elbasan, Albania n/a Albania ilovefbinfo@gmail.com +355 692207020
James Smith – sounds like a good Albanian name! And while we’re at it, where else have we seen Albania mentioned recently? Interesting coincidence.
As for that email address, it appears on WHOIS records as diverse as lolmyday.info to mywife.in to thashethemevip.com. That last one is in native Albanian language too…
Getting back to woolworthsfree.net, the site itself is bound to IP address 176.9.21.250 which is apparently owned by Hetzner in Stuttgart. Frankly, I’d prefer to continue thinking of Stuttgart being all about Porsches rather than scammers!
The geographic distribution is one of the reasons why these scams are so hard for authorities to get on top of. People in Australia being scammed by a guy in Albania using a server hosted in Germany. Who do the cops speak to? My experience talking with the authorities about the call centre scammers shows that things like this just get filed away in the “too hard” basket.
Conclusion
This ultimately amounts to no more than the last Facebook scam I analysed; a convincing con to suck you into filling out mindless crap that is somehow of value to some people that are willing to lie and cheat in exchange for your time. That value could be as innocuous as rewards for click through, ad impressions or survey completion but it could also be far more sinister in that it could relate to identity theft. Frankly, with the number of different permutations the scam could take it could well lead to all of these.
The last time I analysed a scam it was sex, this time it’s Woolies vouchers (an Harvey Norman vouchers and Starbucks vouchers and Costco vouchers). In each case the scam relies of the power of social media leverage by making the victim the advocate for the scam. It’s their wall that's telling all their friends how awesome the scammer’s page is.
In this case, the moral of the story is simply the old adage of “if it sounds too good to be true”. Seriously folks, you’ve got to do enough shopping at Woolies to feed a small nation before their loyalty card gives you even a few dollars benefit, does any reasonable person think they’re really going to start giving away $400 vouchers to random strangers?!