Another week, another breach. This time Yahoo! was the target with 453,491 email addresses and passwords from their Voices service being exposed for all to see. Whilst unfortunate for those involved, these breaches do give us some unique insight into password practices and as is usually the case, it’s not pretty.
Back in June last year after one of many Sony breaches I conducted a brief analysis and found a litany of bad password practices. Less than 1% of passwords contained a non-alphanumeric character, only 4% actually used more than two character types and 93% of passwords were between 6 and 10 characters long.
What made the Sony analysis particularly easy (and relevant) was that there was no cryptographic storage – everything was in the clear. You’d think that by now the big guys would have worked out that storing passwords in the clear is not on, I mean just look at the bad press LinkedIn got last month and they at least made a small attempt to hash them. Whilst the details are still sketchy, the early evidence is that Yahoo! kept their passwords in the clear and certainly the dump appears to support this with quite a number of “strong” passwords appearing in the breach and unlikely to have been brute forced, at least not without a very comprehensive dictionary.
I thought it would be interesting to take a quick look at what’s in this breach and the metric I was specifically interested in was prevalence of password reuse with the Sony breach:
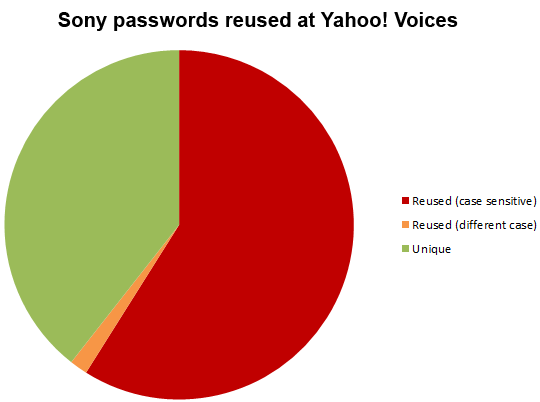
This probably shouldn’t come as a surprise – but it still did. More than a year after their accounts were breached on Sony, 59% of people were still using the exact same password on Yahoo! Voices. A further 2% were using passwords which differed only by case. This is from a sample size of 302 common accounts and unsurprisingly, the strength of those passwords leaves a lot to be desired:
03189500, 052385, 07182006, 102501Boo, 1albertw, 1fantom, 307722mp, 31315135, 31883188, 33487156, 399101nwm, 4boyzmom, 696969, 98760000, acoolmom, acting, aiden1, alkjsdfi9u, allied, Andover, apesfix, austin, avs4life, babygirl, Bakhos82, Bantha15, barnaby55, bearbear1, Beautiful1, benjiturtle, bestbuy66, bippy1, blonde42, brandi2, bruromg, bubby1, buddywade, cabana, casey123, catfish, ceaser, celibacy, chalantat, charbovari, Christina1, christmas07, chupibird, colleen, contest, cookie, crab67, creat1ve1, dani99, dexter, diaero35, diamond, dillon, electric1, EMASTE8, eternity, fernandes, frisky, gabby1, greats, hawaii, hendrix3, heybum, hitsalkali, horror, hRD71469, invent1, janmarie, jesse5, jimimac, joseph321, joshjoe, june0610, jwvM75pers, kayla123, kentucky, kickboxing, kimrip, kissma50, laughup, lexxus, lighthorse, llamas, Lonestar1, love13, lucky4, lynnette16, maciver, macpd202, maketea, mammals, margie, mattie24, mcdancer, mckenny1340, memaw1, mememe3, mingliu, monoder, munchkin, nancyjen, nepenthe, nirvana, nursing123, nylevE12, pandas, Passw0rd25, peaches, peanut, peepie, pfp462, philip, pittisit4077, plants, poinsettia, prancer, PRINCESS1, puddin, purple, rambling, rascal, rb112480, reiswade, richard916, ripper, rosebud, royals71, rutschke, sajoha82, sambo05, schniggy, scorpio, serene, skeeter, snoopy, sook11, sphinxster, stephen, Stingray, teacher, theblood, thomas, thomas1, tiger20, tipper, tooltool, TsugarBB, twosons8485, vetho123, victoria, village, vunhko, wachovia, webslinger, welcome, whole1, wilmat, windhaven, winner, winter, wolves, yamsy55, zgrizz, zoutia
We’ll see what comes out in the wash over the next few days, but chances are this may have been no more than a simple SQL injection attack. It’s a timely reminder for those of us building systems that strong hashing is essential (not the naked hashing which is frequently used) and for those of us creating online accounts (that would be all of us), that password uniqueness is always essential.